- Cisco Community
- Technology and Support
- Networking
- Switching
- CBS350 - One directional ACLs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-30-2020 08:39 PM - edited 12-30-2020 08:47 PM
Dear Cisco Community,
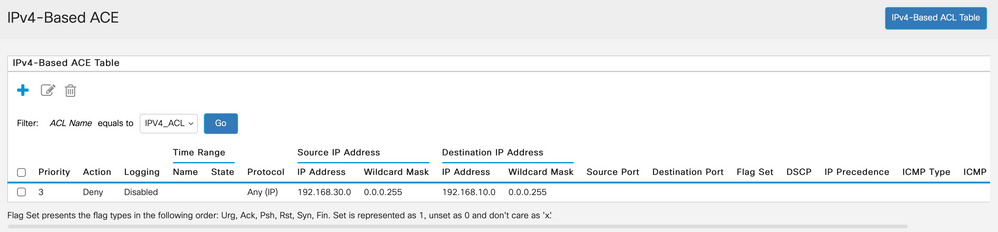
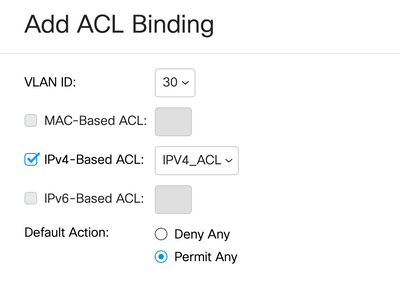
I have two VLANs on my CBS350-24T-4X
- VLAN 10 - 192.168.10.0
- VLAN 30 - 192.168.30.0
And I want VLAN 10 to access VLAN 30
but I want to block VLAN 30 accessing VLAN 10.
VLAN 10 -----ALLOW
VLAN 10 <<<----BLOCK
I've tried several things and also followed this Cisco YouTube video but it blocks signal from both directions.
When I ping from 192.168.10.7 to 192.168.30.33 I get Request timeout.
When I ping from 192.168.30.33 to 192.168.10.7 I get Request timeout.
Here are my settings. Any help would be very much appreciated!!
Thank you so much in advance.
Solved! Go to Solution.
- Labels:
-
Other Switches
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2020 10:50 AM
-The access list shown by Paul will allow UDP traffic to be initiated from VLAN 30 to VLAN 10 which does not conform to the requirements of the original post which is why I mentioned using a stateful packet filter such as the one in your EdgeRouter Lite.
-As to your question about slowing down, you will likely not see any kind of speed degradation.
-As for your question about ACL CLI syntax, according to: https://www.cisco.com/c/dam/en/us/td/docs/switches/lan/csbms/350_/cli_guide/CLI_Tesla_Sx350_2_2_5.pdf it looks to be similar to IOS but some minor differences so if you were wanting to block traffic as mentioned in your original post, the syntax would be:
ip access-list extended NO-ACCESS-TO-VLAN10 deny ip any 192.168.10.0 0.0.0.255 interface vlan 30 service-acl input NO-ACCESS-TO-VLAN10 default-action permit-any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2020 12:07 AM
If you create an ACL that blocks traffic sourced from VLAN 30 that is destined for VLAN 10 and apply the ACL to the VLAN 30 interface in the inbound direction, your desired goal would be met; however, you would still not be able to ping. If you were on a computer in VLAN 10 and pinged a computer on VLAN 30 that was running a packet capture, you would see the incoming echo request followed by the echo reply. The computer in VLAN 10 would never receive the echo reply because the ACL would be blocking it. So traffic is in fact making it from VLAN 10 to VLAN 30 but traffic from VLAN 30 is not making it back to VLAN 10.
Now if you are wanting VLAN 10 to be able to initiate a connection with a computer in VLAN 30 and allowing the return traffic (able to receive the echo replies) while denying any computer in VLAN 30 from initiating a connection with any device in VLAN 10, you would not be able to accomplish this with an ACL. This is what a stateful packet filter does which is commonly seen in firewalls.
Does this answer your question?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2020 06:50 AM - edited 12-31-2020 06:59 AM
Thank you so much for the detailed explanation!!!
I was very confused about the difference between ACLs and FireWalls. But after reading your explanation, everything makes perfect sense now.
Looks like, I need to do this via FireWall in my Router, not this switch. And I have two questions relate d to this. hopefully, you can answer this for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2020 01:29 AM - edited 12-31-2020 02:03 AM
Hello
@bwv656 wrote:
Dear Cisco Community,
I have two VLANs on my CBS350-24T-4X
- VLAN 10 - 192.168.10.0
- VLAN 30 - 192.168.30.0
And I want VLAN 10 to access VLAN 30
but I want to block VLAN 30 accessing VLAN 10.VLAN 10 -----ALLOW
---->>> VLAN 30 VLAN 10 <<<----BLOCK
----- VLAN 30
Having never had any exposure to this switch model so i cannot say if you can do this within the GUI, So do you have access to the cli?
The following example should perform the above request for tcp traffic, udp is classless it so cannot be filtered on established traffic
ip access-list extended Vl10-Vl30
permit icmp 192.168.30.0 0.0.0.255 any echo-reply
deny icmp 192.168.30.0 0.0.0.255 any echo
permit tcp 192.168.30.0 0.0.0.255 any established
deny tcp 192.168.30.0 0.0.0.255 any
permit ip any any
int vlan 10
ip access-group Vl10-Vl30 out
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2020 06:56 AM - edited 12-31-2020 07:24 AM
Thank you so much for the answer. But I have a quick question before I try anything. Above CLI commands you posted are for IOS only right? The switch I have is the new CBS 350 switches, basically a face-lifted version of old SG350s. Please correct me if I am wrong but IOS commands are not compatible with these switches, right? Especially the ACLs commands.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2020 10:50 AM
-The access list shown by Paul will allow UDP traffic to be initiated from VLAN 30 to VLAN 10 which does not conform to the requirements of the original post which is why I mentioned using a stateful packet filter such as the one in your EdgeRouter Lite.
-As to your question about slowing down, you will likely not see any kind of speed degradation.
-As for your question about ACL CLI syntax, according to: https://www.cisco.com/c/dam/en/us/td/docs/switches/lan/csbms/350_/cli_guide/CLI_Tesla_Sx350_2_2_5.pdf it looks to be similar to IOS but some minor differences so if you were wanting to block traffic as mentioned in your original post, the syntax would be:
ip access-list extended NO-ACCESS-TO-VLAN10 deny ip any 192.168.10.0 0.0.0.255 interface vlan 30 service-acl input NO-ACCESS-TO-VLAN10 default-action permit-any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2020 11:18 AM
Thank you so much once again for taking the time to write this detailed answer!!! You really helped me to understand the whole thing.
As you suggest I will use the EdgeRouter for managing the traffic. And I am so glad about this because I was starting to think managing ACLs felt not as intuitive as managing Firewall rules. At least for me.
Thanks again for your crystal clear answers!! Happy New Year!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2020 02:47 PM
Hello @TJ-20933766
The acl you propose will not allow traffic initiated from vlan 10 whatsoever not even tcp.
Now if your going to incorporate a router for the inter lan routing then your have options open up other than using a firewall
features such as:
DACL
CBAC
ZBFW
All of which won’t require a designated firewall but will allow you to deny traffic one way and allow the other!
However if this switch is the L3 for the lan then naturally the above isn’t viable with a router or firewall unless you move the L3 for those two vlans off the switch and onto a router /firewall and filter from their
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-31-2020 03:14 PM
Paul, thank you so much for providing the extra information. Since I don't have a CISCO router. I only have Cisco Switches at home (CBS350-24T-4X and SG200). So those features you listed are out of reach for me. But in the future, I will consider them when I upgrade my router. For now, I will stick with the Firewall in my router and go from there. Thanks again for providing the detailed answers today and hope you have a wonderful 2021!! Happy New Year!!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide