Update (March 24, 2020): This feature is now available for all Cognitive Intelligence customers.
Identifying cyber security threats in an organization is a necessary and non-trivial process. Fortunately, we can leverage machine learning algorithms to tap into the huge amount of traffic generated. These mathematical models have achieved high levels of sophistication and reliability that allow them to detect a wide range of anomalies, from early indicators of compromise to suspicious user behavior patterns, connections to domains or IP addresses related to attacks, and so on. When combined, all these pointers can give insights into active and ongoing malicious campaigns (due to the visibility that Cognitive Intelligence has through all the users and verticals) and provide security teams with prompt notification of attacks and tips on how to remediate the attacks.
Reasons behind the convictions
Predictions are powerful, but they are not enough. Security professionals need to know why a machine learning model has reached that conclusion and why it is important. In order to apply timely counter-measures that might limit connectivity for some users or other fixes, they need to have certainty and clear reasons for this verdict.
To achieve this, additional annotations are launching this week in the Cognitive Intelligence portal, providing new details for both confirmed and detected threats. Enroll for early access today!
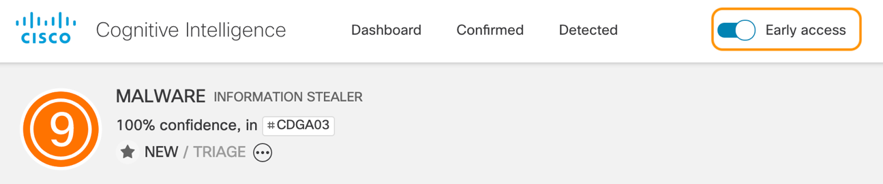
Figure 1: To see additional annotations in the Cognitive Intelligence portal, enable early access with one click from any confirmed or detected threat page.
These comprehensible descriptions are available in the anomalies section. They elaborate not only on the machine learning outcomes, but also the several layers of inference that are used to reach that verdict. Furthermore, they are displayed in a logical way to support the prediction.
These include information obtained by passive DNS, user statistics, details on the attack technique used, the capabilities and potential risks of the attack, specific triggers or IoCs that have raised the alarm, components of the Global Risk Map, and others.
If confirmed threats are identified, they are linked with the specific anomaly that set them off. This is especially useful when the event is related to several confirmed threats, since we are shown the specific trigger for each of them.

Figure 2: Bad actors often use domain names which are similar to legitimate ones in order to carry on their attacks. With the new annotations, a comprehensible anomaly description is provided.
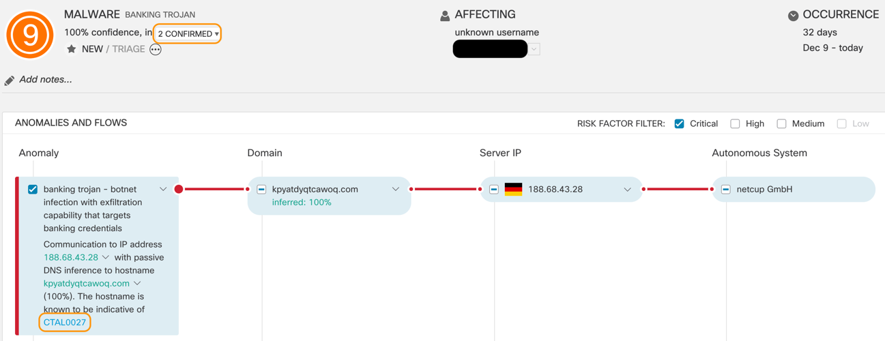
Figure 3: When an anomaly is related to a specific confirmed threat, the actions that led to identifying this specific threat are enumerated. The ID of the confirmed threat is also mentioned.
For Stealthwatch customers using the Cognitive Intelligence portal, most events currently have annotations, but not all of them. We will increase the coverage in the coming months.
Currently, the following anomalies are covered:
- Known malicious hostnames from passive DNS inference
- Known malicious hostnames
- Known malicious domains
- Known malicious IP addresses
- Stratum protocol communication
- Known Stratum protocol services
- Known Sality URL pattern
- RESP communication
- Uncommon executable download
- ICMP communication
- Large data transfer
- Typosquatted hostnames
- Punycode‐substituted hostnames
- Combosquatted hostnames
- Uniform and excessive external communication
- Excessive external communication Known TOR nodes
- BitTorrent communication
- SMB protocol communication
For customers that send proxy logs to Cognitive Intelligence, the following Anomalies are covered:
- Known malicious hostnames
- Known malicious domains
- Known malicious IP addresses
- Typosquatted hostnames
- Punycode‐substituted hostnames
- Combosquatted hostnames
Do you want to share your thoughts on this new addition to the Cognitive Intelligence portal? Click the feedback button to tell us what you like about the addition or what would be more helpful for you. We welcome your comments!
Figure 4: Click the feedback button to send us your comments about the Cognitive Intelligence portal.
Conclusions
It’s time for explanations in the machine learning field. The additional annotations supporting a specific detection put the threats identified by Cognitive Intelligence into context and help you understand whether they pose a risk to your organization.
This enables you to make informed decisions and address the hazards accordingly. At the end of the day, being able to understand the exact triggers of an attack provides you with trust in the results from our machine learning models and gives you .
Machine learning is evolving and so are our algorithms. The future is not only related to explainability, it’s also prescriptive. Stay tuned for more blog posts about innovations in Cognitive Intelligence!
