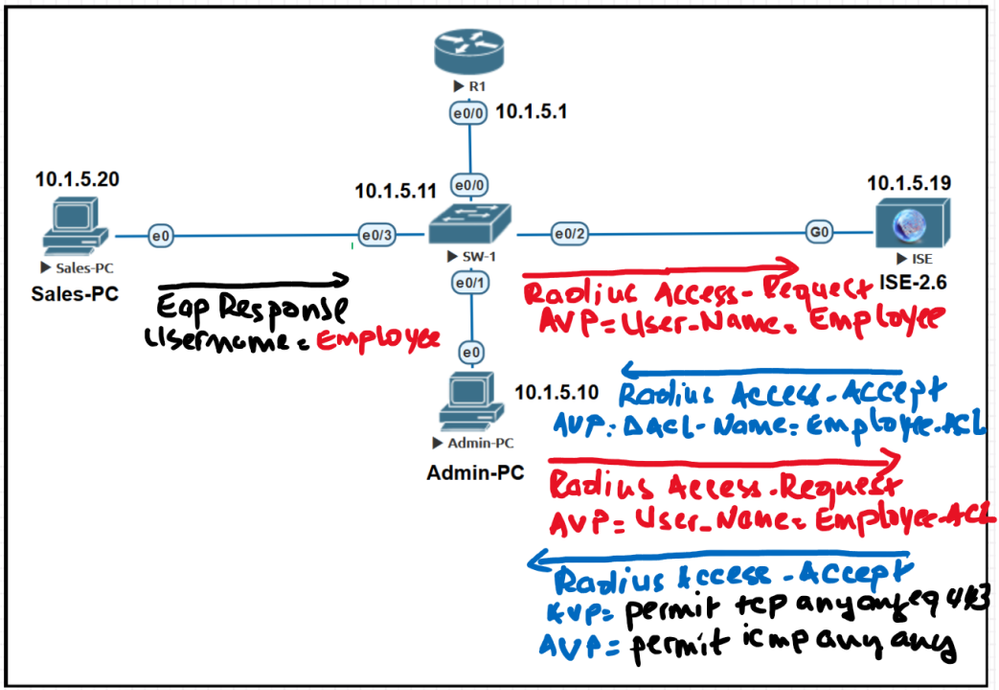
The 802.1X protocol is basically a method to control the network access for users, authentication with a username and password, and authorization using a Dacl or VLAN assignment for example.
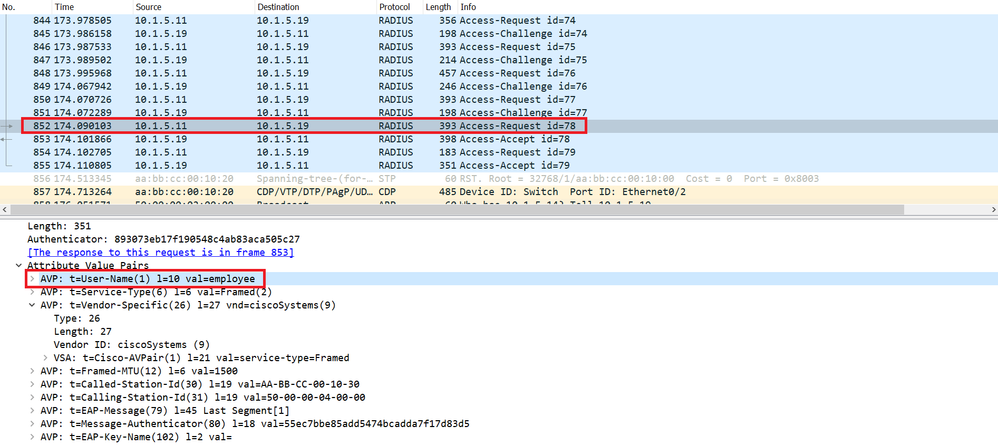
The PC sends a EAP-Response message providing the username, for example “Employee” in this case, the NAD or the Switch encapsulates the EAP message in Radius Packet and sends a Radius Access-Request packet to Cisco ISE. This Radius Access-Request contains the Attribute Value Pair “AVP” “User-Name”=employee.
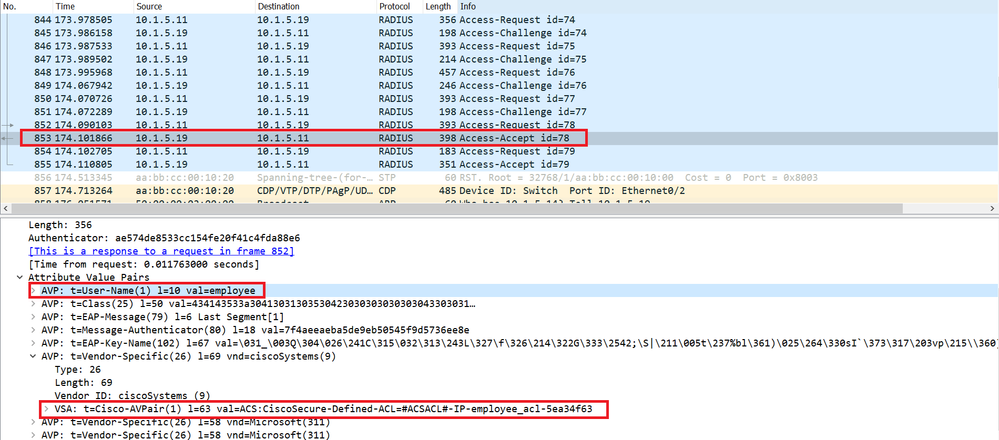
The Cisco ISE based on the credentials (Employee), validates the authentication using an authentication policy and based, let’s say the group the username employee belongs to, provide authorization using an authorization policy, in this case the authorization is provided through a Downloadable ACL called Employee-acl.
The Cisco ISE sends a Radius Access-Accept packet as a response to the Radius Access-Request originated by the Switch.
This Radius Access-Accept packet contains the Cisco-AVP (Attribute Value Pair Attribute) with the Value=employee_acl, to tell the Switch which ACL it should apply to the user Employee.
In the Wireshark capture below, we can see that the Cisco ISE does not provide the content of the Dacl, in other words the ACE entries. It provides only the name of the Dacl.
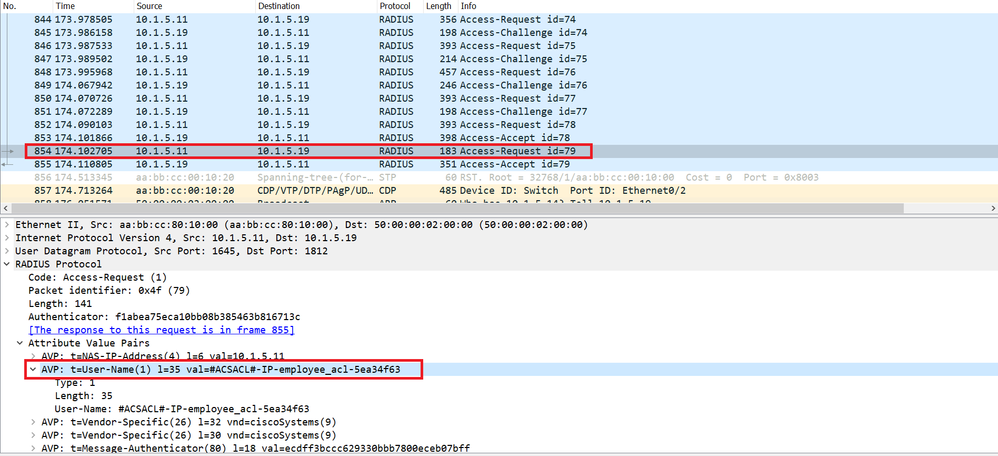
Then the Switch generates and sends a Radius Access-Request . This Radius Access-Request contains the Attribute Value Pair “AVP” “User-Name”=employee_acl, the Switch tells the Cisco ISE, OK I dont have a locally configured ACL with the same name, can you send me the content of the ACL named employee_acl?
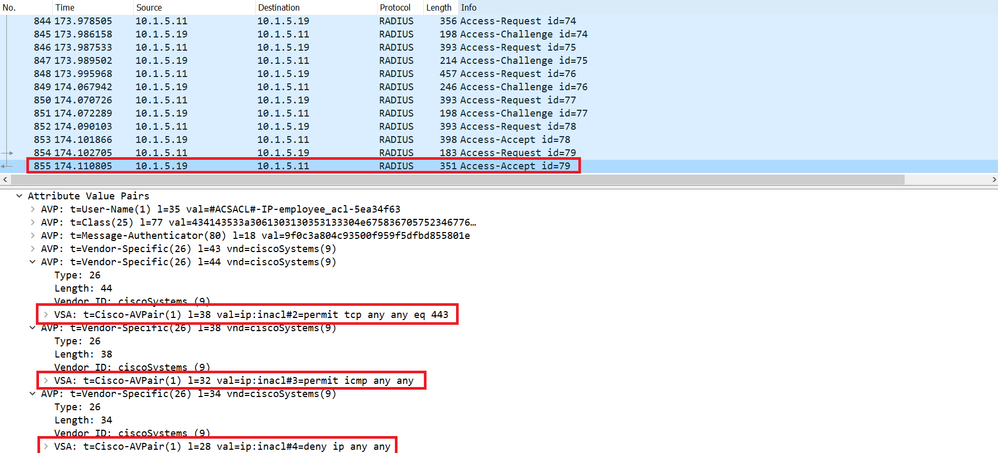
Finally, the Cisco ISE sends a response through the Radius Access-Accept with the content of the Dacl as shown below, with the ACEs entries: permit tcp any any eq 443, permit icmp any any and deny ip any any.
Conclusion:
The Cisco ISE does not push the entire Dacl with the ACEs once it receives a Radius Access-Request from the NAD for user authentication, instead it sends a Radius Access-Accept including just the name of the Dacl and without the ACEs.
The Cisco ISE will wait the switch to send another Radius Access-Request but the “User-Name” attribute contains only the name of the ACL, the purpose is to request the Cisco ISE the details (ACEs) of this Dacl.
