Network security is critical in today’s fast-growing infrastructure. To protect the data and provide next-generation firewall capabilities, Firepower has emerged to combat the growing threats and provide end-to-end data security with its robust firewalling capabilities. However, with the high-end security and data processing by any firewall, there is a latency, and that is unacceptable in scenarios where every microsecond counts or in situations where there is a high burst of data flowing through. For example, low latency is critical in data centers that run the database servers doing bandwidth intensive procedures such as backup to a different datacenter segment.
To ensure that the big data flows that get through Firepower are processed quickly, the Flow Offload feature was introduced. This feature ensures that the flow that is trusted by the Firepower data path doesn’t need any processing by the x86. It is offloaded to the smart NIC hardware, which is lightning fast. Just to share the numbers, when the flow is offloaded, we can have a scintillating 21G TCP throughput and 40-G UDP throughputs. A test demonstrates that we can transfer 64 bytes of UDP packets with just 2.9 microseconds of delay.
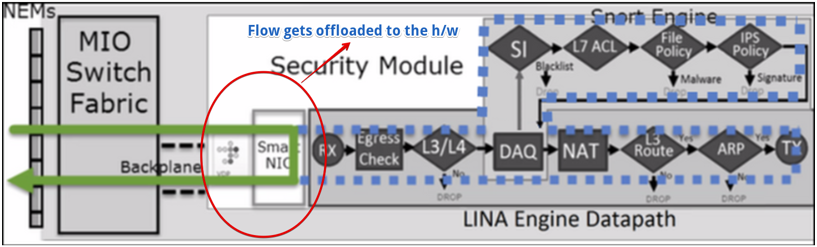
The flow offload on Firepower 9300s and 4100s generally would trigger with the prefilter allowing the fast path for the given traffic. However, with the introduction of Dynamic Flow Offload in Firepower Threat Defense 6.3 release, SNORT dynamically decides to offload given traffic. The dynamic offloading is done under the following conditions:
- When the flows match an access control policy's trust rule action
- When there are flows that are trusted by the Intelligent Application Bypass (IAB) policy either explicitly or due to exceeding flow bypass thresholds
- When the flows that match file or intrusion policies qualify for flow offload. This results in the x86 pushing the flow to the smart NIC
The Flow offload feature is enabled by default, and it can be disabled manually using SFCLI:
> configure flow-offload dynamic whitelist disable
This feature is supported in high availability mode (active/standby) pair and clustering mode wherein the symmetric flows (forward and backward flows hitting the connection owner directly) can be offloaded easily to the smart NIC.
Some of Cisco's competitors follow a similar behavior, which is purely at the cost of security. Their focus is primarily centered on to fast switch the traffic through the hardware. With Firepower, when the flow is offloaded to the hardware smart NIC, Firepower is intelligent enough to offer a certain level of security by performing TCP sequence randomization, rewrite of header fielder of IP Addresses and NAT/PAT. This intelligence makes Firepower a winner over its competitions.
After a flow is offloaded, packets within the flow may also be returned to the Firepower Threat Defense device for further processing under the following conditions:
- When the packets from a particular flow include TCP options other than the timestamp
- When packets from the flow are fragmented or are subjected to Equal-Cost Multi-Path (ECMP) routing
- When the ingress packets move from one interface to another
This innovation and improvisation are a savior when dealing with thick fat flows and is readily accepted by the customers globally on the field.
Cheers!
- Hemant Madan
