Introduction
In this blog we will configure Remote Access VPN on cisco ASA with authentication using Certificate but Authorization using ISE via Active Directory.
Video lab demo: https://youtu.be/UJWUk3ria88
Certificate based authentication in conjunction with Anyconnect VPN, the certificate authentication process terminates on the ASA. Since the ASA terminates the authentication process without passing the certificate to ISE, So when the request comes to ISE it tries to process a full authentication. There is no password in the TCP packet, thus authentication fails.
Thus, we need to bypass Authentication on the ISE for such communication.


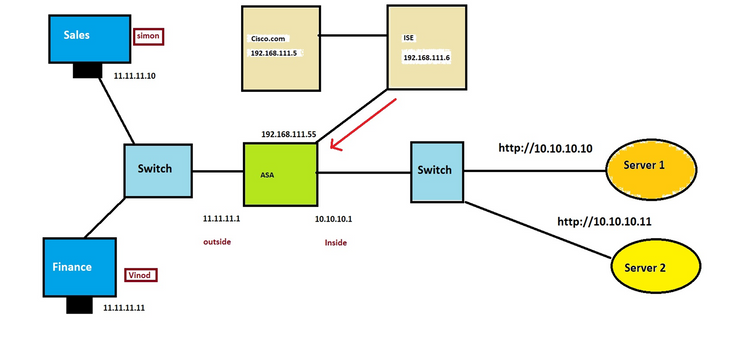
TOPOLOGY
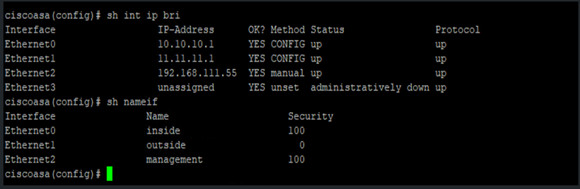
Below is the pre-Build configuration for ASA.
•Task 1: Certificate Based Authentication
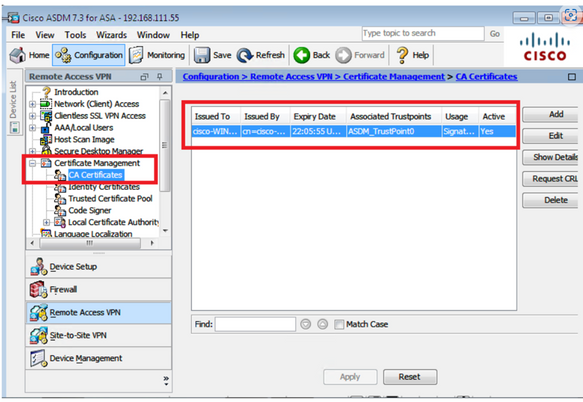
Step 1 of 3: Install the Root CA certificate into ASA
Step 2 of 3 – Setup Tunnel Group
!
tunnel-group sales.w365.vpnet.com type remote-access
tunnel-group sales.w365.vpnet.com general-attributes
address-pool sales
default-group-policy GroupPolicy_sales.w365.vpnet.com
tunnel-group sales.w365.vpnet.com webvpn-attributes
authentication certificate
group-alias sales.w365.vpnet.com enable
!
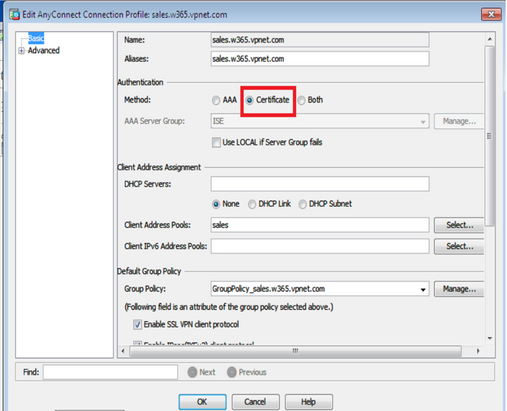
Step 3 of 3 – Setup Tunnel Group
!
group-policy GroupPolicy_sales.w365.vpnet.com internal
group-policy GroupPolicy_sales.w365.vpnet.com attributes
wins-server none
dns-server value 192.168.111.5
vpn-tunnel-protocol ikev2 ssl-client ssl-clientless
group-lock value sales.w365.vpnet.com
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split-acl
default-domain value cisco.com
split-dns value cisco.com
address-pools value sales
webvpn
anyconnect keep-installer installed
anyconnect profiles value sales.w365.vpnet.com_client_profile type user
always-on-vpn profile-setting
!
Testing
•User Attempt to connect
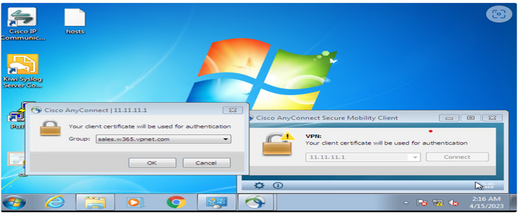
•Certification Based Authentication is performed.
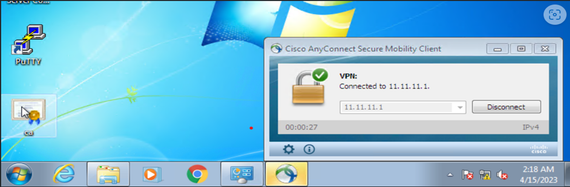
•User is successfully connected.
•Task 2: Setup Authorization
•Task 2: Part 1- Setup ASA for Authorization
Part 1: Step 1 of 2 -Setup ASA for Authorization
•Following extra configuration must be added into ASA
!
aaa-server ISE protocol radius
interim-accounting-update
aaa-server ISE (management) host 192.168.111.6
key *****
!
Part 1: Step 2 of 2 -Setup ASA for Authorization
!
tunnel-group sales.w365.vpnet.com type remote-access
tunnel-group sales.w365.vpnet.com general-attributes
address-pool sales
authorization-server-group ISE
default-group-policy GroupPolicy_sales.w365.vpnet.com
authorization-required
tunnel-group sales.w365.vpnet.com webvpn-attributes
authentication certificate
group-alias sales.w365.vpnet.com enable
!
•Task 2: Part 2- Setup ISE for Authorization
Part 2: ISE: Step 1 of 6
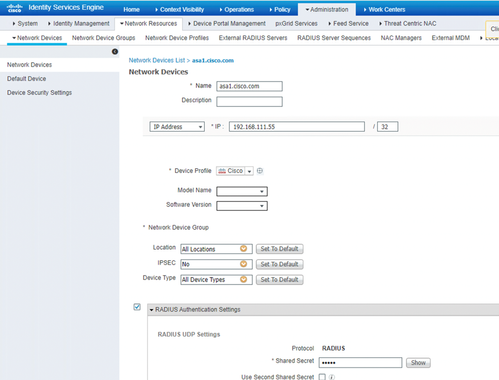
Part 2: ISE: Step 2 of 6
•Perform Active Directory Integration and fetch the AD Groups.
