- Cisco Community
- Technology and Support
- Small Business Support Community
- Switches - Small Business
- Re: Inter-vlan routing on SG350-10MP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Inter-vlan routing on SG350-10MP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2020 10:39 PM
I have a Cisco SG350 that I am trying to configure for my domestic network. There is just one thing that I am not able to do, and I would like to know if you can help me out why and how to fix.
So my problem is: I have a NAS in vlan 30 and a PC in vlan 20. My PC cannot ping or access the NAS. My switch, however, can ping it from vlan 30 interface, but cannot ping it from any other vlan.
My vlans are all created in the firewall/router that is acting as the gateway for the SG350. From firewall to SG350 I have trunk ports configured.
I thought that because I have IP routing enabled in the switch, the inter vlan routing would happen naturally, but it does not seem to be true.
Thanks for the help!
This is the config that I have on the switch:
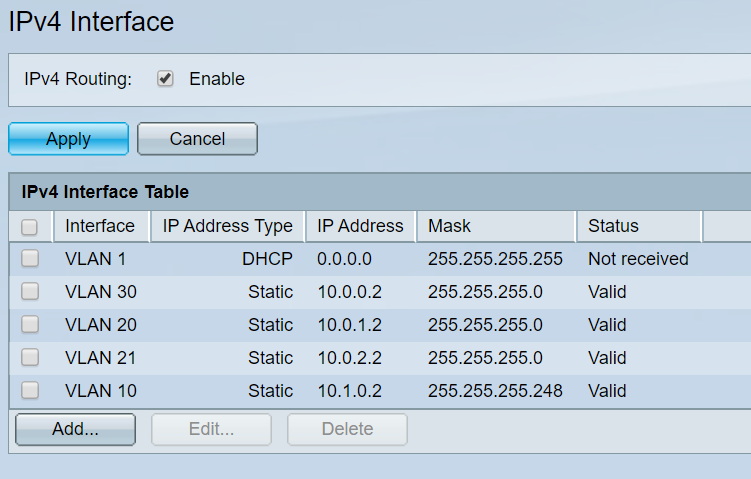
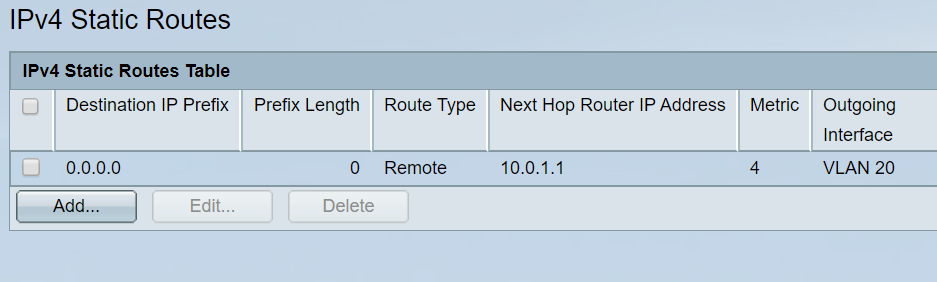
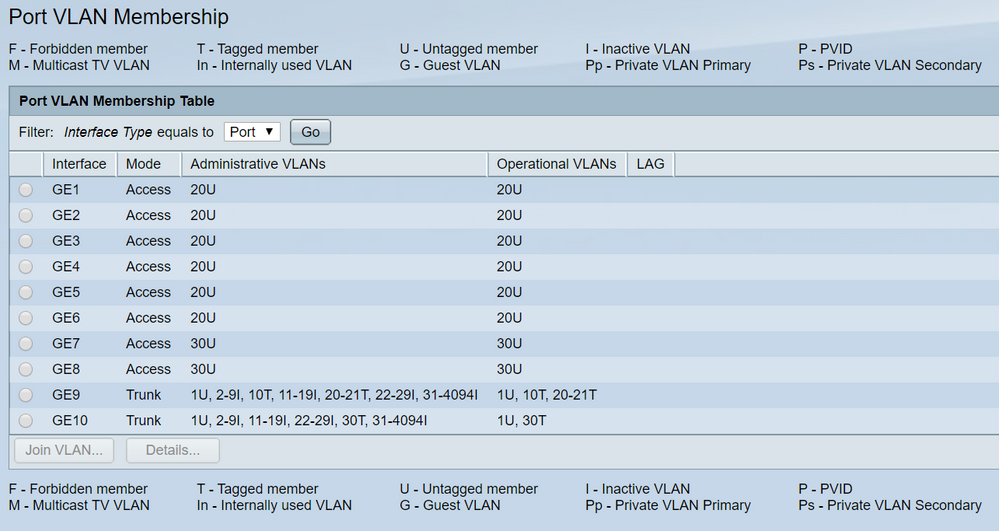
config-file-header switch6a6d71 v2.5.0.83 / RTESLA2.5_930_364_091 CLI v1.0 file SSD indicator plaintext @ ! unit-type-control-start unit-type unit 1 network gi uplink none unit-type-control-end ! vlan database vlan 10,20-21,30 exit voice vlan oui-table add 0001e3 Siemens_AG_phone________ voice vlan oui-table add 00036b Cisco_phone_____________ voice vlan oui-table add 00096e Avaya___________________ voice vlan oui-table add 000fe2 H3C_Aolynk______________ voice vlan oui-table add 0060b9 Philips_and_NEC_AG_phone voice vlan oui-table add 00d01e Pingtel_phone___________ voice vlan oui-table add 00e075 Polycom/Veritel_phone___ voice vlan oui-table add 00e0bb 3Com_phone______________ bonjour interface range vlan 1 hostname switch6a6d71 username fabio password encrypted 8006c3b9215a15248f77214fca75f423a57a98a6 privilege 15 ! interface vlan 10 name mngt ip address 10.1.0.2 255.255.255.248 ! interface vlan 20 name user ip address 10.0.1.2 255.255.255.0 ! interface vlan 21 name wireless ip address 10.0.2.2 255.255.255.0 ! interface vlan 30 name dmz ip address 10.0.0.2 255.255.255.0 ! interface GigabitEthernet1 switchport access vlan 20 ! interface GigabitEthernet2 switchport access vlan 20 ! interface GigabitEthernet3 switchport access vlan 20 ! interface GigabitEthernet4 switchport access vlan 20 ! interface GigabitEthernet5 switchport access vlan 20 ! interface GigabitEthernet6 switchport access vlan 20 ! interface GigabitEthernet7 switchport access vlan 30 ! interface GigabitEthernet8 switchport access vlan 30 switchport trunk native vlan none ! interface GigabitEthernet9 switchport mode trunk ! interface GigabitEthernet10 switchport mode trunk ! exit ip default-gateway 10.0.1.1
- Labels:
-
Small Business Switches
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2020 05:44 AM
Hi,
You need to first decide where you want to perform the inter-VLAN routing, if the necessary IP interfaces for respective VLANs are already configured in Firewall/ Router then you can remove the IP interfaces configured in the Switch (you can assign only one management IP for the switch), in this case switch will act as an layer 2 device; if not, then inter-VLAN routing configuration on the switch is fine. Please make sure you are creating the IP interface for VLANs at one place, either on the Firewall/Router or switch.
Gateway on the NAS device will be the VLAN30 interface IP and similarly devices in each VLAN need to use the respective VLAN IP interface as gateway for inter-VLAN routing. On the SG350 switch you need allow the VLANs (for which you want forward the traffic with Firewall/router) as tagged in trunk port, one VLAN will be native. As per the config, Firewall/ Router IP is 10.0.1.1 (belongs to VLAN 20) so please keep the VLAN 20 as native VLAN in SG350 on the trunk port connected to the Firewall, remaining VLANs can be tagged.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide