- Cisco Community
- Technology and Support
- Networking
- Switching
- 17.3.5 or 17.6.4 | C9300L-24P-4X-E
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2022 09:53 AM
Looking for an upgrade suggestion for a C9300L-24P-4X-E. The link below suggest 2 different versions (17.3.5, 17.6.4). They will not be doing anything fancy other than L2 switching (I know, its overkill, its what the clients Administration wants). Other than looking at the affected bugs related to both, and choosing the lesser to 2 evils, what other ways would you go about deciding which one to go with?
Solved! Go to Solution.
- Labels:
-
Catalyst 9000
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2022 10:03 AM
- I would just use the latest advisory release : https://software.cisco.com/download/home/286322046/type/282046477/release/Bengaluru-17.6.4
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2022 10:03 AM
- I would just use the latest advisory release : https://software.cisco.com/download/home/286322046/type/282046477/release/Bengaluru-17.6.4
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2022 09:54 AM
You're suggesting to go with 17.6.4 simply based on the release date?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2022 04:56 PM - edited 03-15-2023 08:41 PM
Go with 17.6.4 17.3.5.
Update below.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2022 11:53 AM
Sure i vote for 17.6.4 for stable version
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2022 08:49 PM - edited 11-29-2022 08:50 PM
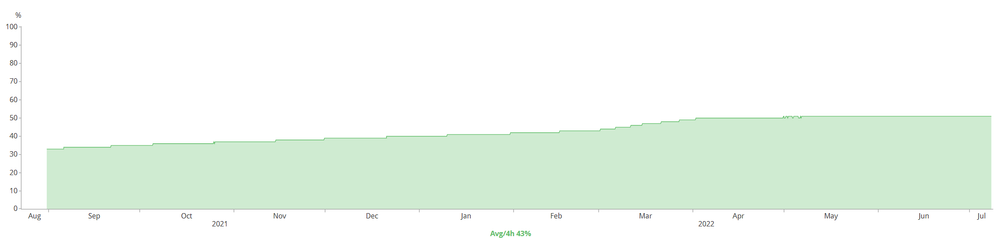
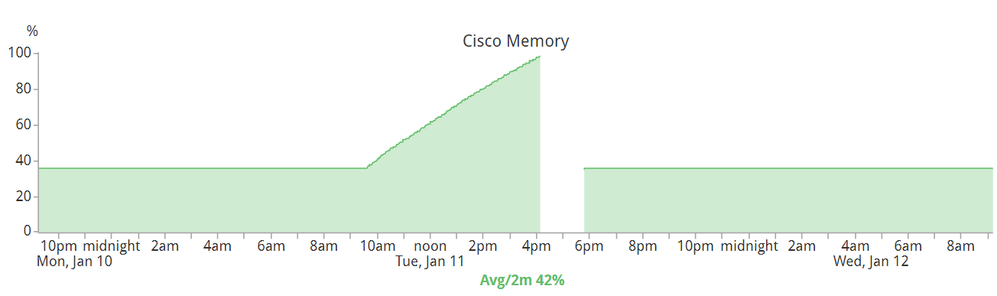
If anyone is brave to even consider 16.12.X, please refer to my "documentation" below: 
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2023 10:37 AM
Hi Leo,
What's your load on these switches and stacked?
Do you have any 9300s running 17.6.4 or 17.3.6 with the same results?
Our deployment is moving away from 3650 edge to 9300 (all POE) around 100 already deployed with routing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2023 03:03 PM
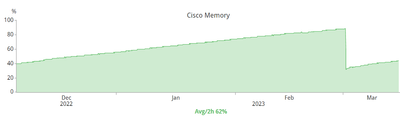
Half of our fleet is on 17.3.5 and the other half is on 17.6.4. Some portion of our 17.6.4 are showing memory leak with the "linux_iosd-imag" process. This process is all about "telemetry" including "SNMP".
Just this morning, at 06:00, I had to reboot a stack of two switches (half full) because of the same issue. That one had an uptime of 25 weeks.
I will be doing more pro-active reboots in the next two weeks.
I am not keen on upgrading to 17.6.5 because there are some bugs I am trying to avoid. One of them is CSCwe54104.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2023 03:07 PM
I'm on the same line with upgrading to the latest and greatest as it's always bleeding edge.
Issue is we are standardizing the IOS everywhere so looking at moving to 17.3.6 code.
Cheers.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2023 05:34 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2023 09:46 PM
Stack of 7 x 9300, IOS-XE 17.6.4, Uptime of 13 weeks before I had to perform a reboot of the entire stack on 01 March 2023. After the reboot, the memory leak continues with the same upward trend.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2023 03:49 AM
Gonna jump in here..even though the thread is a bit dated. We had the same conundrum, go with the 17.6 train or ride out the 17.3. We decided to go the way of 17.6, and have encountered an "unpublished" defect in POE with 9200 and 9300 series gear. After a switch reboots, often we will lose POE to either "some" ports, or all. Opened a TAC case yesterday after upgrading to 17.6.5 on a handful of brand new 9300 UXM switches...found out about the "unpublished" bug. Changed trains to 17.3.6 on a few stacks last night, POE working as it should.
HTH.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-10-2023 09:04 AM
I'm looking at 17.6.x code train for the new GRE features so will keep that in mind with POE devices.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-11-2023 02:49 AM
@Jon Porterwe have confirmed with cisco that the unpublished bug only impacts C9300-48H switches. Whether or not I trust them, that is debatable. I have witnessed the same symptoms on 9200 series as well, same train of code, 17.6.xxx.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide