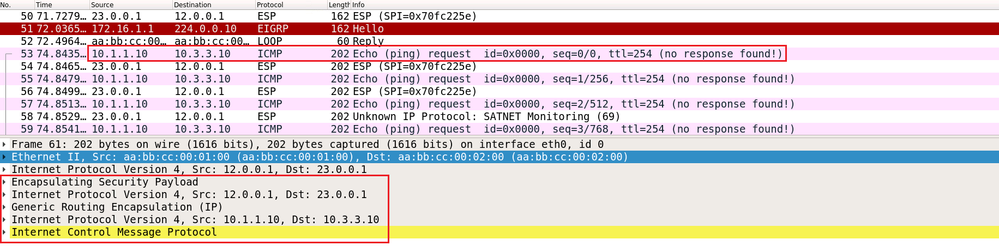
Sometimes you want to see how the tunnel and the transport modes works with encapsulation, especially when using GRE over IPSEC and you would like to decrypt the ESP or IPSEC packet to see how GRE packet is encapulated with the two modes, especially for studying , teaching or may be for troubleshooting.
Below how to do it:
Configue the ESP encryption with null in the transform set.
crypto ipsec transform-set TS esp-null esp-sha512-hmac
Copy the pre-shared key configured in phase 1 ISAKMP.
crypto isakmp key CISCO address 23.0.0.1
Open wireshark. right-click on the ESP packet, in this scenario the ESP SA from the source 12.0.0.1 to the destination 23.0.0.1. Under the Protocol Preferences, check the three options shown below.
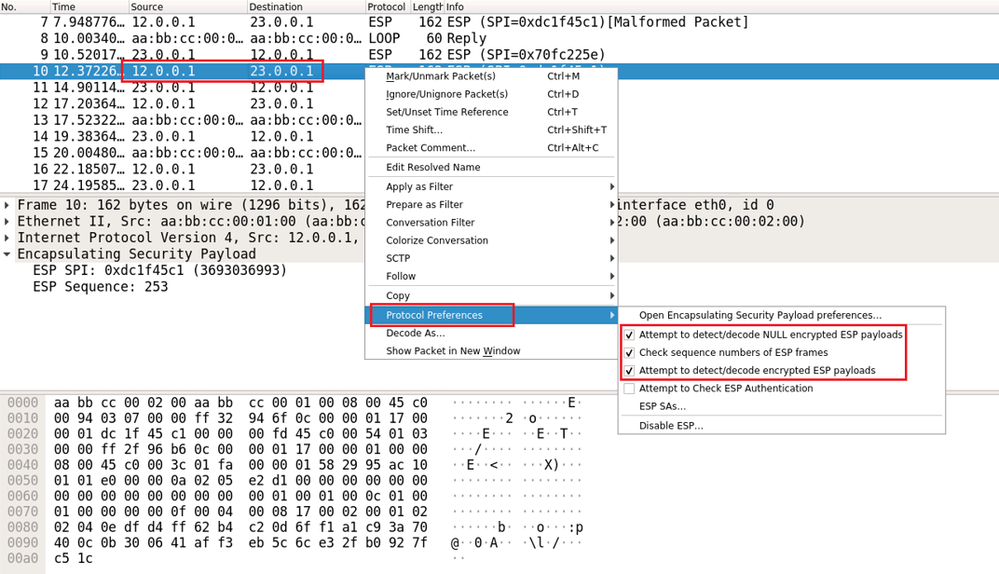
Expand the Encapsulation Security Payload and copy the SPI value for this ESP SA.
0xdc1f45c1
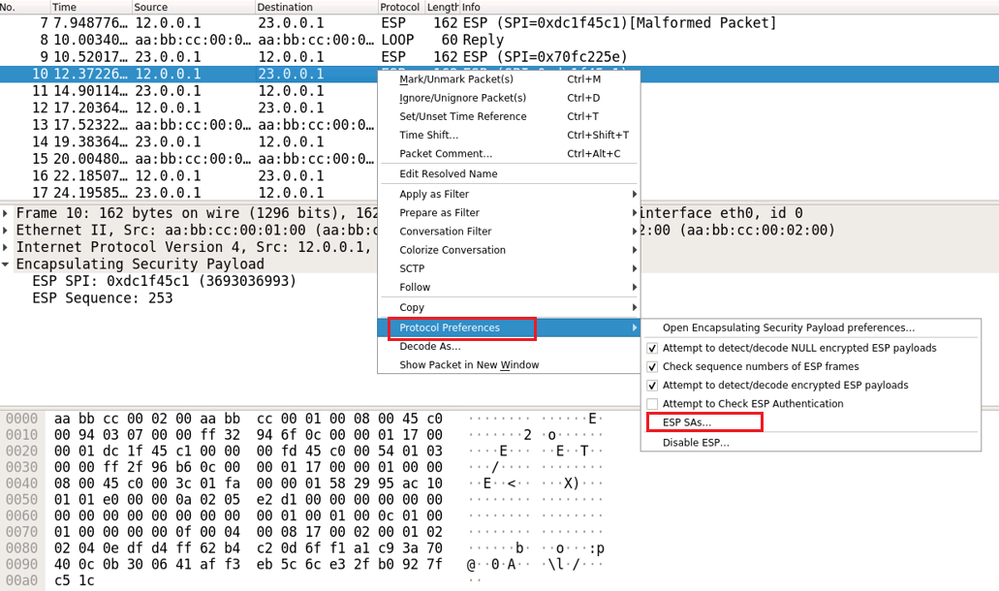
 Go back to Protocol Preferences, click on ESP SAs.
Go back to Protocol Preferences, click on ESP SAs.
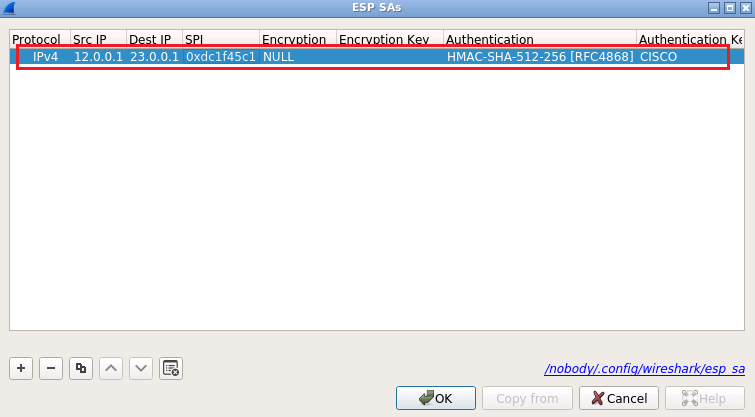
Enter the informations related to the ESP SA.
Protocol: IPv4
Src IP: 12.0.0.1
Dest IP: 23.0.0.1
SPI: 0xdc1f45c1
Encryption: NULL
Authentication: SHA512-hmac-512-256 [RFC4868]
Authentication Key: CISCO
Click OK, you should see the IPSec packet in clear text.