- Cisco Community
- Technology and Support
- Networking
- Switching
- Can't Access GUI
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Can't Access GUI
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2019 09:49 AM
After I create a VLAN i can no longer access the GUI.
port 1 - trunk connected to router
port 2 - access, PC
The switch is connected to an Edgerouter.
I'm sure it's something simple, but I'm new to VLANs and can't figure it out.
- Labels:
-
LAN Switching
-
Other Switches
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2019 10:09 AM
Hi @Rduhb,
By default, all ports of a switch belong to vlan 1. If you create a new vlan and associate it with the port where you are connected, you will no longer be part of vlan 1, so you will lose connection. If you have access to the switch, try changing your connection to a port that remains in the vlan. You could also try to connect by console to check what happened.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2019 06:15 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2019 06:29 PM
As stated, by default all switch ports are assigned to vlan 1 which is the native vlan.
The reason you can’t access the GUI from the pc on your access port is because they are in different vlans. It’s logically the same as having two different switches, one with the GUI attached and another separate switch with your pc attached.
If you create a new vlan and want to access the GUI from a PC on an access port in the new vlan, you must create an interface on that vlan and assign it an IP address on the same subnet as the pc.
Switch#(config)>interface vlan (number of PC vlan)
ip address x.x.x.x y.y.y.y
then enable http access on that vlan.
Hopefully that clears it up for you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2019 07:13 PM
Thanks for the help. And sorry for the remedial VLAN questions. But I thought that a port NOT in a VLAN I created is by default in the default VLAN. And shouldn’t I have access to the GUI by plugging into one of the ports on the default VLAN? I obviously have a lot more to learn about VLANS. 😀
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2019 09:02 PM - edited 09-21-2019 09:23 PM
Don't worry about asking basic questions, we all have to start somewhere and wrapping your mind around the concept of vlans can be challenging coming from the world of non managed switches.
When people say "the default vlan," they're almost always referring to vlan1. The reason that most people get confused is that they think of the vlan 1 as being this special thing that is like any other vlan, but in reality it isn't. In reality vlan 1 is the vlan you're used to dealing with on non-managed switches. In fact, if you take your cisco switch with the default, out-of-the-box config and connect it to any other non managed switch you could buy at an office supply store, all ports on both switches will be in vlan 1. For now, think of vlan 1 as no vlan at all.
Now... to access the GUI you had to set an IP address on the switch. If you do a show run and look at the config, you'll see the ip addess you set under...
interface Vlan1
This interface is not a physical port on the switch, rather a virtual interface that is attached to "the default vlan" and all ports not configured as access or trunk ports are part of this vlan. That is why you could access the GUI from any port other than the one you set as an access port for your PC.
The easiest way to think about vlans is dividing your single switch up into differant individual switches that operate independantly. In fact, you could accomplish almost the same thing by using multiple unmanaged switches instead of vlans. The main purpose of vlans is to enable us to conserve resources by reducing the number of switchs we need and also be able to reduce the amount of cabling we need in our facility. When used in conjunction with routers or firewalls, vlans reduce the number of physical interfaces we need on these devices. Imagine a large network with 50 network segments. Without vlans, you would need at least one switch for every segment and either a router with at least 51 physical interfaces or 50 individual 2 interface routers. From a cabling perspective, imagine you had two server closets and you needed to get network traffic between those two closets for those 50 network segments. Without vlans, you would have to run 50 cables between the closets and have at least 100 switches!
So hopefuly, that explains vlan 1, the "default vlan," but what about the other vlans...
Lets take your example. By creating another vlan (we'll call it vlan 2 for now since you didn't specify the vlan number you created) you now effectivly have two switches. One switch operates on "the defaul vlan" and the other on vlan 2. Any ports that you don't issue the switchport access vlan X command on are part of the vlan 1 switch and any ports you make access ports on vlan 2 are part of the vlan 2 switch.
Now what about the switch's IP address that you assigned? That IP address is attached to a virtual interface in vlan 1. The virtual interface isn't a physical port on the switch, rather it is an interface that the switch itself can use to have access to a specific vlan. This is why your PC could get to the switch's GUI on any port but the port you made an access port on vlan 2. Vlan 2 has no access to vlan 1 because it is logically a differant switch and the switch itself has no way of communicating with a PC on vlan 2 because it doesn't have an interface to connect it to vlan 2.
If you wanted to access the GUI from your access port on vlan 2, you would need to create a virtual interface on vlan 2 and give the switch an IP address on that subnet. For example...
Switch(config)#interface vlan 2
Switch(config-if)#ip address x.x.x.x y.y.y.y
Switch(config-if)#no shutdown
Switch(config-if)#exit
Now the switch would have an IP address on vlan 2 with which it could communicate with your PC on it's access port in the same vlan. One note here... I never use the GUI on any Cisco device so I'm not totally sure but I believe the GUI is accessible from all vlans on the switch as long as the switch has an interface with a valid IP on that vlan. If that is the case, you should now be able to access the GUI using the IP address assigned to interface vlan 2 from you PC on an access port on vlan 2.
Hopefully this info helps clear things up a bit.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2019 06:22 AM
Chris,
I greatly appreciate the thorough explanation. This help tremendously. Next I have to start learn to configure via CLI.
R.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2019 11:10 AM
Glad I was able to help out.
You should defiantly learn to configure via CLI. The GUI on Cisco hardware is extremely limited because they focus on CLI. Once you learn it, you will find that it is faster and makes more sense than any GUI ever could.
The only time I use any type of Cisco GUI is ASDM on the ASAs and even then, I don't use it to configure anything. It has some helpful real-time graphs and charts that can show you lots of information about what the ASA is up to and what's going on as far as bandwidth per interface and the like.
If you don't have a cisco console cable or a serial port on your computer, I would defiantly suggest getting a console cable and a USB to serial adaptor for your PC.
In the mean time, you can still learn CLI. You would just first have to setup an IP and enable telnet access like you do now with the GUI, then you could use putty or telnet on your PC to access the command line.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 07:39 AM
Thanks again!! I ordered the RS232 to USB adapter yesterday.
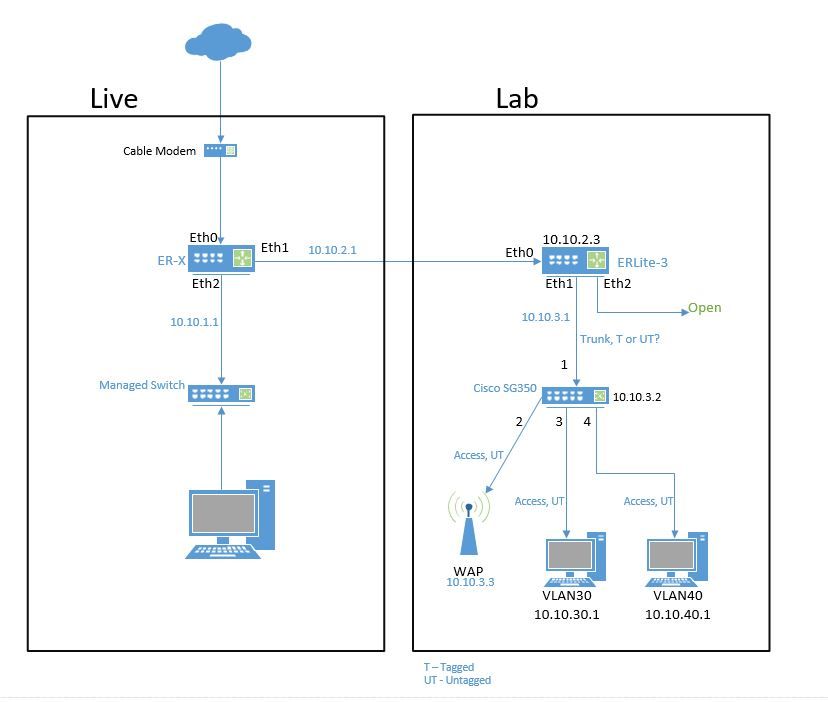
So, the reason for my questions is I have setup a lab environment to learn more about configuring an EdgeRouter and Cisco switch. My setup is below. I think have a grasp on the VLANs, but still battling issues with internet access through the AP. The AP supports VLANs and multiple SSIDs. I'm going slow and documenting what works and what doesn't and understanding the why's. I pretty sure my problem is incorrect trunking and tagging of the ports. Lots to learn.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 08:41 AM
This looks like a reasonable set up. To address your question about tagged or untagged: you are correct that devices connecting to the switches should be untagged. The trunk between switches can carry one vlan as untagged and all other vlans are carried as tagged.
Am I correct that the 10.10.2.0 link is just a routed link? Am I correct in assuming that 10.10.3.0 is a vlan? So your lab will have 3 vlans? What will be doing the routing between these vlans?
A couple of things to keep in mind:
- unless you plan to do address translation on the router in the lab then the router in the live part of the network will need to have routes for 10.10.30.0 and 10.10.40.0. This could be accomplished using a dynamic routing protocol or by using static routes.
- the router in the lab will need a default route pointing at the live part of the network. This could be accomplished using a dynamic routing protocol or by using a static route.
- if you want your devices in the lab to access the Internet then you will need to translate their addresses. The logical place to do this would be the router in the live part of the network.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 10:11 AM
The EdgeRouter allows me to create separate LANs. So I created 10.10.2.0 on eth1 of the first router to supply the other EdgeRouter in my lab. DHCP on the live router assigned the lab router 10.10.2.3. I created another LAN, 10.10.3.0, on eth1 of the lab router to connect to the Cisco SG350. DHCP on the lab router assigned 10.10.3.2 to the Cisco switch. It also assigned 10.10.3.3 to the WAP. I created VLANs 30 and 40 for ports 3 and 4 respectively on the switch and the lab router. DHCP was setup on the lab router to assign addresses to devices in VLAN 30 and 40. I actually had everything working fine until I connected to the WAP. Somehow I lost access to the WAP GUI. I gambled and changed the trunk to tagged (or untagged) and lost access to everything. :-) Reset the switch and started over. Needless to say, I've reset the switch several times.
For the most part I've been configuring everything while connected to the "Live" portion of my setup. I switch to the lab environment to test configs. One way I test is to create an SSID for VLAN 30 and and an SSID for VLAN 40. Connecting to one of those networks allows me to communicate with the device in that VLAN and not the other. And I had internet access and access to the WAP GUI until I screwed something up. But I'm learning.
By the way, you mentioned "...trunk between switches...". What about the connection from the switch to the router? That should be configured as a trunk/tagged also, right?
THANKS FOR THE HELP!!!!! I'm going to do MORE reading on routing and switching.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 11:50 AM
My guess is that you couldn't access the WAP GUI because the management VLAN of the WAP is set to 1. You may or may not be able to change that.
If the WAP supports changing the management VLAN, you could assign it to either VLAN 30 or 40 and access it's GUI from one of those two vlans. If it doesn't, you'll have to use something called the native vlan on your trunk port to the WAP. The native vlan is basically which VLAN will any untagged traffic be assigned to.
You're setup should be something like this...
You have sub interfaces on the lab router for VLAN 30 and 40 that are tied to a single physical interface. That interface connects to the switch using a trunk that allows at least vlan 30 and 40. You would then have a trunk link to your WAP carying VLAN 30 and 40 for each wireless network and depending on weather you can change the management vlan of the WAP, perhaps also specify the native vlan of either 30 or 40 so that you can still manage the WAP from one of those vlans.
You could leave the WAP in vlan 1 and do what's called out-of-band management. That basically means that neither vlan 30 or 40 would be able to access the WAP's GUI and you would have to have a third PC on the default vlan to manage it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2019 10:36 AM
You told us that at one point " I actually had everything working fine until I connected to the WAP." Did that include successful communication between vlan 30 and 40? Or were those configured later? If vlan 30 and 40 were not able to communicate with each other were they able to communicate with 10.10.2 or 10.10.3? Was DHCP successfully assigning IP addresses to devices in vlans 30 and 40? One possible explanation for problems in communicating for vlans 30 and 40 might be problems in the configuration of their default gateway.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2019 08:16 PM
There are several things that we do not know about this environment and that makes it difficult to give good advice. Please provide clarification about these items:
- what platform is this running on?
- is this switch a layer 2 switch or a layer 3 switch (with ip routing enabled)?
- you indicate that the connection to the edge router is a trunk. Does this trunk carry all of the vlans?
- does the edge router have subinterfaces configured for each of the vlans on the switch?
- when you created the new vlan did you configure just the layer 2 vlan or did you configure the layer 2 vlan and the layer interface vlan x?
HTH
Rick
Rick
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide