In this post, we are going to enable the services for our ISE node and configure the Identity Mapping Service (known as PassiveID in ISE 2.1) between ISE and Active Directory in this blog post. The Identity Mapping service enables ISE to monitor users that are authenticated by a domain controller and not by ISE. This feature will be useful for the EasyConnect configuration that I will go over in later posts. It is able to gather this information by connecting to Active Directory using the Microsoft WMI interface and by querying logs from the Windows event messaging.
We previously configured our Group Policy in Active Directory to allow ISE to gather these logs. If you need to review that configuration, please click here. In this post, we will configure the ISE node for Identity Mapping/PassiveID integration and test it out.
Open the ISE GUI and navigate to Administration>System>Deployment. Click on the hostname of your ISE node that you are using. . This will bring up the Edit Node page. Check the following boxes on this page to enable this node for pxGrid:
- Enable SXP Service - This is a service that allows endpoints to communicate Security Group Tagging to IP Address binding. This is not necessary for pxGrid but it is good for TrustSec which I will be configuring in later blog posts.
- Enable Device Admin Service - This is for if you are using your ISE node for TACACS+ so you can use ISE for administration of your network access devices. It's not needed for pxGrid but since I will be doing a post later on TACACS+ and ISE 2.0, I'll be checking this option.
- Enable Identity Mapping (in ISE 2.1, this is Enable Passive Identity Service) - This most certainly is for pxGrid integration. This specifies that this host can be used for pxGrid identity mapping .
- Pxgrid - This enables the pxGrid service for this host
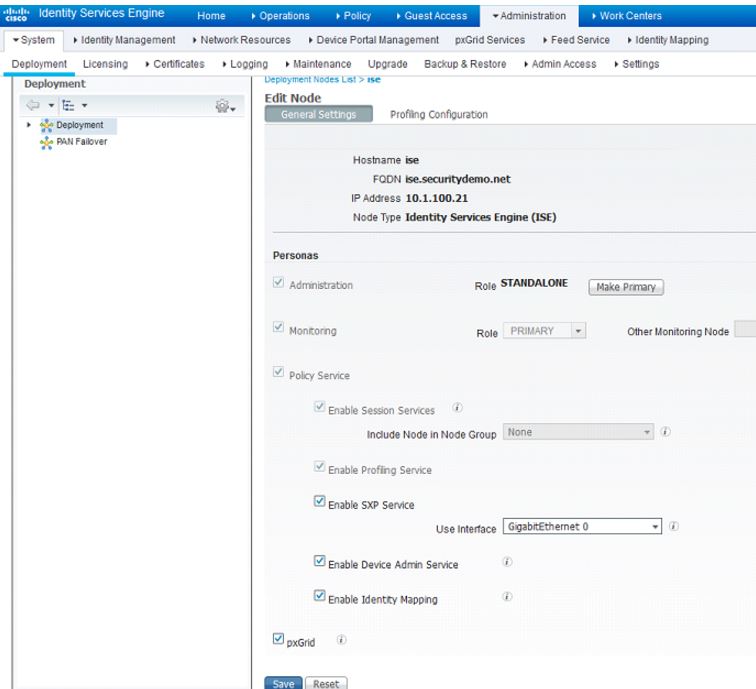
Note: In ISE 2.1, one additional persona added:
- Enable ThreatCentric NAC Service - This enables ISE 2.1 for the Threat Centric NAC services that allow for ISE integration with AMP for Endpoints and Qualys
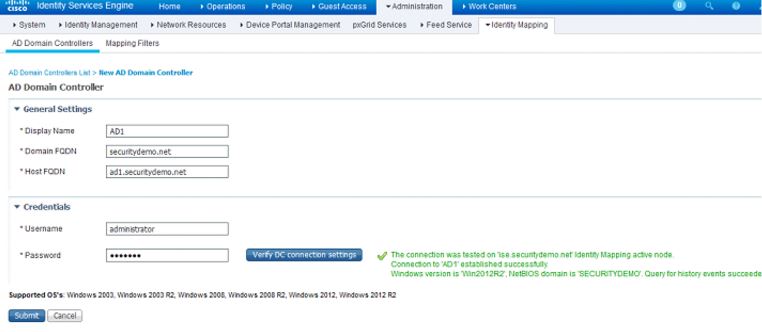
Navigate to Administration>Identity Mapping>AD Domain Controllers (In ISE 2.1, this is called PassiveID) and click Add. If the instructions from the previous blog post was followed correct for PassiveID configuration in you Group Policy, you should be able to add the AD server on this page with ease. In the New AD Domain Controller page, the fields are pretty self-explanatory. For the credentials, use the credentials you planned on using when you configured the Group Policy (either a Domain Admin or non-Domain Admin account). You can configure up to 80 Domain Controllers for PassiveID.
Click on the Verify DC connection settings button to verify this connection. Sometimes I've noticed that it might fail the first time you try so try again at least once or twice. If everything is configured correctly on both the ISE server and the Active Directory server, you should get a green check box verifying that the connection was established correctly. If you receive this success message, click Submit to save the settings.
If you did not have a successful connection, check the following to troubleshoot:
- GPO settings
- User credentials
- Network connectivity between ISE and the AD server
- ISE is using a DNS server that have the Active Directory FQDN in it
By establishing this Identity Mapping, you should see users logging into the domain under Operations>RADIUS Livelog regardless of whether they are connected to an device authenticating through ISE or not.
Next, we are going to enable the Pxgrid services for Auto-Registration. This will enable your Pxgrid clients to seamlessly add themselves to ISE in later blog posts. In a production environment, you might want to disable the auto-registration if you want to manually approve Pxgrid clients but for a lab, I don't typically do so. Navigate to Administration>Pxgrid Services and click on the Enabled Auto-Registration link on the top right-hand corner.