- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: ACLs to block traffic between interfaces on same cisco router
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2021 08:34 PM - edited 09-28-2021 08:36 PM
Hello,
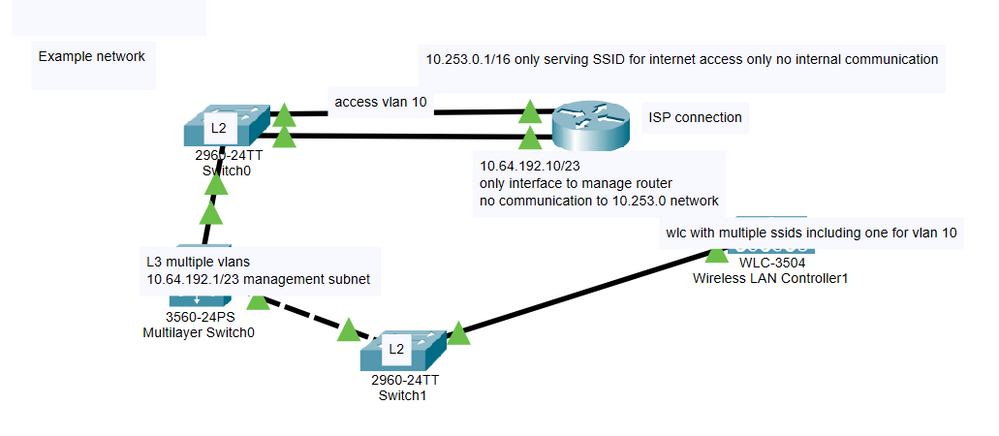
I'm trying to come up with a couple of ACLs to block traffic in the same router from two of its interfaces (if possible). The only purpose of this router is for internet access only that will be used for one of our wlans. One interface is for us to manage it and the only subnet that needs access to the router. No other communication to the router should exist. Below is the a very simplified example. For example, 10.253.0 subnet will be used for one of our wlans and the router is also the dhcp server for this subnet and we will be using public dns servers. The snapshot below is just an example to simplify scenario. For the management example,10.64.192. subnet should be the only subnet with access to manage this router. Also, the traffic between these two subnets should be blocked so 10.253.0.1 should only have access to the internet. and 10.64.192. will be for management only. We don't want users from the this wlan to have any internal access so I'm trying to block traffic both ways. Is this possible using ACLs in the router?
Both connections to the switch from the router are access ports and the gateway for the management address is on a core (L3). The gateway for the wlan is on the router.
I've been playing with packet tracer but im not getting the results i want. this snapshot is simplified i'm not testing it directly from the router, I have desktops to test communication between subnets in my real packet tracer file FYI
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2021 10:37 PM
Hello,
you can use simple access list like in the example below. Traffic from subnet 10.53.0.0/24 to 10.64.192.0/24 is blocked, the rest is allowed:
access-list 101 deny ip 10.253.0.0 0.0.0.255 10.64.192.0 0.0.0.255
access-list 101 permit ip 10.253.0.0 0.0.0.255 any
!
interface GigabitEthernet0/0
description 10_253_0_0_Subnet
ip access-group 101 in
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2021 10:37 PM
Hello,
you can use simple access list like in the example below. Traffic from subnet 10.53.0.0/24 to 10.64.192.0/24 is blocked, the rest is allowed:
access-list 101 deny ip 10.253.0.0 0.0.0.255 10.64.192.0 0.0.0.255
access-list 101 permit ip 10.253.0.0 0.0.0.255 any
!
interface GigabitEthernet0/0
description 10_253_0_0_Subnet
ip access-group 101 in
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2021 04:28 AM
Hello @Georg Pauwen thank you for the quick response, I just noticed I forgot to add the interfaces in this example. Another thing I think I need to clarify is that the router should only have access to what I'm calling the mgmt subnet in this example and the wlan subnet while also not allowing communication between the two. So in your example, if im using g0/0 as the 10.253.0.0/16 this is where I'm placing this acl right? And let's say I use g0/1 as the 10.64.192.0/23 subnet interface do I need to accomplish what I need? Sorry for not being clear hope this can help explaining better
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2021 03:29 AM
Hi
Another option is to create an vrf, if the router supports it, and move the interface for vlan10 and the isp interface into that vrf.
In that way you have separated the router into 2 logical routers with there own routingtables.
/Mikael
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2021 04:31 AM
@mlund Hey thank you I will pass this option to the senior eng and see what he thinks. Unfortunately, I think they want to have the 3 physical interfaces at this moment but it is a good option I appreciate it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2021 06:33 AM
@Georg Pauwen Hey I tested the ACLs and it worked I now have communication between hosts in the same subnet only. I used two acls one for each interface. I appreciate it
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide