This blog extends information from Cognitive Threat Analytics (CTA) Release Notes.
November 2017 Updates
- Advanced Detection from Encrypted channels
- ETA Analytics. New and updated algorithms that use ETA features in StealthWatch-flows to detect: Malware families Cryptowall, Sality, and Ramnit, Malicious file download, Phishing, DNS sinkhole, Vulnerability scanning, Typo-squatting, Unicode typo-squatting. Note that CTA support for ETA works specifically for customers providing StealthWatch-flow telemetry. For customers providing ProxyLog telemetry CTA now provides HTTPS-based detection capability (see next item)
- Detection from HTTPS telemetry without decryption. From now on CTA provides industry-unique technology allowing to detect multiple infection types in HTTPS channel without decryption. The technology is the result of year-long research effort motivated by the fact that the increasing adoption of encryption across the Internet may diminish capabilities of industry-standard detection techniques. CTA makes the most of combining and correlating multiple very weak indicators available in HTTPS telemetry.

Example 1: Here the HTTPS classifier attributed the https communication to the ad injector activity. Connection to server is not shown as successful to cause harm, nevertheless the client node is clearly infected.
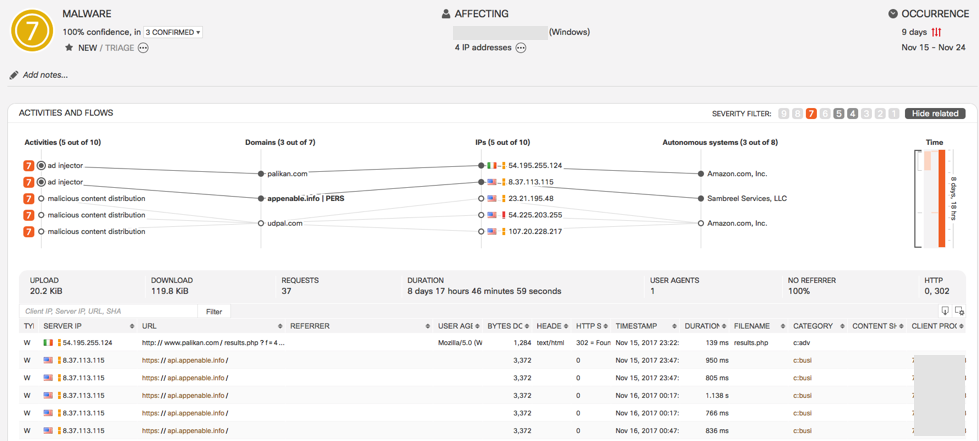
Example 2: Note the https flows in the bottom, that in this case proved sufficient to trigger the incident.