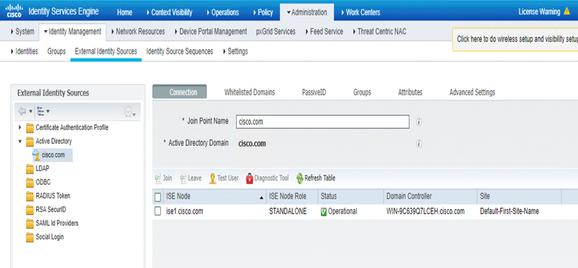
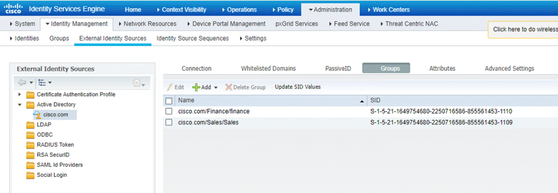
Part 2: ISE: Step 3 of 6
•Create right Authorization Profile
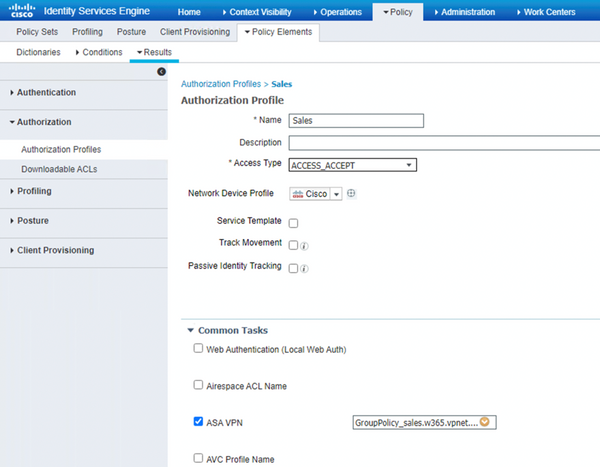
Part 2: ISE: Step 4 of 6
•Create Access Policy
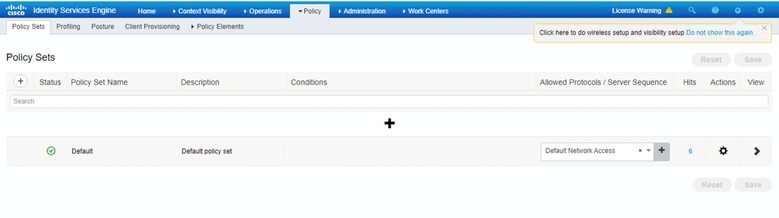
Part 2: ISE: Step 5 of 6
•Authentication Policy

Part 2: ISE: Step 6 of 6
•Authorization Policy
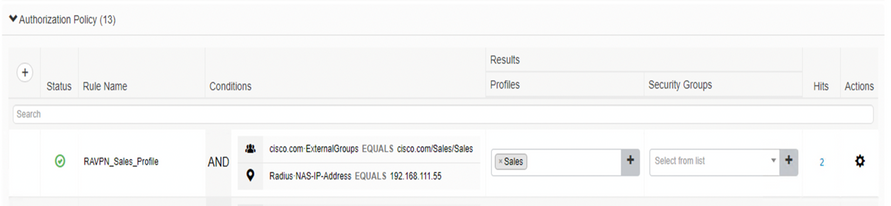
Packet Capture Analysis
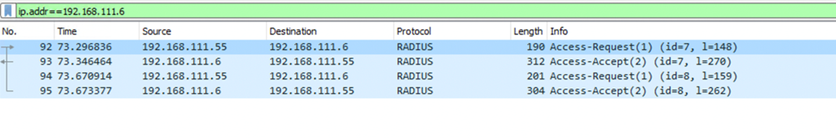
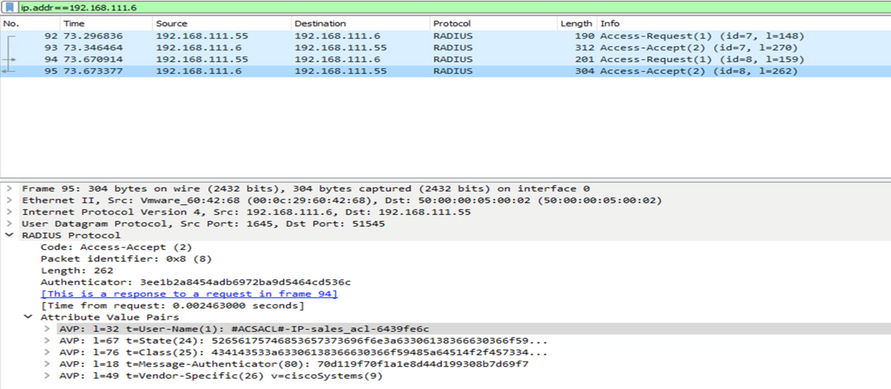
Packet 1:
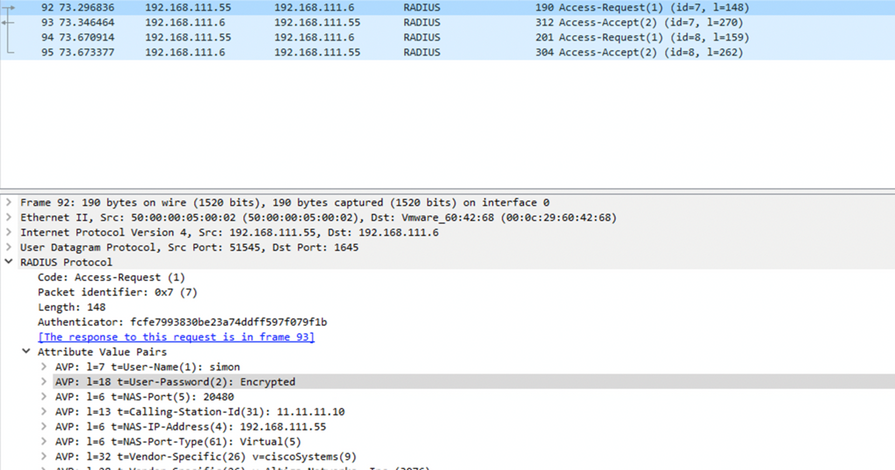
Packet 2:
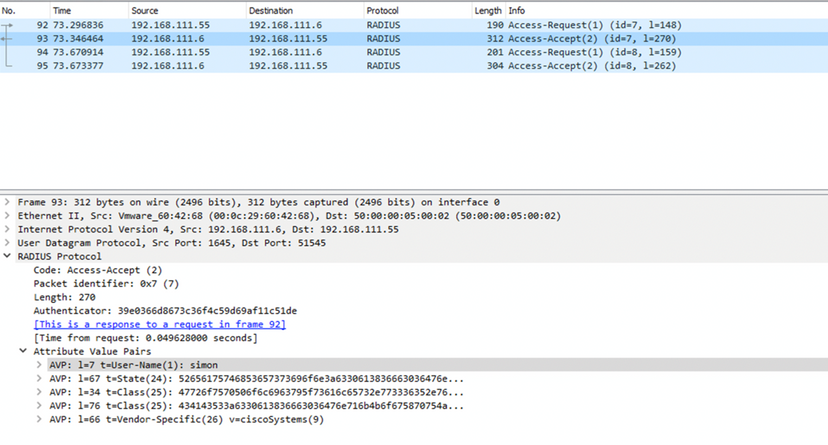
Packet 3:
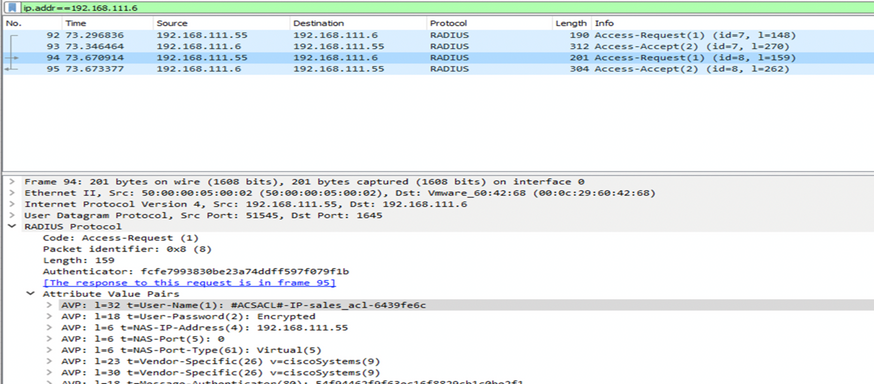
Packet 4: