Everyone is digitising, everyone is enabling connectivity, everyone is pulling data from device’s we deemed not possible. Why? For a range of reasons, automation, data intelligence, predictive maintenance and efficiency to name a few. As you can image there is a whole host of heterogeneous devices from all verticals, sensors, HMI’s and PLC’s in manufacturing all the way to ECG machines, X-ray machines and CT Scanners in healthcare all connecting in many different ways. At the same time devices being brought online are either legacy or new, without any security built-in due to the functions of the device.
Once connected to the network this device is now vulnerable coupled with no visibility. To make matters worse legacy devices present even more of a challenge as they are too old to update but very valuable to keep in operation, for example in the manufacturing vertical it’s not uncommon to find devices over 20+ years in operation.
Cisco’s IoT Threat Defence can help with this challenge.
Segmentation is one of the four key pillars in IoT Threat Defence solution and is compromised of the following Cisco products,
• Next Generation Firewall
• Identity Services Engine
• TrustSec
The US Department of Homeland Security, National Security Agency, international defense agencies, and leading Network publications and analysts recommend network segmentation to limit the scope of a compromise and reduce the extent an adversary can move across the network. This also becomes the only point where the device can send inbound and outbound traffic giving us visibility via the segmentation.
The NGFW is the answer to provide both safety and security to your network modernization projects. It also provides the anchor point for converging IT and OT security visibility without interfering with operational practice.
Our ruggedized ASA 5506H-X is ideal for harsh or hazardous conditions. The 60 Gigs of storage has been thermal tested to withstand the heat of industrial environments.
As well as the ISA 3000 ruggedized appliance that provides the widest range of Access, Threat, and Application controls.
The ISA 3000 industrial firewall can fulfill security requirements associated with a variety of industrial standards, regulations, and guidelines such as: NERC-CIP, ISA 99, ISA 62443, CFATS, ANSI/AWWA G430 and others.
Managed through either a user-friendly on-box system manager or companywide security management, the ISA 3000 provides industrial focused, out-of-the-box configuration and simplified operational manageability. These highly customizable management options allow for simplified local operational awareness and higher order IT/OT security convergence for the inevitable mix of industrial and IT capabilities.
In reality, you have many different types of users and devices accessing onto the network. The devices need access, perhaps only temporarily, to certain network resources in order to execute a process effectively and efficiently.
ISE collects contextual data from the network (like DHCP, NetFlow, etc.), the type of device, and the user identity (e.g., from Active Directory) and pulls that information in.
It also collects context from integrated partners when evaluating posture or compliance.
Now, with a contextual identity established, ISE is able to bring together these disparate pieces of data to a single location and make a more fully-informed decision regarding access.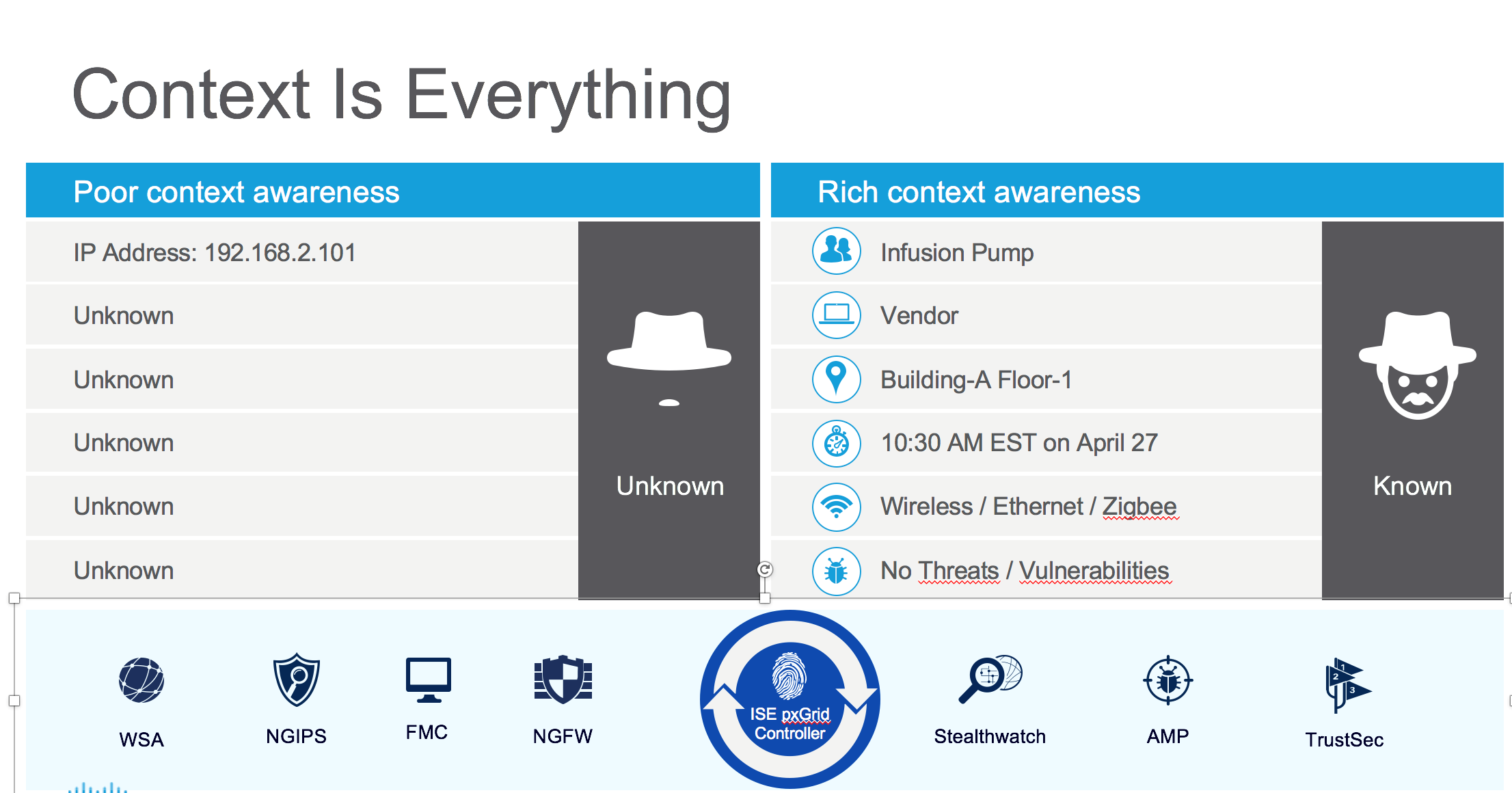
Here, the device an infusion pump may get access to send information to a nurse’s console in an intensive care unit, but obviously not to the Enterprise Medical record server.
The third and final step is TrustSec, Segmentation with TrustSec is managed centrally (ISE being the orchestrator of TrustSec) and scales for the world of IoT, which is exactly what you need with the billions of devices and growing. It provides you with a true topology-independent segmentation architecture that is easier to maintain and manage. By creating logical security groups based on the role of a device, there’s no need to provision ACLs for each individual, device, and destination on the network. With TrustSec-capable network devices, your business can benefit from segmentation without requiring VLANs, without dependence upon address space in a process that is transparent to endpoints. As rules are based upon meaningful groups, they are easier to understand and can be applied automatically.
In summary, how does this all work:
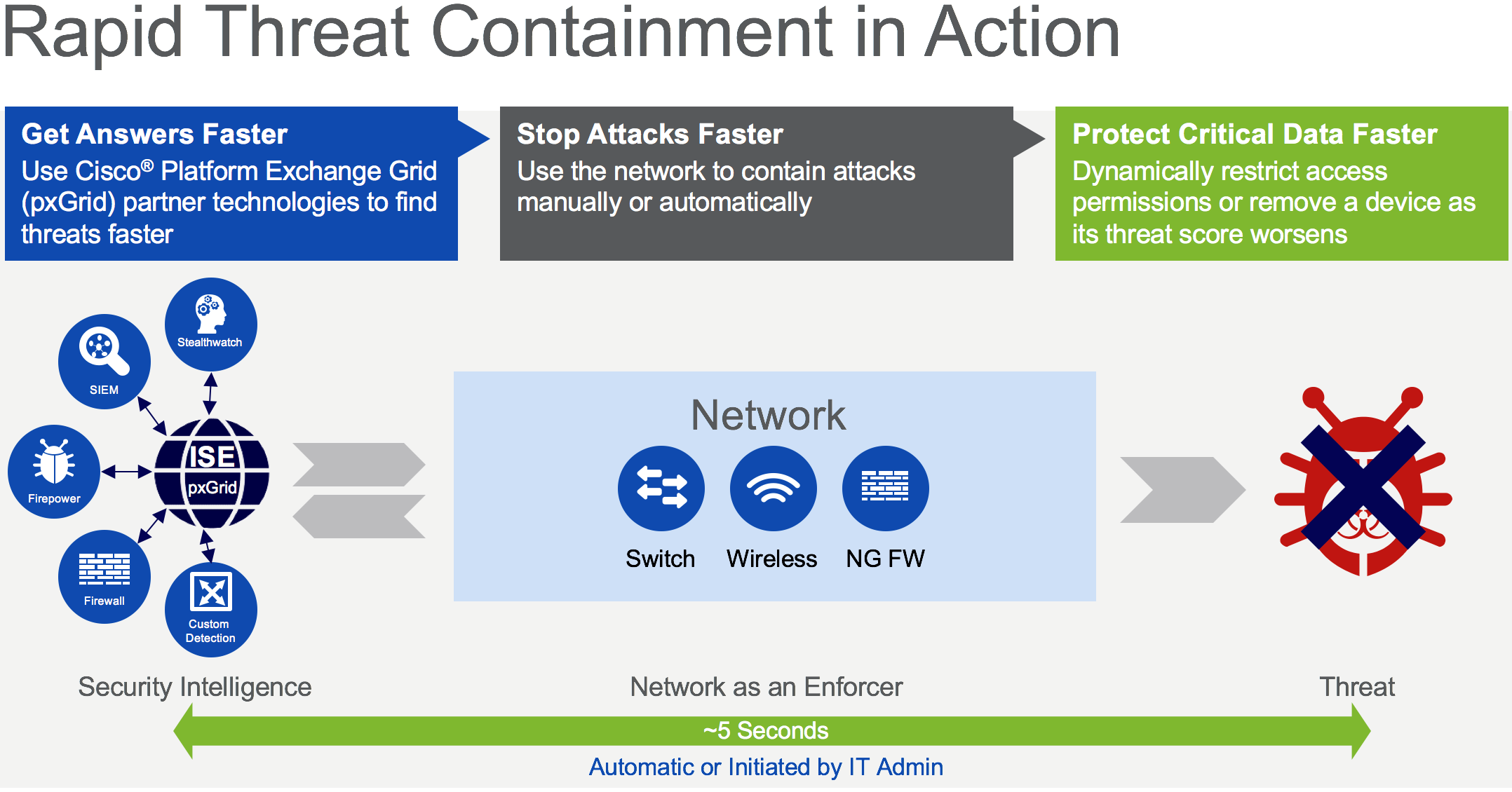
Multiple security technologies share data via pxGrid so the Security admin can get answers fast. Once the attack is recognized the admin can push the kill button to start the process of an infected device – either with a change of authorization (COA) to a benign VLAN (perhaps for sandbox, quarantine or mitigation (Depending on company preference) or assigns it to a TrustSec security group. So, we can stop the attack quickly. If a device is infected and acts suspicious but not malicious then we can move the device into a VLAN or security group where they can’t threaten critical resources, but still do most of their work.
|
Join me for an upcoming technical deep-dive briefing on IoT via the Customer Connection program. The session will be on July 26, 2017 from 8:00-9:30am PT. All you need to do is register for the Security track of the Customer Connection program here: www.cisco.com/go/ccp. In the meantime, please join feel free to ask me any questions regarding this announcement.
|
