Terminology Updates
We are aligning the terminology used in the system across Cisco and the network security industry. As a result, these changes have been implemented:
- Activities are renamed to Anomalies
- Severity of Activities is renamed to Risk Factor
It varies from 1 to 9, and now it will also be categorized as low – medium – high - critical, represented in different colors:
Low (blue) for 1 to 5, medium (yellow) for 6 to 7, high (amber) for 8 to 9 and critical (red) for 10.
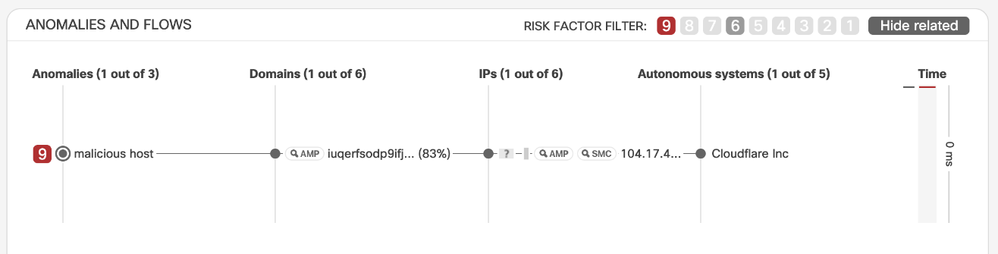
Updated Terminology in the Incident Detail
- Permanent Filter is now Ignored Networks
The functionality to exclude some IP addresses or subnets from the list of incidents is improved and renamed from Permanent Filter to Ignored Networks.
The alerts for hosts matching the configured subnets will also be excluded from reporting in AMP for Endpoints, Stealthwatch, and STIX/TAXII feeds.
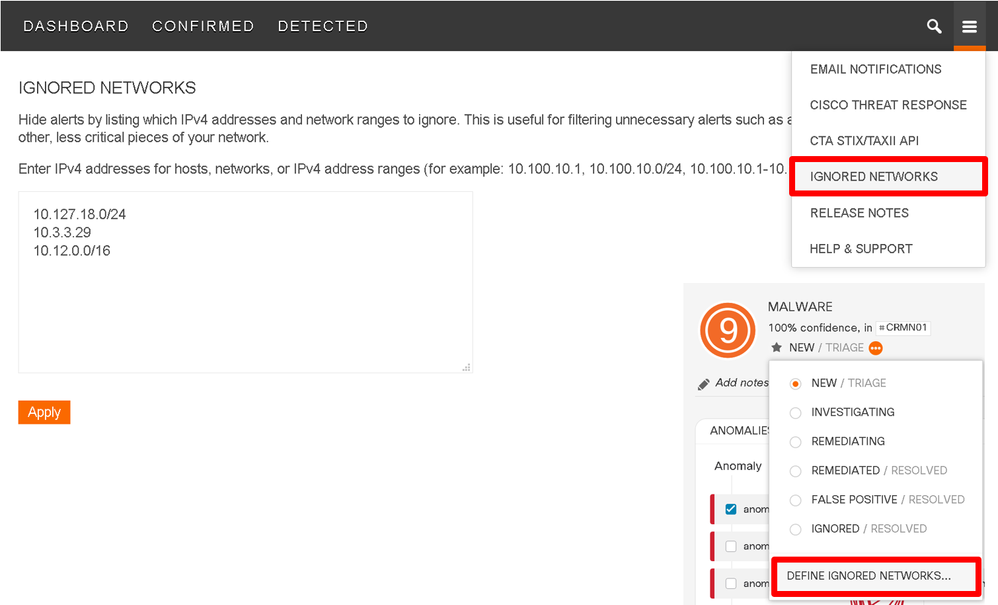
Ignored Networks Configuration
New features
The Cognitive UI now offers Casebook – a small widget that allows for submitting of observables directly to Cisco Threat Response. More details on Casebook can be found in the following blogpost: https://blogs.cisco.com/security/cisco-visibility-casebooks-saving-you-time-when-you-need-it-most
You can enable Casebook using the icon or in the Cognitive Threat Response menu.
Better support for moving indicators from the page to Casebook will be improved in subsequent releases.
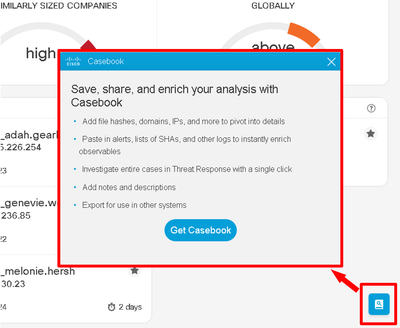
Casebook Enablement
New Confirmed Threats
In August and September, we added to our growing list of machine-learning-powered Confirmed Threat detections provided by the Cognitive Intelligence engine. We added two net-new Confirmed Threat types (see list below) and increased detection rates for previously-existing Confirmed Threats in the past six months.
List of new Confirmed Threat types in August and September:
|
Confirmed Threat ID
|
Name
|
Category
|
Risk
|
Description
|
|
CTAL0194
|
Phorpiex
|
Malware - Dropper
|
High
|
Phorpiex infects machines to deliver follow-on malware. Phorpiex has been known to drop a wide range of payloads, from malware that sends spam emails to ransomware and cryptocurrency miners.
|
|
CTAL0236
|
Parite
|
Malware - File Infector
|
High
|
The Parite virus is a polymorphic file infector that resides in memory and attempts to disable antivirus solutions. It infects executable files on the local file system and on writeable network shares. Generally classified as a high-risk threat.
|
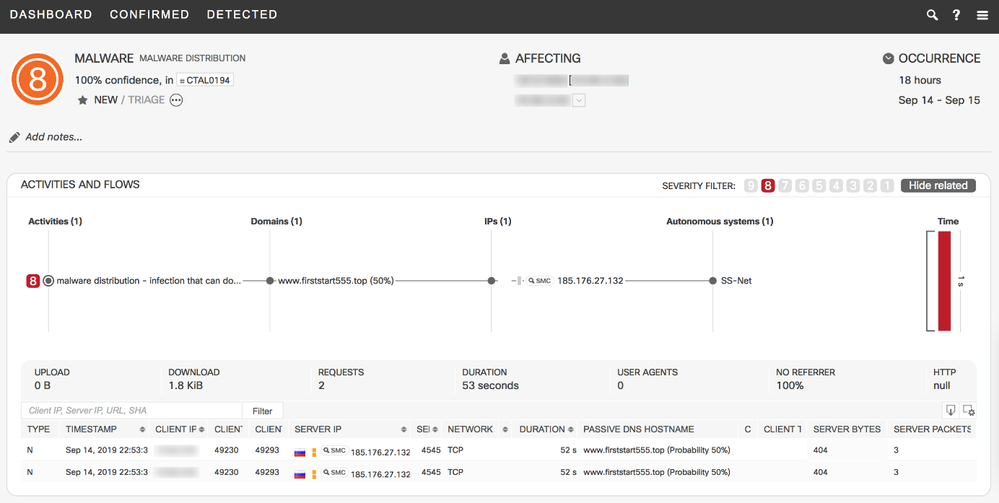
Sample Finding of new Confirmed Threat CTAL0194 Phorpiex Trojan
Confirmed Threat Updates
Our semi-automatic Indicator-of-Compromise (IoC) hunt processes (see Machine Learning Backend Improved blog) allowed us to increase the IoC coverage of existing Confirmed Threats. In August and September, we observed the re-emergence of the Emotet trojan (see Talos blog) and accordingly identified 97 new IoCs. In total, we added more than 600 high-risk IoCs and 40 mid-risk IoCs, covering over 20 different Confirmed Threat types.
Leveraging Cognitive Intelligence
Cognitive Intelligence capabilities are available to AMP customers with a compatible web proxy such as the Cisco Web Security Appliance, and all Stealthwatch Enterprise customers. Reach out to your account executive to learn how to turbocharge your existing cybersecurity investment with Cognitive.
