- Cisco Community
- Technology and Support
- Networking
- Switching
- Access-List
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2013 03:03 AM - edited 03-07-2019 11:26 AM
Hi Everyone,
I need help regarding access-list. I really don't understand the concept of outbound and inbound.
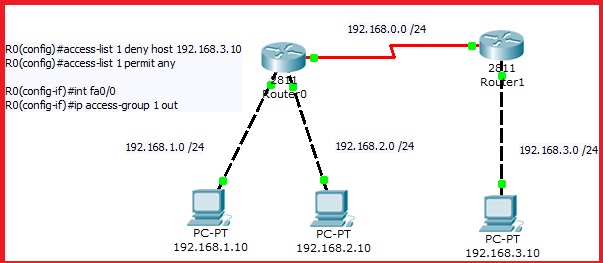
This is working fine, but my question is when i put the access-group in serial interface of router 0 the access list won't work.
Please Advise.
Thanks.
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2013 03:06 AM
Hi,
if you apply it to serial0 then it must be inbound as packets with a source address of 192.168.3.10 are entering this interface not exiting.
But then it will block communication betwen this host and all hosts in the subnets on the fatethernet ports of the left router not just the hosts from the
fastethernet0 interface.
Regards
Alain
Don't forget to rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2013 03:21 AM
Hi,
it all depends of what you want to achieve. if you wanted to block this host from communicating wit the right one on the left router then putting it outbound on f0 is the right way to do even though the packet will be forwarded and then dropped by the ACL.Now if you wanted to block communication with both clients on the left then you could either apply it inbound on s0 or outbound on both fastethernet interfaces. doing it inbound on s0 Would save a routing lookup and frame rewrite on the router as the packet would get dropped before being routed.
Regards
Alain
Don't forget to rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2013 04:19 AM
Hi,
best practice is to put standard ACL as close to destination as possible because if you put it inbound on your router you are going to block some communication you didn't want to.
for example you won't ping your router or manage it via telnet/ssh or http(s) from your host, you won't get no more dhcp addresses for this host too.
Regards
Alain
Don't forget to rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2013 03:06 AM
Hi,
if you apply it to serial0 then it must be inbound as packets with a source address of 192.168.3.10 are entering this interface not exiting.
But then it will block communication betwen this host and all hosts in the subnets on the fatethernet ports of the left router not just the hosts from the
fastethernet0 interface.
Regards
Alain
Don't forget to rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2013 03:14 AM
Thanks for the quick reply, so what would be the standard deny it inbound in se0/0/0 or outbound fa0/0?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2013 03:21 AM
Hi,
it all depends of what you want to achieve. if you wanted to block this host from communicating wit the right one on the left router then putting it outbound on f0 is the right way to do even though the packet will be forwarded and then dropped by the ACL.Now if you wanted to block communication with both clients on the left then you could either apply it inbound on s0 or outbound on both fastethernet interfaces. doing it inbound on s0 Would save a routing lookup and frame rewrite on the router as the packet would get dropped before being routed.
Regards
Alain
Don't forget to rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2013 03:33 AM
One more question, I tried putting this command in Router 1 (right router) and it works.
R1(config)#access-list 1 deny host 192.168.3.10
R1(config)#access-list 1 permit any
R1(config-if)#int fa0/0
R1(config-if)#ip access-group 1 in
Is it the same as :
R0(config)#access-list 1 deny host 192.168.3.10
R0(config)#access-list 1 permit any
R0(config-if)#int serial0/0/0
R0(config-if)#ip access-group 1 in
right? is it proper to deny the host in its own router (which is the Router 1 in this example)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2013 04:19 AM
Hi,
best practice is to put standard ACL as close to destination as possible because if you put it inbound on your router you are going to block some communication you didn't want to.
for example you won't ping your router or manage it via telnet/ssh or http(s) from your host, you won't get no more dhcp addresses for this host too.
Regards
Alain
Don't forget to rate helpful posts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2013 03:19 AM
Ok, I get it now. Thanks again!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2013 08:03 AM
Disclaimer
The Author of this posting offers the information contained within this posting without consideration and with the reader's understanding that there's no implied or expressed suitability or fitness for any purpose. Information provided is for informational purposes only and should not be construed as rendering professional advice of any kind. Usage of this posting's information is solely at reader's own risk.
Liability Disclaimer
In no event shall Author be liable for any damages whatsoever (including, without limitation, damages for loss of use, data or profit) arising out of the use or inability to use the posting's information even if Author has been advised of the possibility of such damage.
Posting
I need help regarding access-list. I really don't understand the concept of outbound and inbound.
Inbound vs. outbound determines when a packet is subjected to a particular ACL. Inbound applies to packets entering the interface. Outbound applies to packets leaving the interface. An interface can have both inbound and outbound ACLs.
Often you can apply the same logical ACL either inbound or outbound, however you often need to be mindful that IP addresses and UDP/TCP port numbers "swap" depending on direction the packet is traveling.
For example, if I want to block traffic between hosts 192.168.1.10 and 192.168.3.10. I might:
(1) block traffic with source IP 192.168.1.10 and destination IP 192.168.3.10
or
(2) block traffic with destination IP 192.168.1.10 and source IP 192.163.3.10
or (ideally) apply both of the above rules.
What's important if I don't use both rules, you need to apply the right rule for the direction of traffic's flow, so for traffic flowing from 192.168.1.10 (source) to 192.168.3.10 (destination) you need the first rule.
That (1st) rule could be applied as the inbound ACL on Router0's Ethernet interface, or outbound on its Serial interface, or inbound on Router1's Serial interface or outbound on its Ethernet interface.
The second rule wouldn't match traffic flowing from 192.168.1.10 to 192.168.3.10, nor would the other direction ACL be applied, e.g. outbound ACL on Router1's Ethernet for this traffic.
If you combined the two rules, it would work inbound or outbound, on any interface, that traffic would flow across between these two hosts.
As you might now see you have many options, even in this simple case, what the ACL might contain, and where it might be applied. So how would you choose?
For performance, you generally want to drop packets as early as possible and you want ACLs often as short as possible. But, also for performance, you need to consider other traffic.
For example, applying rule 1 as inbound on Router0's Ethernet, at first glance, seems better than applying the same rule as outbound on Router1's serial. But, what if 192.168.1.10 was sending almost all its traffic to 192.168.2.10?
Even other considerations might apply. Perhaps you don't have access to one of these routers, say Router1. In that case, rule 2 could be applied inbound on Router0's serial interface.
So if you remember inbound and outbound apply to the direction of traffic flowing across and interface, and ACLs need to account for "swap" addresses (and UDP/TCP ports), hopefully it will make this easier to understand.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2013 07:01 PM
Joseph,
My example is for standard ACL only and your rule is applied in Extended ACL, Great example though. Cheers.
Thank You for putting extra effort in explaining, big help for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2013 07:11 PM
Disclaimer
The Author of this posting offers the information contained within this posting without consideration and with the reader's understanding that there's no implied or expressed suitability or fitness for any purpose. Information provided is for informational purposes only and should not be construed as rendering professional advice of any kind. Usage of this posting's information is solely at reader's own risk.
Liability Disclaimer
In no event shall Author be liable for any damages whatsoever (including, without limitation, damages for loss of use, data or profit) arising out of the use or inability to use the posting's information even if Author has been advised of the possibility of such damage.
Posting
rivanfrank wrote:
Joseph,
My example is for standard ACL only and your rule is applied in Extended ACL, Great example though. Cheers.
Thank You for putting extra effort in explaining, big help for me.
Correct, I did imply using an extended ACL. Same concept with standard ACL except you're much more limited what you can examine, e.g. no destination IP.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide