Overview
I was just recently asked how to do ISE BYOD (Bring Your Own Device) without the need for Native Supplicant and/or Certificate Provisioning.
This request was for a healthcare customer that wanted their staff to register their personal devices and to also limit how many of these devices can be registered for access to the network. This also give their users the ability to manage their devices via the My Devices Portal by adding in lightweight devices (such as kindles with a limited browser). They can also delete a device if they no longer are using it or blacklist it if its stolen or lost.
They weren't ready to start getting into Certificates which is the recommended way to deploy BYOD as it provisions a unique credential per device. If its lost you can revoke the certificate through the My Devices or admin portal(s). They were aware that if a device was lost they would need to have the helpdesk reset their user AD credentials.
Here is a basic write-up on how this is done with ISE 2.x:
This is the setting that is used to not require an NSP under CPP. You don't need to do any configuration under CPP.
You could also use this for supporting devices that support Native Supplicant provisioning (windows, OSX, iOS and Android) by adding in CPP rules for those OS they would go through PEAP > EAP-TLS or OPEN > EAP-TLS (this would require config mentioned in design guides site) but for devices such as Windows Mobile or Blackberry would still be allowed access as registered only and would use the rules below.
Administration > System >Settings > Client Provisioning
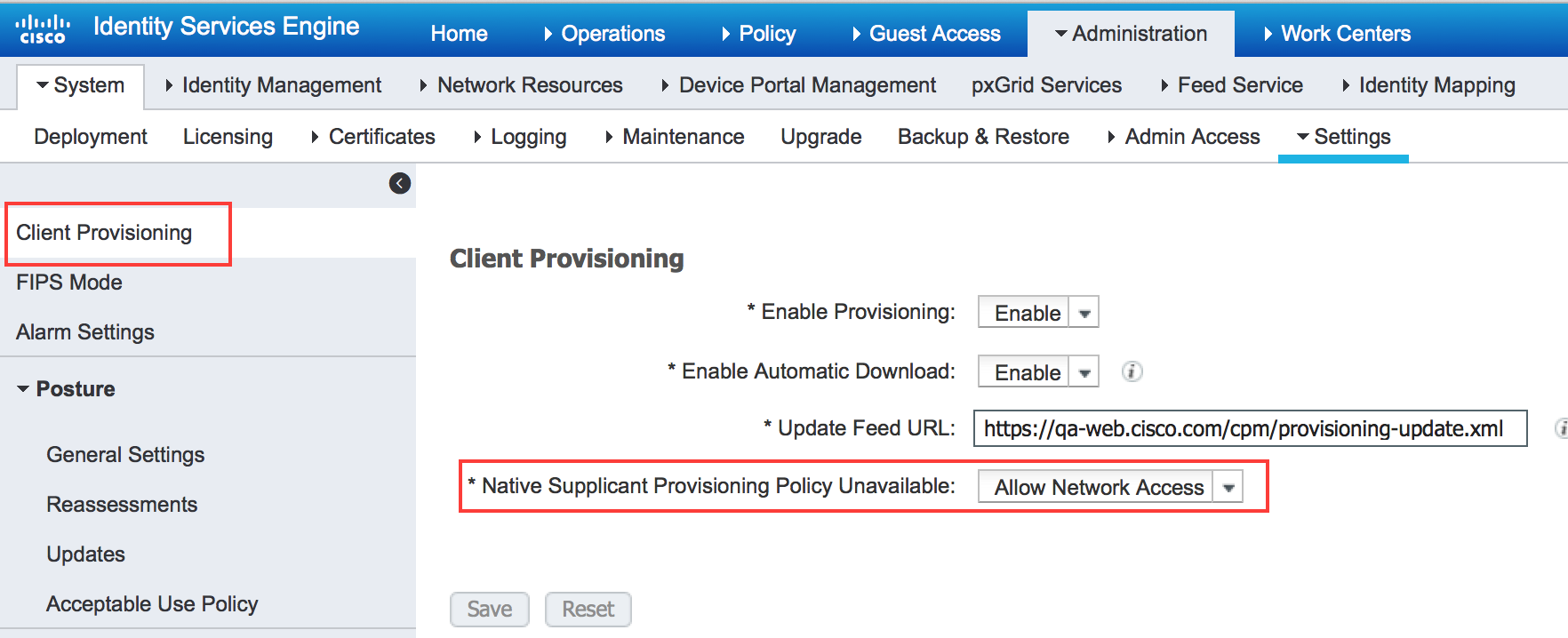
So that your users are not required to click an install and just right to registration success. Under your Client Provisioning Policies remove any policies for NSP BYOD.
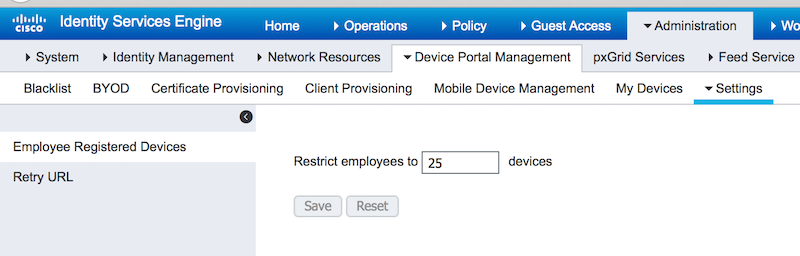
Set how many devices can be used
Administration > Device Portal Management > Settings > Employee Registered Devices
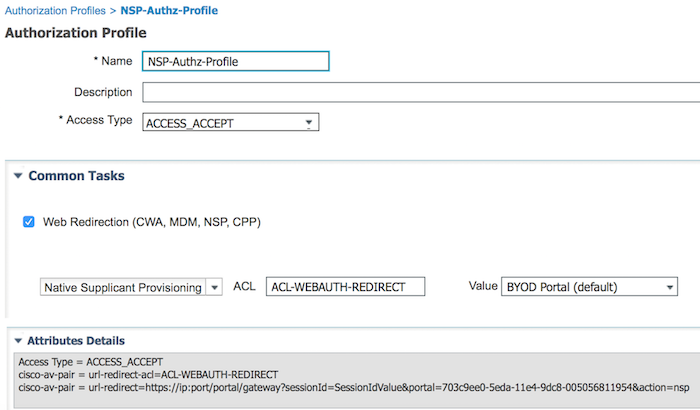
There are 2 authz profiles
1 that sends back the WLC redirect ACL and to the BYOD/NSP portal
Another NSP that permits Access with the WLC ACL for permit access
- NOT SHOWN
And a blacklist that’s already built in
- NOT SHOWN
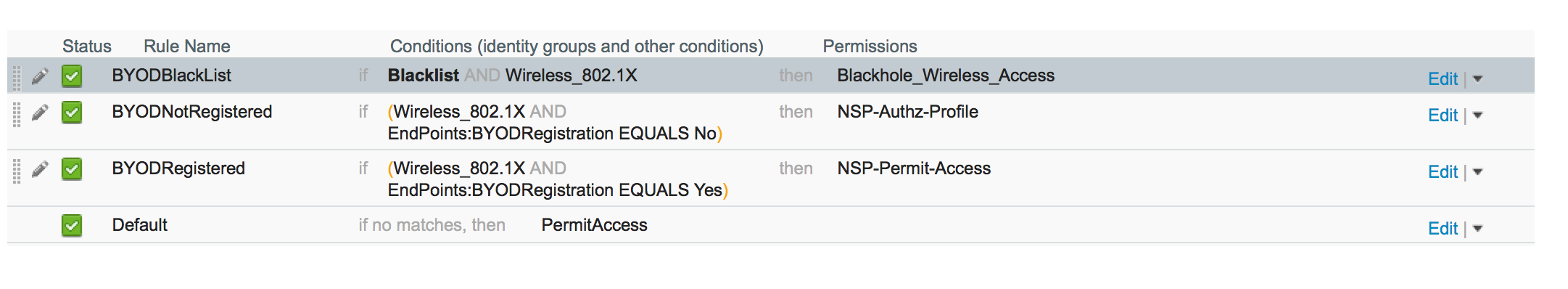
Authz rules
Here are needed rules
Please rate my blog! Thanks!
