- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- IP Phone SSL VPN to ASA using AnyConnect
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-05-2010 08:06 AM - edited 08-28-2017 10:14 PM
- Purpose
- Functional Overview
- CUCM Places ASA Certificate Hash and VPN URL in Phone Config
- Phone Connects to ASA
- Software Versions
- Phone Models
- CUCM Configuration
- Phone Configuration
- ASA Configuration
- Additional Requirements:
- Troubleshooting Steps
- Common Issues
Purpose
Starting in CUCM 8.0.1 and IP Phone Firmware 9.X, IP Phones are now able to directly connect to an ASA using the AnyConnect VPN. This document will help address some common issues encountered during intial configuration. This guide will act as a supplement to the Official IP Phone VPN Documentation.
Functional Overview
Before we get into versions and model numbers let's look at how the feature works.
CUCM Places ASA Certificate Hash and VPN URL in Phone Config
Before the phone is ready for VPN, it must first be provisioned using the internal network. This requires direct access to the CUCM TFTP server.
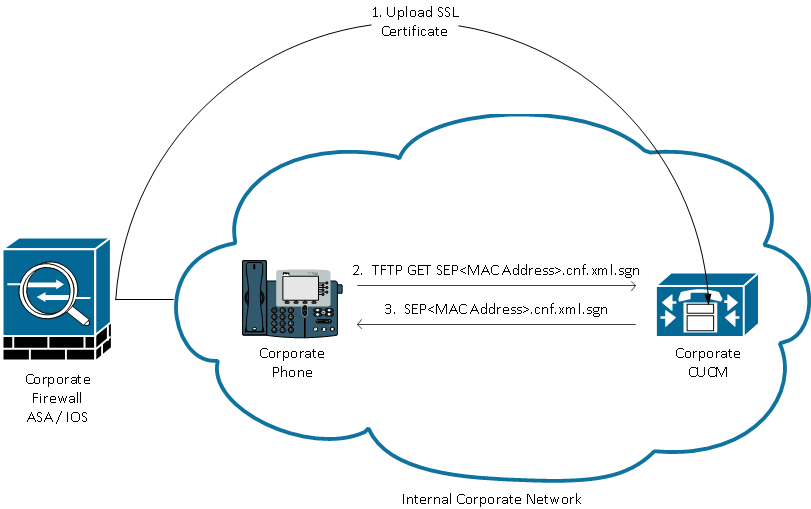
The first step after the ASA is fully configured is to take the ASA HTTPS Certificate and upload it to the CUCM server. This allows the CUCM server to build an IP phone config file that tells the phone how to get to the ASA. The CUCM requires some additional configuration to associate the uploaded certificate with a VPN Profile that can be assigned to the phone.
Here is an example of the IP Phone VPN section of a phone's config file after performing the required configuration:
jasburns@jasburns-gentoo /home/jasburns $ tftp 14.48.44.80 tftp> get SEP0011215A1AE3.cnf.xml.sgn Received XXXX bytes in 0.0 seconds jasburns@jasburns-gentoo /home/jasburns $ cat SEP0011215A1AE3.cnf.xml.sgn .......... <vpnGroup> [Some Lines Omitted] <addresses> <url1>https://X.X.X.X/PhoneVPN</url1>
</addresses>
<credentials>
<hashAlg>0</hashAlg>
<certHash1>1eD9l3VEI9DGWQGKlNBGE1bRhUg=</certHash1>
</credentials>
</vpnGroup>
Note that the URL is printed exactly as entered on the VPN Gateway Configuration page in CUCM. Make sure the IP Phone can resolve this address.
Even more interesting is the Cert Hash. The IP phone configuration does not contain the entire certificate, merely a SHA1 Base64 encoded hash of the certificate.
You can compare the certificate hash in the IP phone configuration file to the cert hash of the actual file on the ASA or CUCM if you copy it to a computer running OpenSSL (either Windows, Linux, or Mac)
$ cat r2800.cisco.com.pem
-----BEGIN CERTIFICATE-----
<Base64 value of the cert omitted>
-----END CERTIFICATE-----
openssl x509 -in r2800.cisco.com.pem -noout -fingerprint
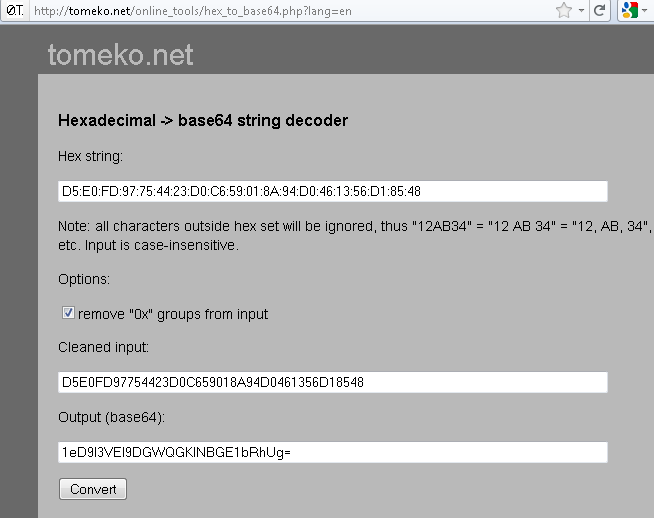
SHA1 Fingerprint=D5:E0:FD:97:75:44:23:D0:C6:59:01:8A:94:D0:46:13:56:D1:85:48
This is the SHA1 Fingerprint in Hexadecimal form. In the configuration file this value is instead printed as the Base64 value. I used the following website to convert from Hex to Base64:
http://tomeko.net/online_tools/hex_to_base64.php
This method can be used to verify the certificate loaded onto and presented by the ASA matches the certificate hash loaded into the phone.
Phone Downloads Configuration
This part is extremely important. The phone must download the configuration (including the certificate hash in Base64) while it is inside the network and has direct access to the CUCM TFTP server.
The phone has to be provisioned inside the network before it can be moved outside the network and use the VPN feature.
Phone Connects to ASA
After internal provisioning has been completed, the phone can be moved to the external network for VPN access. Here the Corporate Phone has been moved to a Home location.
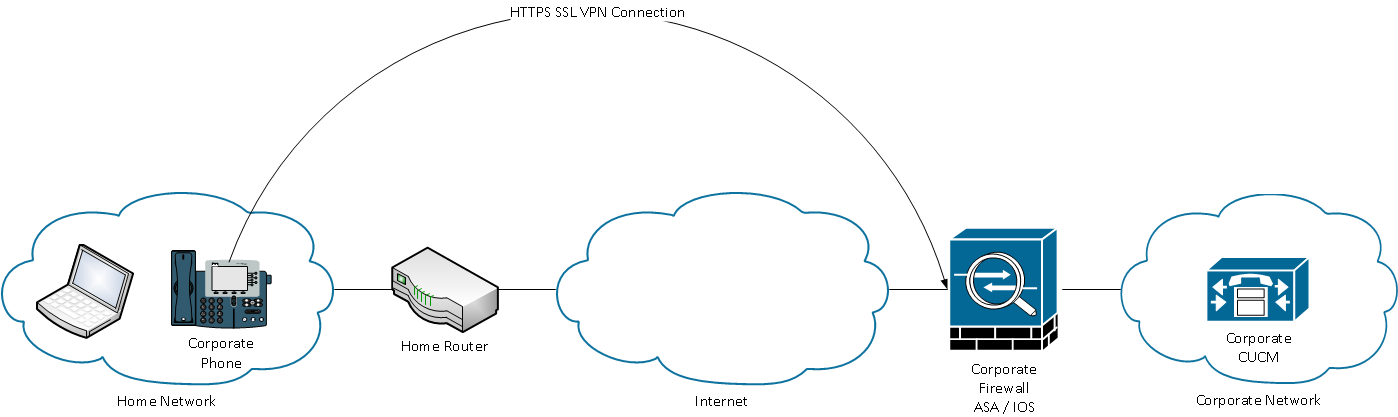
Depending on the phone's configuration it will either automatically attempt to connect to the VPN gateway, or will connect once manually initiated. If auto network detect is enabled, the phone will try to ping the TFTP server. If there is no response to this ping request the phone will automatically bring up the VPN process on the phone.
The phone connects on TCP port 443 over HTTPS to the ASA. The ASA responds back with the configured certificate, hopefully the same certificate uploaded to CUCM. In additional TCP 443 (Transport Layer Security, or TLS), the phone will also connect on UDP 443 for DTLS (Datagram Transport Layer Security).
Phone Verifies Presented Certificate
The phone console logs show us the hash of the certificate that the ASA presents in Hex form:
3943: INF 18:10:22.354209 VPNC: vpnc_save_to_file: wrote: </tmp/leaf.crt>, 479 bytes
3944: NOT 18:10:22.355351 VPNC: cert_vfy_cb: peer cert saved: /tmp/leaf.crt
3945: NOT 18:10:22.361892 SECD: Leaf cert hash = D5E0FD97754423D0C659018A94D0461356D18548
3946: NOT 18:10:22.362574 SECD: Hash was found in the trust list
3947: NOT 18:10:22.400294 VPNC: VPN cert chain trusted
These messages show us that the phone was able to validate the certificate that the ASA presented. The cert presented matched the hash in the configuration file.
At this point the phone will establish an SSL session with the ASA and continue setting up the VPN tunnel.
All communication will now flow between the phone and the ASA in an encrypted tunnel. Once the traffic reaches the ASA it will be decrypted and forwarded along to any location in the network that the phone would like to connect to.
The beauty of this solution is that the phone obtains an address on the Internal network that is typically not filtered. The phone can connect using SCCP, SIP, HTTP, HTTPS to any server inside the Corporate Network. This allows advanced phone services and features to function that might not work through ASA Phone Proxy.
Software Versions
CUCM >= 8.0.1.100000-4
IP Phone >= 9.0(2)SR1S - SCCP
ASA >= 8.0.4
Anyconnect VPN Pkg >= 2.4.1012
Note: A "Premium" license and an "AnyConnect for Cisco VPN Phone" license is required. The part number for the "AnyConnect for Cisco VPN Phone" is L-ASA-AC-PH-55XX= where XX = 05,10,20,40,50,80.
Phone Models
7942 / 7962 / 7945 / 7965 / 7975 / 8961 / 9951 / 9971. For a complete list of supported phones in your CUCM version go to:
https://<CUCM Server IP Address>:8443/cucreports/systemReports.do
Unified CM Phone Feature List
Generate a new report
Feature: Virtual Private Network
http://www.cisco.com/en/US/docs/voice_ip_comm/cucm/security/8_5_1/secugd/secuvpn.html
CUCM Configuration
The following document provides a complete set of configuration tasks required to configure CUCM for this feature:
http://www.cisco.com/en/US/docs/voice_ip_comm/cucm/security/8_5_1/secugd/secuvpn.html
Note: Please make sure the URL for the VPN Gateway contains the full and correct address to reach the IP Phone VPN tunnel-group on the ASA.
Phone Configuration
- Use a supported phone model per the CUCM Supported Models / Features report.
- Register the phone to the CUCM server on the Internal network
- Configure the IP phone with a TFTP server manually.
- Move the phone to the external network.
ASA Configuration
Configure Anyconnect VPN access on ASA to provide network access.
See http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a00808efbd2.shtml for example configuration.
The lateset CUCM Security Guide also provides sample ASA configuration.
Additional Requirements:
- The ASA must have the AnyConnect for Cisco VPN Phone Licensed feature enabled. Licensing info can be found using show version command.
- Group-policy must not be configured with split tunnel or split exclude. Only tunnel all is the supported tunneling policy
- The tunnel-group used can not be the DefaultWEBVPNGroup. Create another tunnel-group and use "group-url https://x.x.x.x/phonevpn enable to map to the correct tunnel-group.
- DTLS must be enabled and negotiated for operation. This requires both tcp/443 and udp/443 to be open and allowed on all devices between the ASA and the phone.
Troubleshooting Steps
- Plug the phone into the internal network. This will test whether the phone's configuration works prior to adding VPN.
- Connect with AnyConnect on a PC from the outside to the ASA. This will confirm that the ASA is configured correctly for Anyconnect
- From the connected PC try to ping the TFTP server and CUCM server. This will test basic ip connectivity to the two servers.
- From the PC try to download the TFTP config file for the phone in question "tftp -i <TFTP Server> GET SEP<Mac Address>.cnf.xml" This will test that the tftp service is reachable and serving files.
- From the PC try to telnet to TCP Port 2000 on the CUCM server "telnet <CUCM IP> 2000". This should immediately come back with a new line and a blank cursor. This will test connectivity to the CUCM SCCP port, for SIP registrations use port 5060 instead.
Common Issues
- One-way or no voice. The phone registers and makes calls but no audio is heard. Confirm routing between the two phone/rtp stream endpoints.
- Auto Network Detect does not reliably work in IP Phone Firmware 9.0(2), but does work as expected in 9.2(1).
- Auto Network Detect allows the phone to detect whether it is inside or outside the network. If outside it will bring up the VPN, if inside, it will connect directly.
- The phone uses a series of pings to the TFTP server to determine whether it is outside the network. If pings to the TFTP server fail, the VPN GUI will be brought up on the phone and the phone will attempt to access the VPN URL.
- Username and Password authentication from the phone does NOT support the SPACE character in either the username or the password.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Are video calls supported on the 9971 with this method?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
This is completely possible, but covered in another document for IOS SSL Phone VPN
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Video calls over the VPN should work as long as you have enough bandwidth.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
We did a lab recreation here and we confirmed the VPN phone can connect using AnyConnect Essential License. This is an option instead of use the Premium License.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hi everyone. is it work on CIUS? i want to connect my CIUS with anyconnect, and registered with my CUCM. I already buy the ASA license to enable AnyConnect for mobile. When i try connecting CIUS to ASA ,there's message from CIUS "phone service unavailable" and "telephone service is unavailable". Do i need to buy another license to enable AnyConnect for CISCO VPN Phone?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
This should work with the CIUS without any additional licensing. If it's not working correctly you could possibly have a CIUS without a MIC (manufaturer installed certificate)
You can double check if you're running into this problem by bringing your CIUS back to the internal network, turning on SSH Enabled from the CCM Admin Device > Phone page for this CIUS, and trying to SSH in. If your SSH connection fails you could be running into this problem.
If the SSH connection works then start troubleshooting by looking at the logs on your ASA.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Jason,
I'm trying this for the first time and I'm getting authentication fails and I'm using certificate authentication. I've enclosed a portion of the phone logs when trying to connect. I have a TAC case open and the engineer is struggling to resolve this.
In the log, there is this which I cannot explain nor can the TAC engineer:
1105: ERR 03:11:43.582021 VPNC: process_login: login failed, 'webvpn=' not found in cookie
The status messages on the phone:
| 3:11:32a SEPC40ACBE02496.cnf.xml.sgn | |
| 11:06:35a Trust List Updated | |
| 11:06:36a SEPC40ACBE02496.cnf.xml.sgn | |
| 3:11:37a Trust List Updated | |
| 3:11:37a SEPC40ACBE02496.cnf.xml.sgn | |
| 3:11:43a VPN Certificate Failed | |
| 3:11:51a VPN Certificate Failed | |
| 3:11:54a VPN Certificate Failed | |
| 3:11:58a VPN Certificate Failed | |
| 3:12:21a VPN Certificate Failed |
Rest of log snippet:
1093: NOT 03:11:43.278959 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 write finished A
1094: NOT 03:11:43.280149 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 flush data
1095: DBG 03:11:43.286144 VPNU: State AppsUp --> AppsUp
1096: DBG 03:11:43.286858 VPNU: SM wakeup - chld=0 tmr=0 io=1 res=0
1097: DBG 03:11:43.287476 VPNU: State AppsUp --> AppsUp
1098: NOT 03:11:43.482563 VPNC: ssl_state_cb: TLSv1: SSL_connect: SSLv3 read finished A 1099: NOT 03:11:43.484081 VPNC: create_ssl_connection: SSL setup done
1100: NOT 03:11:43.484729 VPNC: do_login: sending (HTTPS) login request...
1101: NOT 03:11:43.486590 VPNC: do_login: waiting for login response
1102: NOT 03:11:43.579454 VPNC: do_login: got login response
1103: NOT 03:11:43.580670 VPNC: process_login: HTTP/1.1 200 OK
1104: NOT 03:11:43.581322 VPNC: process_login: login code: 200 (ok)
1105: ERR 03:11:43.582021 VPNC: process_login: login failed, 'webvpn=' not found in cookie
1106: ERR 03:11:43.582666 VPNC: do_login: process_login failure
1107: WRN 03:11:43.584131 VPNC: ssl_state_cb: TLSv1: write: alert: warning:close notify
1108: NOT 03:11:43.585806 VPNC: vpn_stop: de-activating vpn
1109: NOT 03:11:43.586465 VPNC: vpn_set_auto: auto -> auto
1110: NOT 03:11:43.587083 VPNC: vpn_set_active: activated -> de-activated
1111: NOT 03:11:43.587667 VPNC: set_login_state: LOGIN: 1 (TRYING) --> 3 (FAILED)
1112 NOT 03:11:43.588252 VPNC: set_login_state: VPNC : 1 (LoggingIn) --> 3 (LoginFailed) 1113: NOT 03:11:43.588844 VPNC: vpnc_send_notify: notify type: 1 [LoginFailed]
1114: NOT 03:11:43.589417 VPNC: vpnc_send_notify: notify code: 11 [LoginFailure]
1115: NOT 03:11:43.589998 VPNC: vpnc_send_notify: notify desc: [no valid session cookie]
1116: NOT 03:11:43.590660 VPNC: vpnc_send_notify: sending signal 28 w/ value 13 to pid 7
1117: ERR 03:11:43.591326 VPNC: protocol_handler: login failed
1118: ERR 03:11:43.592397 VPNC: vpnc_recv_cmd_resp: cmd 0x00000300 [LOGIN], status: 0 [MCAPI_ERROR]
1119: NOT 03:11:43.598175 JVM: --> Properties JNI: SignalApp() handling SIGIPCFG. msgCode=256 value=13
1120: ERR 03:11:43.611098 JVM: --> IPCFG_VPN_NOTIF, SignalApp() handling SIGIPCFG. signal=0
1121: NOT 03:11:43.612806 JVM: <-- Properties JNI: SignalApp()
1122: DBG 03:11:43.793697 VPNU: SM wakeup - chld=0 tmr=0 io=1 res=0
1123: DBG 03:11:43.797509 VPNU: State AppsUp --> AppsUp
1124: DBG 03:11:43.798183 VPNU: SM wakeup - chld=0 tmr=0 io=1 res=0
1125: DBG 03:11:43.798828 VPNU: State AppsUp --> AppsUp
1126: DBG 03:11:48.569959 VPNU: SM wakeup - chld=0 tmr=0 io=1 res=0
1127: NOT 03:11:48.571952 VPNC: vpnc_configure: got URL: <https://97.X.X.X/phonevpn>
1128: NOT 03:11:48.572997 VPNC: protocol_handler: got set url command
1129: NOT 03:11:48.573642 VPNC: protocol_handler: url <https://97.X.X.X/phonevpn>
1130: DBG 03:11:48.574629 VPNU: State AppsUp --> AppsUp
I hope this is enough information to have you provide some suggestions. We've tried certificates over and over with the TAC engineer. We tried exporting them straight from the ASA to CUCM and tried connect to the SSL VPN from a PC and downloaded the certificate from the IE browser. Obviously there is an issue with the certificate, but we can't figure it out.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
do I need to have also a uc proxy license when i want to use srtp?
Does srtp work inside the anyconnect ssl tunnel?
thanks
Marco
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Marco,
The point of the VPN being built is so that it is as if the phone were on your local network. A normal phone registration will happen over the tunnel (without needing NAT or inspection) as a result you don't need to have the ASA be a proxy.
With that being said, if you run Secure VoIP in your network I don't see why it would work to have SRTP run over the VPN tunnel. If your reason for running Secure VoIP is just to protect it over the internet, with the VPN configured this is unnecessary. The VPN will protect the traffic from the phone up to the ASA.
Hope that helps.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I've had a tac case open for about a month and 5 tac engineers are still working on this case. We cannot figure out why when the phone attempts to connect, authentication fails. However, the same credentials work on a laptop.
Here is the log from ASA, any ideas?
CERT_API: Authenticate session 1, non-blocking cb=0x8be78a0
CERT API thread wakes up!
CERT_API: process msg cmd=0, session=1
CERT_API: Async locked for session 1
CRYPTO_PKI: Sorted chain size is: 1
CRYPTO_PKI: Found ID cert. serial number: 5A8B49E400000017XXXX, subject name: cn=CP-9951-SEPa456304198ea,ou=VTG,o=Cisco Systems Inc.,serialNumber=PID:CP-9951 SN:FCH1603XXXX
CRYPTO_PKI: Verifying certificate with serial number: 5A8B49E400000017XXXX, subject name: cn=CP-9951-SEPa4563041XXXX,ou=VTG,o=Cisco Systems Inc.,serialNumber=PID:CP-9951 SN:FCH1603XXXX, issuer_name: cn=Cisco Manufacturing CA,o=Cisco Systems.
CRYPTO_PKI: Checking to see if an identical cert is
already in the database...
CRYPTO_PKI(Cert Lookup) issuer="cn=Cisco Manufacturing CA,o=Cisco Systems" serial number=5a 8b 49 e4 00 00 00 17 XX XX | Z.I.......
CRYPTO_PKI: looking for cert in handle=ab3d12b0, digest=
2a 4c e4 67 57 70 cc 08 9e 20 41 f6 a7 6c XX XX | *L.gWp... A..l.
CRYPTO_PKI: Cert record not found, returning E_NOT_FOUND
CRYPTO_PKI: Cert not found in database.
CRYPTO_PKI: Looking for suitable trustpoints...
CRYPTO_PKI: Storage context locked by thread CERT API
CRYPTO_PKI: Found a suitable authenticated trustpoint anyconnect_Cisco_Manufacturing_CA_trustpoint.
CRYPTO_PKI(make trustedCerts list)CRYPTO_PKI:check_key_usage: ExtendedKeyUsage extension not found.
CRYPTO_PKI:check_key_usage:Key Usage check OK
CRYPTO_PKI: Certificate validation: Successful, status: 0. Attempting to retrieve revocation status if necessary
CRYPTO_PKI:Certificate validated. serial number: 5A8B49E400000017XXXX, subject name: cn=CP-9951-SEPa4563041XXXX,ou=VTG,o=Cisco Systems Inc.,serialNumber=PID:CP-9951 SN:FCH1603XXXX.
CRYPTO_PKI: Storage context released by thread CERT API
CRYPTO_PKI: Certificate validated without revocation check
CRYPTO_PKI: valid cert with warning.
CRYPTO_PKI: valid cert status.
CERT_API: calling user callback=0x8be78a0 with status=0
CERT_API: Async unlocked for session 1
CERT_API: process msg cmd=1, session=1
CERT_API: Async locked for session 1
CERT_API: Async unlocked for session 1
CERT API thread sleeps!
CERT_API: Authenticate session 1, non-blocking cb=0x8be78a0
CERT API thread wakes up!
CERT_API: process msg cmd=0, session=1
CERT_API: Async locked for session 1
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Troy, I had similar issues and also worked with TAC. I ended up monitoring on the ASA and found that I needed to update my NAT exemptions as well as access lists for this to work properly.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi all,
We have bought L-ASA-AC-PH-5520=Anyconnect Vpn Phone License for our Cisco Phones but when we entered this license into our ASA it shows th following i.e enabled for linksys phones.It enabled the linksys vpn phone rather than cisco phone vpn.Is this somekind of issue or Is there a diff part no to enable vpn for cisco phones. Its really urgent.
# sh act
ASA# sh activation-key
Licensed features for this platform:
Maximum Physical Interfaces : Unlimited
Maximum VLANs : 150
Inside Hosts : Unlimited
Failover : Active/Active
VPN-DES : Enabled
VPN-3DES-AES : Enabled
Security Contexts : 2
GTP/GPRS : Disabled
VPN Peers : 750
WebVPN Peers : 50
AnyConnect for Mobile : Disabled
AnyConnect for Linksys phone : Enabled
Advanced Endpoint Assessment : Disabled
UC Proxy Sessions : 2
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
The License for the Linksys phone was re-named to Cisco Phone. It is the same license and should work just fine for you. If you upgrade your code you'll see the name change in the lincense.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
I have configured the vpn phone at a customer site and it work successfully
It is now my second vpn phone configuration in a customer site
But it is not working here
I do all the required config for both the cucm and the ASA
But I need to highlight my topology setup if it is supported or not for the vpn phone
ASA at branch -----------wan-------- PIX at HQ ---- lan --- CUCM
The vpn phone license exist on the ASA on the branch site
but the CUCM exist on HQ
There is a PIX at HQ
So the CUCM isn't in the same LAN as the ASA
The ip phone can connect to the ASA but can't register at all
Trying to ping it from any where , not pingable
When connecting to the ASA from CIUS
to the same SSL VPN with the same URL
the CIUS can register successfully and make calls
Is any one see this topology not supported and that the CUCM must be on the same LAN with the ASA ?
Regards
Haitham
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Jhoback,
I have quite the same error "'webvpn=' not found in cookie". Have you managed to fix it? My blind guess is that it is related to the new ASA software and/or anyconnect. I'm using ASA 8.4.4 now and anyconnect 3.1. Btw, tried SSL VPN to IOS box and it works like a charm.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: