- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Basic VLAN setup
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2022 12:10 PM - edited 06-16-2022 12:11 PM
Hi Guys,
I am new to networking. I have a lab with 1 firewall, 1 L2 switch and 4 PC.
So I created 5 VLANS (1,10,20,30,40) in a single firewall interface with DHCP enabled.
What I want to know is, how should I configure the switch so that my switch can get IP from VLAN 1 and all my four PC can get DHCP and internet from each VLAN(10,20,30,40).
I am attaching a firewall interface screenshot.
Also, in my firewall I have configured VLAN1 as Untagged and rest all as Tagged. So that configuration is correct or not?
Solved! Go to Solution.
- Labels:
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2022 01:13 PM
Given that this is for a lab what you describe is reasonable. The advice from BB is reasonable for a live network environment.
If we knew details about the firewall and the switch then we might be able to provide more specific advice. But here is a general description of what you will need to do.
On the firewall:
- configure the interface as a trunked environment. It should support 5 vlans. vlan 1 should be untagged (native vlan), and vlans 10, 20, 30, and 40 should be tagged. Configure IP addresses for each of the vlan subinterfaces (from the output in the original post it appears that this has already been done).
- the firewall will need to be configured for 5 DHCP scopes (one for each of the vlans). Each of the scopes should define the subnet address for the network, the appropriate mask for the network, and the firewall IP of the vlan as the default gateway. The scope also might want to include information about DHCP servers.
- the firewall will provide routing between the vlans. Depending on the firewall there may be configuration needed for this. For example if the firewall were ASA, and if each of the vlan subinterfaces was configured with security level 100 then the ASA would need to enable inter vlan communication. If the various vlans had different security levels then the ASA configuration would be considerably more complex and I do not want to get into that here.
- what I have described so far would allow the firewall to provide routing between the vlans and allow the PCs connected in each vlan to communicate with each other. If you want the PCs to have Internet access then there are several other steps that will be necessary:
- configure the firewall with a default route.
- configure the firewall with address translation for vlans 10, 20, 30, 40. Do not configure address translation for vlan 1.
- configure the firewall with appropriate security policies to protect the inside networks.
On the switch:
- select an interface for connection to the firewall. Configure that interface as a trunk and assure that it will carry the 5 vlans.
- depending on the particular switch being used you may need to explicitly configure vlans 10, 20, 30, and 40.
- select a switch port for use in vlan 10. configure that port as an access port in vlan 10.
- select a switch port for use in vlan 20. configure that port as an access port in vlan 20.
- select a switch port for use in vlan 30. configure that port as an access port in vlan 30.
- select a switch port for use in vlan 40. configure that port as an access port in vlan 40.
- configure a vlan interface for vlan 1. (note that configuring a vlan interface is different from configuring an vlan) and configure this vlan interface to learn its IP using DHCP.
On each PC.
- assure that the PC will learn its IP address using DHCP.
- connect the PC to the appropriate switch port for each vlan.
This should provide you with a working lab environment.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2022 12:20 PM
what Firewall is this ? If the switch port connected to FW is trunk config with VLAN as Native and DHCP config of the switch if the FW acting as DHCP Server switch should able to get IP address.
But I suggest having a switch to be configured as static IP than dynamic to manage easily.
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2022 12:23 PM
Hi,
Thanks for replying. I have not done anything on the switch, that is why I am seeking how exactly to configure the switch?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2022 12:59 PM
Hi,
In your case since the switch is L2, all you need is to assign one static IP to the switch, so you can manage it remotely, be able to make config changes, etc. Also, since you want to use vlan1 for management, that vlan, vlan1 by default exists on the switch. So, all you have to do is the following:
config t
inter vlan1
ip address 10.10.10.1 255.255.255.0 (you can use whatever IP you want. This is just an example)
no sh
Now, since vlan 1 is the Native vlan (untagged) that should already be part of the trunk configuration on the interface that connects the switch to the FW. On the firewall interface connected to the switch, make sure vlan 1 is configured as Native vlan, so it matches the switch.
All the other vlans (10,20,30,40) should be configured as part of the trunk port on the switch and the firewall.
Also, on the firewall configure the interface with one IP in vlan 1. Example:
ip address 10.10.10.2 255.255.255.0 (Make sure the IP is in the same subnet as the switch).
If all is configured correctly, you should be able to ping the firewall from the switch and viseversa. Configure the FW with DHCP scopes for vlans 10,20, 30, and 40.
Now, you also need a default gateway on the switch pointing to the FW IP address, so it can be reached remotely. It should look something like this
config t
ip default-gateway 10.10.10.2 (assuming .2 is the IP you assign to the firewall).
Now, test some of the vlans with PCs as well as vlan1.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2022 01:04 PM
Hi,
That was a pretty clear explanation. I will try that and come back with the update. Thanks a lot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2022 01:41 PM
Hi,
Keep in mind that we don't know anything about your FW, and are not familiar with it. So, I am assuming you know how to navigate the FW changes.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2022 01:13 PM
Given that this is for a lab what you describe is reasonable. The advice from BB is reasonable for a live network environment.
If we knew details about the firewall and the switch then we might be able to provide more specific advice. But here is a general description of what you will need to do.
On the firewall:
- configure the interface as a trunked environment. It should support 5 vlans. vlan 1 should be untagged (native vlan), and vlans 10, 20, 30, and 40 should be tagged. Configure IP addresses for each of the vlan subinterfaces (from the output in the original post it appears that this has already been done).
- the firewall will need to be configured for 5 DHCP scopes (one for each of the vlans). Each of the scopes should define the subnet address for the network, the appropriate mask for the network, and the firewall IP of the vlan as the default gateway. The scope also might want to include information about DHCP servers.
- the firewall will provide routing between the vlans. Depending on the firewall there may be configuration needed for this. For example if the firewall were ASA, and if each of the vlan subinterfaces was configured with security level 100 then the ASA would need to enable inter vlan communication. If the various vlans had different security levels then the ASA configuration would be considerably more complex and I do not want to get into that here.
- what I have described so far would allow the firewall to provide routing between the vlans and allow the PCs connected in each vlan to communicate with each other. If you want the PCs to have Internet access then there are several other steps that will be necessary:
- configure the firewall with a default route.
- configure the firewall with address translation for vlans 10, 20, 30, 40. Do not configure address translation for vlan 1.
- configure the firewall with appropriate security policies to protect the inside networks.
On the switch:
- select an interface for connection to the firewall. Configure that interface as a trunk and assure that it will carry the 5 vlans.
- depending on the particular switch being used you may need to explicitly configure vlans 10, 20, 30, and 40.
- select a switch port for use in vlan 10. configure that port as an access port in vlan 10.
- select a switch port for use in vlan 20. configure that port as an access port in vlan 20.
- select a switch port for use in vlan 30. configure that port as an access port in vlan 30.
- select a switch port for use in vlan 40. configure that port as an access port in vlan 40.
- configure a vlan interface for vlan 1. (note that configuring a vlan interface is different from configuring an vlan) and configure this vlan interface to learn its IP using DHCP.
On each PC.
- assure that the PC will learn its IP address using DHCP.
- connect the PC to the appropriate switch port for each vlan.
This should provide you with a working lab environment.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2022 05:18 AM
Thank you Rick and Reza for your great explanation. My lab is working now and the PC is getting the internet.
But there is a slight problem: the PCs connected to their respective VLAN can only access the firewall on their VLAN gateway.
I want every PC to be able to access the firewall from the VLAN 1 IP i.e. 10.4.247.1, which is an untagged port. How can I achieve that?
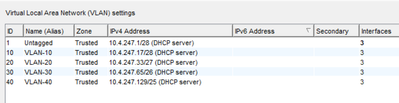
For example, if you refer to the screenshot, a PC in VLAN 40 can only access the firewall with 10.4.247.129 and is not able to reach VLAN1 IP 10.4.247.1.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2022 09:15 AM
I am glad that our suggestions have pointed you in the right direction and that your lab is now working.
I have a couple of questions about your follow up question:
1) Why would the PC in vlan 40 need to access the vlan 1 interface of the firewall? The PC would certainly use the vlan 40 interface address of the firewall to be able to access the Internet or to access devices in the other vlans. The PC could access any firewall functions or resources using the vlan 40 interface address of the firewall. So why does the PC need to access the vlan 1 interface of the firewall?
2) How is the PC in vlan 40 attempting to access the vlan 1 interface address of the firewall? If it is attempting to ping (for example) most firewalls have a default security policy that they do not respond to ping on an interface if the source of the ping is not in the local subnet of the interface. So a ping from the PC in vlan 40 to the firewall address on vlan 1 would not work because of the default security policy.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2022 09:41 AM
Hi Rick,
Thanks again for your reply.
So for point number 1, since this is my lab, so I only want to test if PC in different VLANs can access FW through VLAN1 or not.
For point number 2, yes I have allowed the ping in the internal network in the FW, still, I am not able to ping VLAN1 from any other VLAN.
Lastly, before closing this topic, I have a question. What I have read is that Tagged or trunk is for traffic with multi VLANs and Untagged or Access is for a single VLAN. So how come this lab setup is working when we have created VLAN1 in FW, which is connected to switch as Untagged, even when four different VLANs are passing through it? Correct me please if something I wrote is wrong.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2022 09:57 AM
This part of what you say is exactly correct "What I have read is that Tagged or trunk is for traffic with multi VLAN". When there are multiple vlans on a trunk, most of the vlans will send Ethernet frames with a tag indicating the particular vlan that this frame belongs to. This allows the receiving device to forward the frame into the correct vlan.
This part of what you say is slightly not correct "Untagged or Access is for a single VLAN". You seem to believe that there is a single situation for sending untagged traffic (Access port). But there are actually 2 situations. When a trunk is carrying multiple vlans it is possible that one of the vlans will send Ethernet frames that do not have a tag.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2022 10:43 AM
Thanks, Rick. That clears it up. Yes, I believed only tagged traffic can pass through the trunk port. Thanks a lot for that explanation.
Lastly, what about in my lab, is it possible for different VLAN PC to access FW through VLAN1?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2022 06:21 PM
You are welcome. I am glad that the concepts of trunking and the native vlan, which is a single vlan in the trunk where the Ethernet frames do not have tagging information, is clear.
As far as the question of a PC on a different vlan accessing the firewall through vlan 1, I have attempted to explain it, and perhaps can try to different way of approaching the question. Perhaps I am not understanding what you are really trying to ask. If I take the question very literally perhaps it is asking if a PC in vlan 40 can go through vlan 1 to access the firewall? The answer to that is that no a PC in vlan 40 can not go through vlan 1 to access the firewall.
Perhaps it is asking if there is a way for a PC in vlan 40 to go through vlan 1 to access the firewall? The answer to this is yes, but it would require a very different setup from what you describe in the original post. If you want the PC in vlan 40 to access the firewall through vlan 1 this is what you would need:
- the switch would have to operate as a layer 3 switch with ip routing enabled.
- the switch would have the 5 vlans configured, with appropriate ports configured as access ports in each of the vlans.
- the switch would have vlan interfaces for each of the vlans, with an appropriate IP address and mask configured on the vlan interface.
- this would allow the switch to do inter vlan routing.
- the switch would need a static default route with the firewall vlan 1 IP address as the next hop.
- the firewall would not need the vlan subinterfaces for the other vlans.
- the firewall would need routes for the 4 vlan subnets with the switch vlan 1 IP address as the next hop.
- in this configuration each of the vlan PCs would access the firewall through vlan 1.
If this still does not resolve your question then please explain what you are trying to access on the firewall from the vlan PC.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2022 10:55 PM
Hi Rick,
Yes, you understood the question right. I was just wondering if there is any way to access FW from different VLAN through VLAN1. I got most of the points you explained, except two points.
- the firewall would not need the vlan subinterfaces for the other vlans.
Does it mean that I don't need to create/configure any VLAN on the firewall?
- the firewall would need routes for the 4 vlan subnets with the switch vlan 1 IP address as the next hop.
If I am not creating any VLAN on the firewall and the PCs are connected directly to the L3 switch. Why do I need to create the routes for PCs on FW? My point is how come creating a route of PCs in FW will do anything if the PCs are not even connected to FW? Won't the default gateway of PCs which will be their VLANs IP will serve as their default route? Why create on FW then?
PS: Please bear with me if my question sounds stupid to you 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2022 11:49 AM
First let me say that your question does not sound stupid. It sounds like a question from someone who is learning but still has very incomplete understanding of layer 3 forwarding/IP routing. So I am happy to try to answer your questions.
As for the 2 points let me try to clarify.
There are 2 very different approaches to implementing the network that you describe, in which there are 5 vlans connected to a switch, of which 4 vlans are for user devices, and there is a switch and there is a firewall.
One approach is what you described in the original post. In this approach the important parts are that the switch operates as a layer 2 switch. The connection from switch to firewall operates as a trunk carrying all 5 vlans. And the routing between vlans is done on the firewall. In this approach the firewall needs vlan interfaces for the 5 vlans.
The other approach is what I described in my response. In this approach the important parts are that the switch operates as a layer 3 switch. The connection from switch to firewall operates not as a trunk carrying all 5 vlans, but as a single access vlan (no trunk) carrying only vlan 1. And the routing between vlans is done on the switch. In this approach the firewall does not need any vlans.
So in one approach the firewall does need vlans and in the other approach the firewall does not need vlans. Either approach can work. You can choose one or the other.
Your other question is interesting "Why do I need to create the routes for PCs on FW?" Let me try to explain it in this way: Let us assume that there is a PC in vlan 40. Perhaps it has IP address 10.4.247.130 and its gateway is 10.4.247.129 which is the switch vlan interface. The switch then forwards the IP packet to the firewall. Now the firewall wants to send a response to the PC. But how does the firewall know where is network 10.4.247.128? If the firewall does not have a route for that subnet then all it has is its default route, and that would not get it back to the PC. Remember that in the first approach the subnet for vlan 40 is a locally connected subnet. But in the second approach the subnet is remote, and to reach a remote subnet the firewall must have a route for it.
Rick
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide