- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2014 09:37 AM
Just got a SF200-24 (SLM224GT) in to configure for a small office. According to the product manual and the web gui it should support RADIUS authentication. The switch is running the latest firmware 1.3.5.58. Full logging including debug is enabled.
Radius configuration set to use a local Freeradis setup for testing. After enabling RADIUS as a select authentication method and defining the radius sever settings I go to try it out.However, the switche does not even attempt to send any packet towards the radius server (checked using tcdump on the radius server). Also rebooted the switch to see if that would make any difference, but no. The logs on the switches does not give any indication of any radius attempts either despite debug logging being enabled.
I've also done a quick check to see if 802.1x would work with the radius setup, but it looks like that is failing as well - no radius packets are sent from the switch to the radius server at all.
Can someone confirm if they have go the SF200-24 to work with Raidus and management login and/or 802.1x?
Regards,
Thomas
Solved! Go to Solution.
- Labels:
-
Small Business Switches
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-07-2014 12:05 AM
I got radius authentication up and running in the end. Should have thought of this before, and paid a closer attention to the thread on https://supportforums.cisco.com/thread/2132803 which does highlit the issue.
Radius must be listed before Local under Selected Methods if you are ever to use radius.
For future references, if anyone wonders how to confgure Windows NPS or Freeradius to use Radius auth with the SF/SG series switches:
Freeradius:
The following entry in the /etc/raddb/users file will allow user oladunk to authenticate with the password of mypass12
oladunk Cleartext-Password := "mypass12"
Service-Type = Administrative-User,
cisco-avpair = "shell:priv-lvl=15"
For Windows NPS, the following settings will work as a Network Policy:
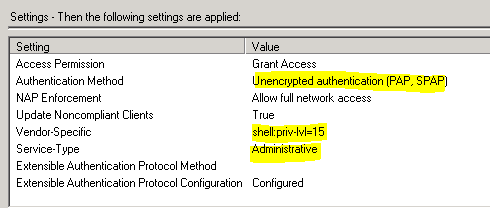
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-07-2014 12:05 AM
I got radius authentication up and running in the end. Should have thought of this before, and paid a closer attention to the thread on https://supportforums.cisco.com/thread/2132803 which does highlit the issue.
Radius must be listed before Local under Selected Methods if you are ever to use radius.
For future references, if anyone wonders how to confgure Windows NPS or Freeradius to use Radius auth with the SF/SG series switches:
Freeradius:
The following entry in the /etc/raddb/users file will allow user oladunk to authenticate with the password of mypass12
oladunk Cleartext-Password := "mypass12"
Service-Type = Administrative-User,
cisco-avpair = "shell:priv-lvl=15"
For Windows NPS, the following settings will work as a Network Policy:

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-07-2014 07:40 AM
Hi Thomas, thanks for the post. All RADIUS/ TACACS posts are very helpful especially when positive result is met. This is always a difficult subject since there's so many servers and such limited testing capability to facilitate everyones needs.
-Tom
Please mark answered for helpful posts
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide