- Cisco Community
- Technology and Support
- Networking
- Switching
- Cannot get DHCP address through multiple switches
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2013 05:30 AM - edited 03-07-2019 04:44 PM
Problem:
A device connected to vlan 102 on Procurve 5406zl switch cannot communicate with Cisco ASA 5510; therefore, cannot get DHCP address.HELP!
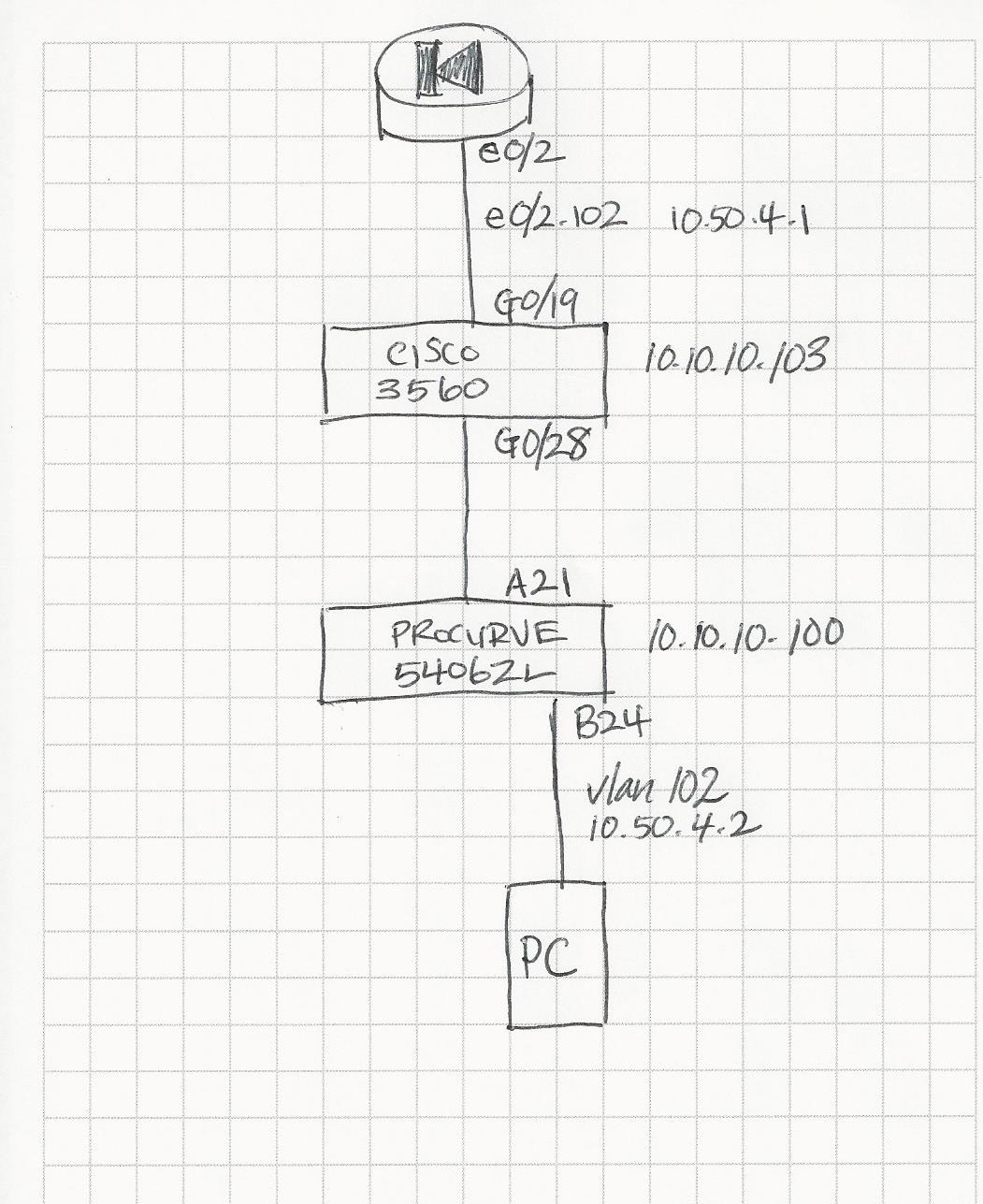
HP Procurve 5406zl:
hostname "Admin"
module 1 type j8705a
module 2 type j8702a
time daylight-time-rule continental-us-and-canada
time timezone -360
ip routing
interface A21
name "trunk to 2404"
exit
interface B24
name "AP-03"
exit
no snmp-server enable
snmp-server location "Administration Building"
router rip
redistribute connected
exit
vlan 1
name "DEFAULT_VLAN"
no untagged B1-B24
untagged A1-A20,A22-A24
tagged A21
ip address 10.10.10.100 255.255.0.0
ip rip 10.10.10.100
exit
vlan 102
name "WIRELESS_admin"
untagged B1-B24
tagged A21
ip address 10.50.4.2 255.255.255.0
ip helper-address 10.50.4.1
exit
spanning-tree
Cisco 3560 switch:
version 12.2
no service pad
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
!
hostname 2404_patch_2
!
enable secret 5 EDIT!
enable password EDIT!
!
no aaa new-model
clock timezone UTC -6
clock summer-time UTC recurring
system mtu routing 1500
ip subnet-zero
ip routing
!
!
!
!
no file verify auto
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
vlan dot1q tag native
!
interface GigabitEthernet0/1
!
interface GigabitEthernet0/2
!
interface GigabitEthernet0/3
!
interface GigabitEthernet0/4
!
interface GigabitEthernet0/5
!
interface GigabitEthernet0/6
!
interface GigabitEthernet0/7
!
interface GigabitEthernet0/8
!
interface GigabitEthernet0/9
!
interface GigabitEthernet0/10
!
interface GigabitEthernet0/11
!
interface GigabitEthernet0/12
!
interface GigabitEthernet0/13
!
interface GigabitEthernet0/14
!
interface GigabitEthernet0/15
!
interface GigabitEthernet0/16
!
interface GigabitEthernet0/17
!
interface GigabitEthernet0/18
!
interface GigabitEthernet0/19
description Trunk to Cisco ASA 5510
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/20
!
interface GigabitEthernet0/21
!
interface GigabitEthernet0/22
!
interface GigabitEthernet0/23
!
interface GigabitEthernet0/24
!
interface GigabitEthernet0/25
!
interface GigabitEthernet0/26
!
interface GigabitEthernet0/27
!
interface GigabitEthernet0/28
description Trunk to Admin
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface Vlan1
ip address 10.10.10.103 255.255.0.0
!
ip classless
ip http server
!
snmp-server community public RO
!
control-plane
!
!
end
CISCO ASA 5510:
ASA Version 8.0(2)
!
hostname ciscoasa
domain-name default.domain.invalid
enable password EDIT! encrypted
names
name 10.10.10.70 S2_server description S2 web server
name 8.8.8.8 GOOGLE_DNS description Google's DNS server
!
interface Ethernet0/0
nameif outside
security-level 0
ip address EDIT
!
interface Ethernet0/1
no nameif
no security-level
no ip address
!
interface Ethernet0/1.5
vlan 5
nameif DOMAIN
security-level 100
ip address 10.50.5.1 255.255.255.0
!
interface Ethernet0/1.99
vlan 99
nameif HP_MGMT
security-level 100
ip address 10.50.6.1 255.255.255.0
!
interface Ethernet0/1.100
vlan 100
nameif WIRED
security-level 100
ip address 10.50.2.1 255.255.255.0
!
interface Ethernet0/1.101
vlan 101
nameif WIRELESS
security-level 100
ip address 10.50.3.1 255.255.255.0
!
interface Ethernet0/2
no nameif
no security-level
no ip address
!
interface Ethernet0/2.1
vlan 1
nameif S2
security-level 100
ip address 10.10.10.1 255.255.0.0
!
interface Ethernet0/2.102
vlan 102
nameif S2-ADMIN
security-level 100
ip address 10.50.4.1 255.255.255.0
!
interface Ethernet0/3
nameif temp
security-level 100
ip address 10.50.1.1 255.255.255.0
!
interface Management0/0
nameif management
security-level 100
ip address 10.50.0.1 255.255.255.0
management-only
!
passwd EDIT! encrypted
boot system disk0:/asa802-k8.bin
ftp mode passive
clock timezone CST -6
clock summer-time CDT recurring
dns server-group DefaultDNS
domain-name default.domain.invalid
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
pager lines 24
logging enable
logging asdm debugging
logging mail warnings
logging class auth mail debugging
mtu outside 1500
mtu temp 1500
mtu S2 1500
mtu management 1500
mtu WIRELESS 1500
mtu DOMAIN 1500
mtu WIRED 1500
mtu HP_MGMT 1500
mtu S2-ADMIN 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
icmp deny any outside
asdm image disk0:/asdm-602.bin
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (temp) 1 0.0.0.0 0.0.0.0
nat (WIRELESS) 1 0.0.0.0 0.0.0.0
nat (DOMAIN) 1 0.0.0.0 0.0.0.0
nat (WIRED) 1 0.0.0.0 0.0.0.0
static (WIRELESS,DOMAIN) 10.50.3.0 10.50.3.0 netmask 255.255.255.0
static (DOMAIN,WIRELESS) 10.50.5.0 10.50.5.0 netmask 255.255.255.0
static (WIRELESS,HP_MGMT) 10.50.3.0 10.50.3.0 netmask 255.255.255.0
static (WIRELESS,S2) 10.50.3.0 10.50.3.0 netmask 255.255.255.0
static (DOMAIN,S2) 10.50.5.0 10.50.5.0 netmask 255.255.255.0
static (HP_MGMT,WIRELESS) 10.50.6.0 10.50.6.0 netmask 255.255.255.0
static (WIRELESS,S2-ADMIN) 10.50.3.0 10.50.3.0 netmask 255.255.255.0
static (S2-ADMIN,WIRELESS) 10.50.4.0 10.50.4.0 netmask 255.255.255.0
static (S2,WIRELESS) 10.10.0.0 10.10.0.0 netmask 255.255.0.0
static (S2,DOMAIN) 10.10.0.0 10.10.0.0 netmask 255.255.0.0
route outside 0.0.0.0 0.0.0.0 EDIT
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 10.50.3.0 255.255.255.0 WIRELESS
http 10.50.0.0 255.255.255.0 management
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
no crypto isakmp nat-traversal
telnet 0.0.0.0 0.0.0.0 management
telnet timeout 5
ssh timeout 5
console timeout 10
management-access temp
dhcpd dns 10.50.5.3 GOOGLE_DNS
!
dhcpd address 10.50.1.50-10.50.1.254 temp
dhcpd enable temp
!
dhcpd address 10.10.2.50-10.10.2.254 S2
dhcpd enable S2
!
dhcpd address 10.50.0.2-10.50.0.10 management
dhcpd enable management
!
dhcpd address 10.50.3.50-10.50.3.254 WIRELESS
dhcpd enable WIRELESS
!
dhcpd address 10.50.5.50-10.50.5.254 DOMAIN
dhcpd enable DOMAIN
!
dhcpd address 10.50.2.50-10.50.2.254 WIRED
dhcpd enable WIRED
!
dhcpd address 10.50.4.50-10.50.4.254 S2-ADMIN
dhcpd enable S2-ADMIN
!
threat-detection basic-threat
threat-detection statistics access-list
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
!
service-policy global_policy global
username admin password EDIT! encrypted privilege 15
prompt hostname context
Cryptochecksum:EDIT!
: end
asdm image disk0:/asdm-602.bin
no asdm history enable
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2013 06:46 AM
It might be helpful if you would post the output of show interface trunk from the 3560.
I would suggest creating the layer 2 vlan on the 3560. You do not necessarily need to assign ports to it, but create vlan 102.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2013 06:30 AM
Hi,
connect a PC with an IP address assigned manually to 10.50.4.x/24 to the port B24 on your HP switch.
Then try to to the ASA IP address 10.50.4.1 from it.
If you got a response, the VLAN is OK and you'vegot some problem with the DHCP configuration.
If you don't get any response, try "arp -a" on your PC.
And if you can see the ARP enry for your ASA, there is still no VLAN problem.
If there is no ARP entry, you need to check your VLAN 102.
Issue "sh int Gi0/28 switchport" on you Cisco switch to check if the port is really trunking.
If not, try to add
"int Gi 0/28
switchport nonegotiation"
to your config.
When you issue "sh mac add xxxx.xxxx.xxxx" where xxxx.xxxx.xxxx it the MAC address of your PC NIC, you should be able to see it behind the Gi 0/28 port within VLAN 102.
You can repeat the same for the ASA MAC address assigned to 10.50.4.1 subinterface.
Again, it should be visible on port Gi 0/19 within VLAN 102.
(don't forget though you need some traffic sent from the devices to fill the MAC address entries on your Cisco switch, there is 5 minute age timer.)
Best regards,
Milan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-22-2013 06:54 AM
I do not have much experience with ProCurve but assume that it treats ip helper-address similar to the way that Cisco does. And in that case you do not need ip helper-address configured in vlan 102 of the ProCurve. The PC will send its DHCP request as a broadcast, and assuming that the vlan is correctly configured and assuming that the turnking is working then the broadcast request will arrive at the subinterface of the ASA where a corresponding DHCP scope is configured.
Could you post the output of show vlan from the 3560 switch? I am wondering if the swtich will need to configure the layer 2 vlan 102 for it to be transported over the trunk.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-26-2013 04:37 AM
2404_patch_2#sh vl
VLAN Name Status Ports
---- -------------------------------- --------- ------------------------------
1 default active Gi0/1, Gi0/2, Gi0/3, Gi0/4
Gi0/5, Gi0/6, Gi0/7, Gi0/8
Gi0/9, Gi0/10, Gi0/11, Gi0/12
Gi0/13, Gi0/14, Gi0/15, Gi0/16
Gi0/17, Gi0/18, Gi0/20, Gi0/21
Gi0/22, Gi0/23, Gi0/24, Gi0/25
Gi0/26, Gi0/27
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------
1 enet 100001 1500 - - - - - 0 0
1002 fddi 101002 1500 - - - - - 0 0
1003 tr 101003 1500 - - - - - 0 0
1004 fdnet 101004 1500 - - - ieee - 0 0
1005 trnet 101005 1500 - - - ibm - 0 0
Remote SPAN VLANs
------------------------------------------------------------------------------
Primary Secondary Type Ports
------- --------- ----------------- ------------------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-26-2013 04:42 AM
2404_patch_2#sh int g0/28 switchport
Name: Gi0/28
Switchport: Enabled
Administrative Mode: trunk
Operational Mode: trunk
Administrative Trunking Encapsulation: dot1q
Operational Trunking Encapsulation: dot1q
Negotiation of Trunking: On
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Administrative Native VLAN tagging: enabled
Voice VLAN: none
Administrative private-vlan host-association: none
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk Native VLAN tagging: enabled
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk private VLANs: none
Operational private-vlan: none
Trunking VLANs Enabled: ALL
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Protected: false
Unknown unicast blocked: disabled
Unknown multicast blocked: disabled
Appliance trust: none
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2013 06:46 AM
It might be helpful if you would post the output of show interface trunk from the 3560.
I would suggest creating the layer 2 vlan on the 3560. You do not necessarily need to assign ports to it, but create vlan 102.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2013 08:21 AM
I was overthinking things - I created vlan 102 in Cisco 3560 with an IP address and vlan 102 in Procurve 5406 had no IP address.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2013 09:14 AM
I am glad that you got the issue solved and that our suggestions were helpful. Thank you for posting back to the forum to update us that is is fixed and what you did to fix it. And thank you for using the rating system to mark this question as answered.
HTH
Rick
Rick
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide