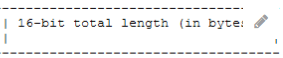- Cisco Community
- Technology and Support
- Networking
- Switching
- Captured Ip packet
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Captured Ip packet
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2018 05:48 PM - edited 03-08-2019 02:00 PM
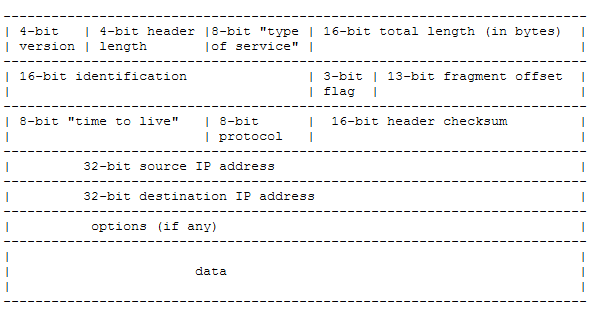
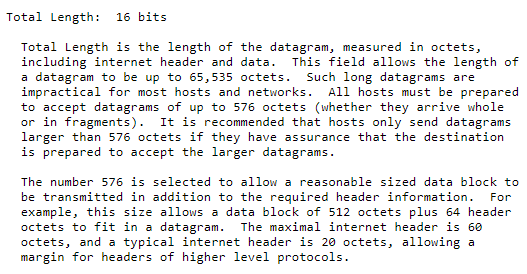
8. I have captured an IP packet in its binary format on the way from its source to destination. Now looking at the starting few bytes of the Packet (shown below) carefully. Provide following information about the packet
CAPTURED IP PACKET
01000101000000000000000111111111
00000000001111110010000000000000
001110110000011011111111000000001100000100000001000000010000000100001010000010100000101000000001
a. What is the total length of the packet
b. What is the Identification number of this packet
c. What is the version of the packet
d. What is the length of the header
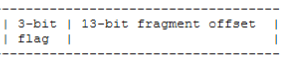
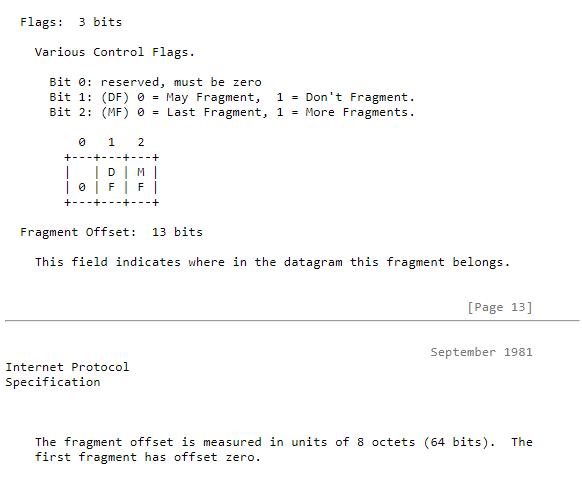
e. Is the packet allowed to be fragmented
f. If it is fragmented then is it the last Packet
g. What type of precedence is given to this Packet
h. What type of services are required for this Packet
i. If it is Fragmented then what is the fragmentation offset
j. What upper layer protocol is this IP Packet Carrying
k. What is the source IP address
l. If the packet is already fragmented
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2018 08:55 PM
If you put your capture in wireshark, it will answer most of your questions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2018 12:46 AM
Hello,
I tried to do this manually, here is what I have come up with. The letters in brackets correspond to the questions, and refer to the preceding bits:
0100(c)0101(d)00000000(g,h)0000000111111111(a)
0000000000111111(b)001(e)0000000000000(i)
0011101100000110(j)1111111100000000/
11000001-00000001-00000001-00000001(k)
00001010000010100000101000000001
a. What is the total length of the packet --> 255 bytes
b. What is the Identification number of this packet --> 63
c. What is the version of the packet --> 4
d. What is the length of the header --> 5
e. Is the packet allowed to be fragmented --> yes, fragment flag is set
f. If it is fragmented then is it the last Packet --> no
g. What type of precedence is given to this Packet --> none
h. What type of services are required for this Packet --> none
i. If it is Fragmented then what is the fragmentation offset --> no offset
j. What upper layer protocol is this IP Packet Carrying --> 6 (TCP)
k. What is the source IP address ---> 193.1.1.1
l. If the packet is already fragmented --> yes
There is a pretty decent document which you can use to dissect the binary info:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2018 05:59 AM
THE IP PACKET FORMAT
0100 0101 00000000 0000000111111111
0000000000111111 001 0000000000000
00111011 00000110 1111111100000000
11000001.00000001.00000001.00000001
11000002.00001010.00001010.00000001
a. What is the total length of the packet >255 bytes
b. What is the Identification number of this packet >63
c. What is the version of the packet >4
d. What is the length of the header >5
e. Is the packet allowed to be fragmented > yes, Fragment Flag is set.
f. If it is fragmented then is it the last Packet > no
g. What type of precedence is given to this Packet > none
h. What type of services are required for this Packet > none
i. If it is Fragmented then what is the fragmentation offset > no offset
j. What upper layer protocol is this IP Packet Carrying > 6 (TCP)
k. What is the source IP address > 203.1.1.1
l. If the packet is already fragmented > yes
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2018 07:20 AM
Hello,
great, you got almost exactly what I got, except for the source IP:
11000001.00000001.00000001.00000001
should be 193.1.1.1 ? How did you come up with 203.1.1.1 ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2018 07:21 PM
You are right that's my mistake.
Source IP in binary - 11000001.00000001.00000001.00000001
Source IP in decimal - 193.1.1.1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2018 08:35 AM
how we know fragmentation is already done or not and how did you find out total length kindly tell me in detail
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2018 08:31 PM
Hello,
Above question we discuss the packet format. Below i try to explain that point, which one you want to understand.
1) How we know fragmentation is already done or not ?
2) How did you find out total length kindly tell me in detail ?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide