This blog extends information from Cognitive Threat Analytics (CTA) Release Notes.
January 2018 Update
CTA Engine now detects new types of incidents:
- repetitive and persistent cryptomining activities on the endpoint
- in-browser cryptomining by websites
Cryptomining infections may not necessarily constitute a threat, but they do cause non-negligible financial harm by excessive consumption of computing resources. Detected incidents can signify either cryptomining infection or voluntary misuse of company resources.
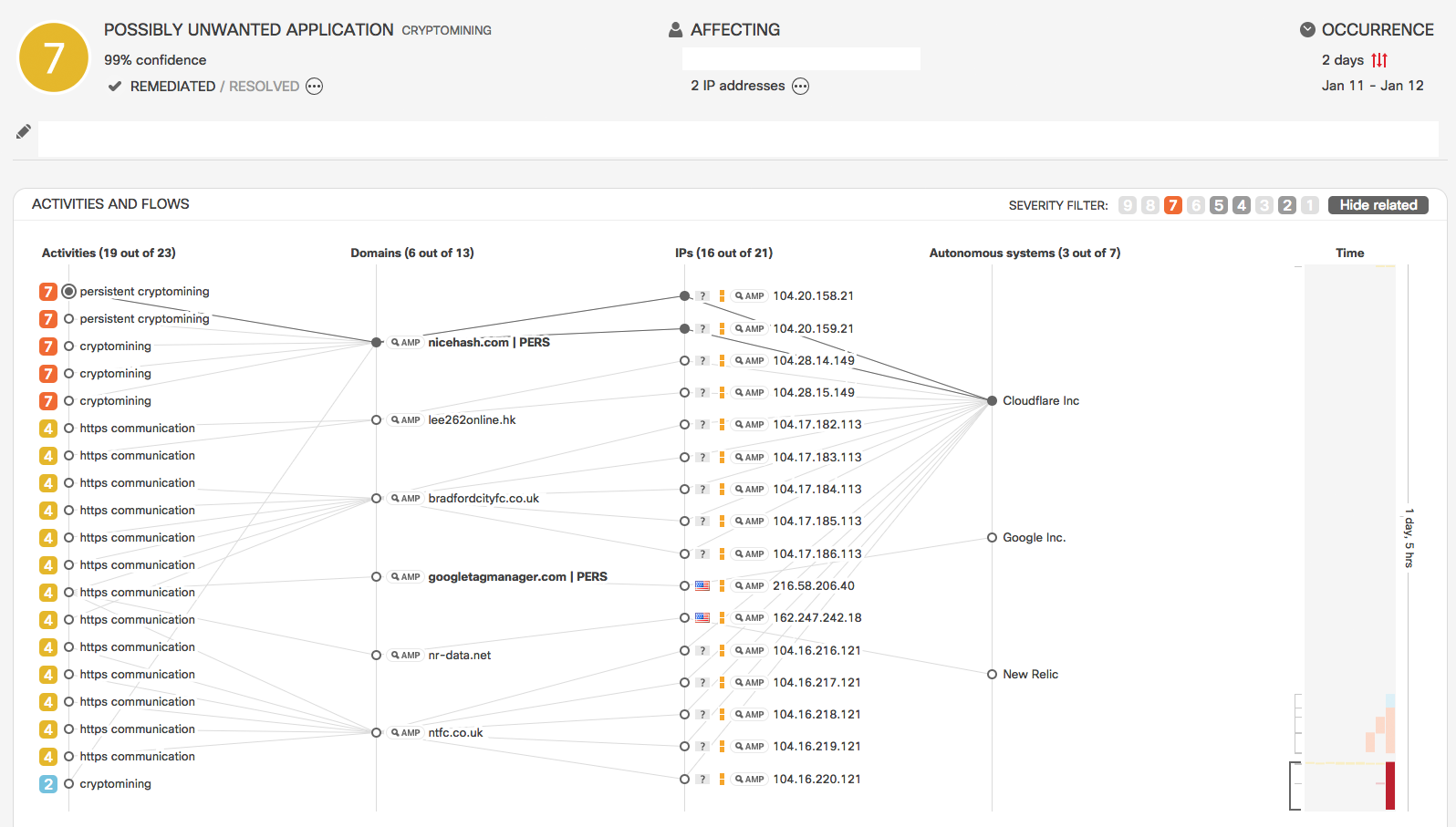
Example: In this incident CTA alerts about repetitive communication with cryptomining pools. The endpoint exhibits persistent communication with nicehash.com, what adds to the conviction that cryptomining activity takes place on the endpoint.
