At this point, we've added our roles, created Certificate Templates, pushed out a GPO, and laid the groundwork for Pxgrid Identity Mapping (PassiveID in ISE 2.1) . This is the point where I finish up with some last minute housekeeping items and run a couple of tests.
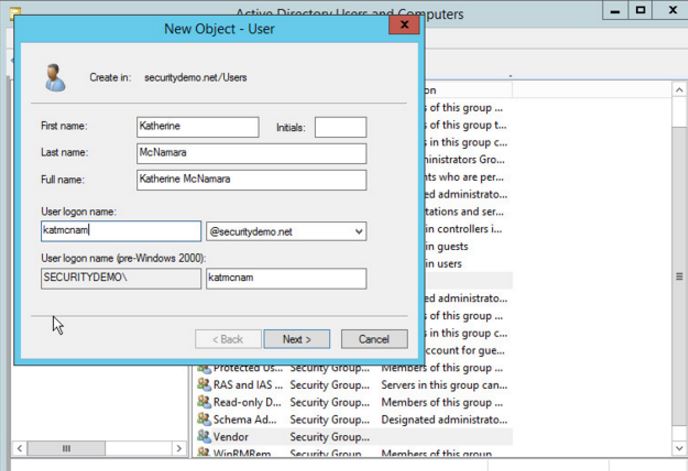
The first thing I usually do is create some test users and groups in Active Directory Users and Computers. Here are the following users and groups I created for the purposes of my lab:
- Katherine McNamara - Domain Admin, BYOD-Users
- Jessica Jones - Employee, BYOD-Users
- Tony Stark - Vendor

Another thing that needs to be done before moving over to ISE is making sure that the time is set correctly. If you haven't already checked at this point, your certificates that have been issued might be in a different year, expired, etc. Not to mention, ISE is very picky about time and will not join the domain if the time is off by greater than 5 minutes. There are a couple ways of setting the time correctly:
- You can manually set it between ISE and the AD server but this can cause issues if either server is turned off for an extended period of time
- You can have it sync up with the ESXi host - realistic for a lab, not always for production
- You can use Powershell to do so as described in the following directions:
- http://www.sysadminlab.net/windows/configuring-ntp-on-windows-server-2012
I would also recommend making sure that your server is issuing both computer and user certificates. A good way to check is to attach a computer to the local network and join it to the domain. After it's been joined and restarts, login with your user credentials. If you open up Certification Authority again, you should be able to see the issued certificates under the Issued Certificates folder

Likewise, you can open an MMC on the local computer that you joined and also add a snap-in to check the local Computer and User certificates to make sure they are there.
If you find yourself not having certificates issues, some good troubleshoot steps are:
- Check the Failed Requests folder in Certification Authority
- Check to make sure that the GPO is being pushed to the local machine by doing a RSOP
- Check the permissions on your certificate template to be sure that your Domain User and Domain Computer groups have Read, Enroll and Autoenroll permissions for the appropriate certificate templates. Also make sure that other certificate templates do not have the same autoenroll permissions (pxGrid)
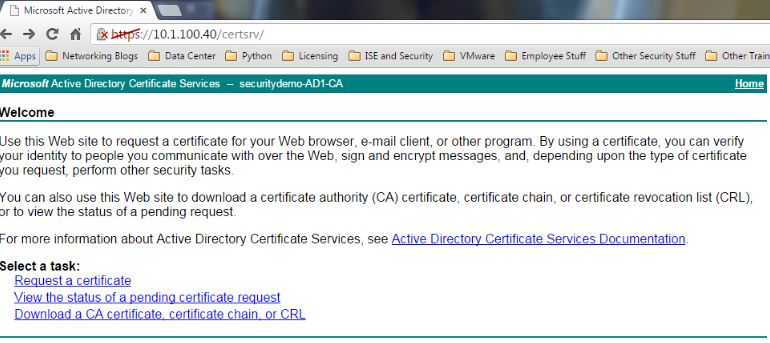
The next thing I like to do after this is to ensure that my Certificate Web Enrollment Page is working. Open the browser on a computer attached to the local network or on your Server 2012 VM and navigate to https://AD-Server-IP/certsrv and make sure you are getting the following page:
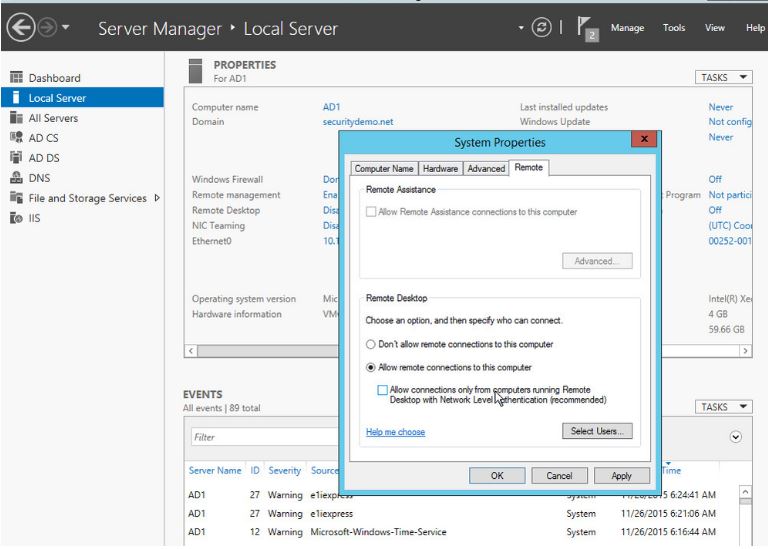
In Server Manager, click on Local Server on the left-hand side. In the Properties panel, click on Remote Desktop. This is where I like to allow Remote Desktop access so I don't have to console in from vSphere every time I want to get into my server.
I usually like adding all of my lab appliances to DNS as well for the sake of management later one. Go to the Start menu and open up DNS. Add the DNS records for the devices you plan on using.

