As part of the Cisco Common User Experience program, we are working towards a more uniform user experience and terminology alignment. This program runs across all Cisco security products.
A More Intuitive Cognitive Portal Design
In this release, we have redesigned the portal header, menus, and certain colors schemes to match the rest of the Cisco Advanced Threat portfolio.
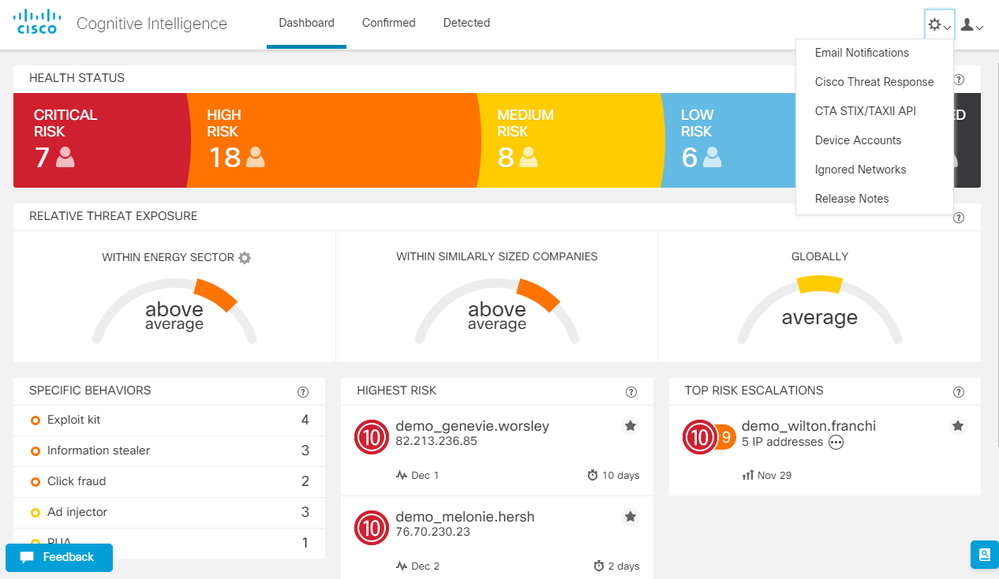
Redesigned header and menus in the Cognitive portal
Direct Feedback from the Cognitive Portal
Apart from the typical support channels that Cisco already offers, the Cognitive portal now includes a button that you can click to provide feedback directly to the Cognitive product team . This feedback can be anything from a feature request to a specific issue with the portal or an individual detection. You also have the option to leave your contact information for a follow-up.
Please note that this feedback is provided directly to the Cognitive product team and researchers in order to improve the capabilities of Cognitive. It is not a channel to request formal technical support. In order to obtain technical support according to Cisco SLAs, please open a case with Cisco TAC.
Feedback button on the Incident Detail page
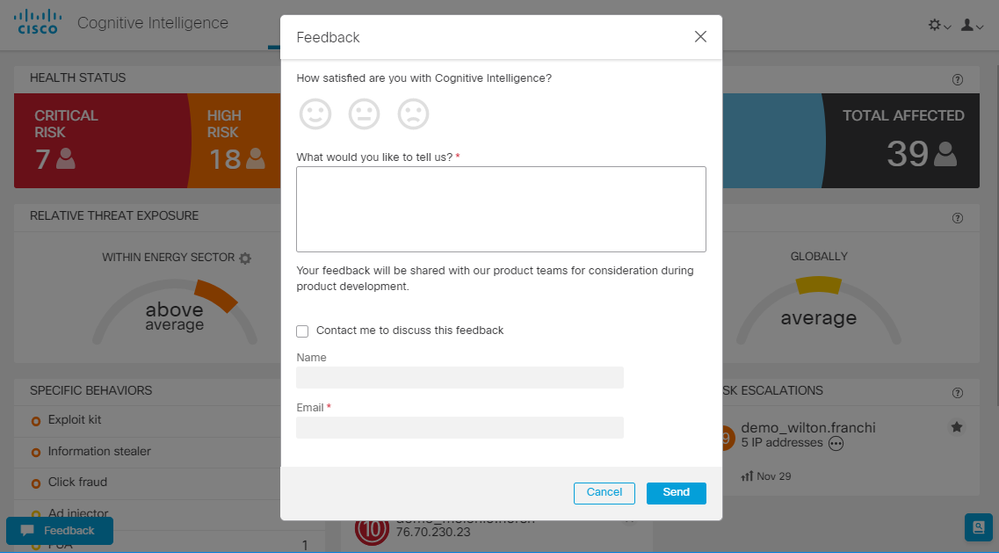
Feedback pop-up window
New Confirmed Threats
List of new Confirmed Threat types in November:
|
Confirmed Threat ID
|
Name
|
Category
|
Risk
|
Description
|
|
CTAL0161
|
Quasar Remote Access Trojan (RAT)
|
Malware Remote Access Trojan
|
Critical
|
Quasar gives the attacker complete remote control and administration of the infected device.
|
|
CTAL0154
|
Tinba Trojan
|
Malware
Trojan
|
High
|
Threat related to the Tinba Trojan, that possesses rootkit capabilities, machine-dependent encryption and uses man-in-the-middle attacks to steal banking information.
|
|
CTAL0193
|
TeslaCrypt
|
Malware Ransomware
|
Critical
|
Threat searches for specific files on local, remote, removable, and mapped drives. It also searches un-mapped network shares and encrypts all of them, demanding a payment as a ransom to decrypt them
|
Leveraging Cognitive Intelligence
Cognitive Intelligence capabilities are available to AMP customers with a compatible web proxy such as the Cisco Web Security Appliance, and all Stealthwatch Enterprise customers. Reach out to your account executive to learn how to turbocharge your existing cybersecurity investment with Cognitive.
