- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2022 05:43 PM
Dear everyone,
I'm trying to configure a named extended ACL to deny one host access to a DHCP server while permitting another host access. Both of them are on the same Vlan and I've realized that you can use 0.0.0.0 as a source IP to deny access to the destination address 255.255.255.255 but that means that I would have to either deny access to BOTH hosts are permit access to both hosts.
Is there anyway for me to treat one of the two hosts as a separate IP? I thought of using MAC ACL but that doesn't work sub-interfaces which are also being utilized in the network.
Thank you all in advance for your assistance.
Solved! Go to Solution.
- Labels:
-
LAN Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2022 09:41 PM
We do not have enough information to be able to give you much advice. A good starting point would be to give us the output of the commands you use to create the acl and to apply the acl. It would also help if you could explain the topology of the network (where are the hosts, where is the dhcp server) or to give us a simple diagram showing this.
I will say that you seem to be confused about what mask to use. You are correct that if you use mask 255.255.255.255 then the source address will always be 0.0.0.0. And that is not what you want. If you want to permit or deny specific hosts then you need to use mask 0.0.0.0.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2022 02:00 PM
Thank you. This clarification is quite useful. To be clear you want a named acl on interface vlan 20 which will allow a specific host to obtain an IP address from the dhcp server but will not allow any other access from that host to that server. You want all other devices in that vlan/subnet to have full access to the server?
I suggest that your config might look somewhat like this:
ip access-list vlan20 extended
deny ip host 193.168.44.h host <serverIP> where h is the IP of the host you want to deny
permit ip any any
interface vlan 20
ip access-group vlan20 in
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2022 09:41 PM
We do not have enough information to be able to give you much advice. A good starting point would be to give us the output of the commands you use to create the acl and to apply the acl. It would also help if you could explain the topology of the network (where are the hosts, where is the dhcp server) or to give us a simple diagram showing this.
I will say that you seem to be confused about what mask to use. You are correct that if you use mask 255.255.255.255 then the source address will always be 0.0.0.0. And that is not what you want. If you want to permit or deny specific hosts then you need to use mask 0.0.0.0.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2022 11:57 PM - edited 11-25-2022 06:18 AM
still not get what issue here ???
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2022 12:56 AM
Hello,
I think this has come up a few times before. Unless something fundamental has changed (which I don't think has), DHCP snooping is your only option...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2022 02:29 AM
Is this a wired or wireless client ?
you want to deny access from client to dhcp server once it has got the dhcp ip or you want this specific client not to go through dhcp process ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2022 06:07 AM
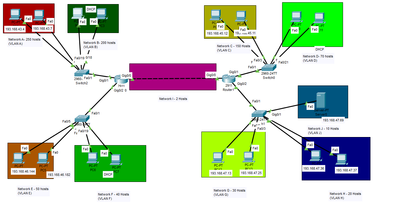
Thank you to everyone for attempting to help and apologies for not providing enough info:
Here is a screenshot of my network topology, the hosts in question are the two in Network B, both wired connected and both are having their IPs given by the DHCP server in Network J (VLAN J), the ACL output I'm creating is:
10 permit udp host 0.0.0.0 eq bootpc host 255.255.255.255 eq bootps
I also tried changing the host to the IP given by the DHCP server but that never seems to work, it should also be noted that the network has multiple OSPF connections:
router ospf 1
router-id 1.1.1.1
log-adjacency-changes
passive-interface GigabitEthernet0/1.10
passive-interface GigabitEthernet0/1.20
passive-interface GigabitEthernet0/2.30
passive-interface GigabitEthernet0/2.40
passive-interface GigabitEthernet0/2.90
network 193.168.47.84 0.0.0.3 area 0
network 193.168.43.0 0.0.0.255 area 0
network 193.168.44.0 0.0.0.255 area 0
network 193.168.46.0 0.0.0.63 area 0
network 193.168.46.128 0.0.0.63 area 0
network 193.168.46.192 0.0.0.63 area 0
network 193.168.47.64 0.0.0.15 area 0
The connection for Network B is gig0/1.20 on network 193.168.44.0 0.0.0.255
I hope all of this clears up the confusion I caused, is there anything I should be doing differently?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2022 08:46 AM
It would be helpful if you would post the complete acl and the configuration of the interface where it is applied. Also helpful if we had the IP addresses of each host and of the server. Let me address what we have so far. In reading the original post I thought that you were describing something like permit 0.0.0.0 255.255.255.255 (which is equivalent to permit any). But I see that you did really mean 0.0.0.0 and 255.255.255.255 as addresses. The issue is that neither of these are valid as addresses for a device. For the acl to work you need to specify valid addresses as source and destination.
That would be easy enough for the destination. If you are trying to control access to the dhcp server then the server IP would be the destination. But it is a challenge trying to figure out what to use for the source. Since you are controlling access to the dhcp server the clients do not yet have an IP address. And so there is really not any address that will work in an IP extended access list. Perhaps some mac acl or perhaps something in dhcp snooping might help you achieve your objective.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2022 10:36 AM
I'm not sure what you mean by complete ACL but when I do show access-list this is what's output:
Extended IP access list 1
10 permit ip host 193.168.43.4 any
20 deny ip host 193.168.43.7 host 193.168.47.36
30 deny ip host 193.168.43.7 host 193.168.47.37
Extended IP access list 3
10 permit udp host 0.0.0.0 eq bootpc host 255.255.255.255 eq bootps
And here is my show run for the interface the hosts are running on:
interface GigabitEthernet0/1.20
encapsulation dot1Q 20
ip address 193.168.44.1 255.255.255.0
ip helper-address 193.168.47.69
As for the IP for the hosts (As given by the DHCP server) the first is 193.168.44.2 and the other is 193.168.44.3 and the DHCP ip address is 193.168.47.69
The advice you have given so far has been helpful, I looked into DHCP snooping and mac ACL but neither has worked for me so far, though admittedly I haven't tried everything either has to offer. Personally I feel MAC ACL has the best chance of giving me what I'm looking for but I can't get my switch or my router to even acknowledge the command for me to try it out.
The command I'm trying to run is:
mac access-list extended name
But everytime I run it, I just get this error:
Invalid input detected at '^' marker, with the ^ pointing to the access-list part of the command.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2022 10:58 AM
sure this because PKT not support this command, I hope I add IOSL2 to my GNS3VM tonight and test the idea of MAC ACL,
but still I dont get what you need
do you need
host get ip from dhcp
then it can not ping DHCP
or
host totally not get ip nor ping DHCP?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2022 12:27 PM
Earlier in the discussion @ammahend asked an interesting question: "you want to deny access from client to dhcp server once it has got the dhcp ip or you want this specific client not to go through dhcp process". The significance is that if you want the host to obtain an IP address and then to deny further access than an IP acl is the appropriate tool. But if you want to prevent the host from obtaining an IP address than an IP acl will not work (since the host does not have an IP address at that point then an IP acl can not identify the host). Can you clarify what you are trying to achieve?
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2022 12:56 PM
to no longer access the server after that point, hope that clarifies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2022 02:00 PM
Thank you. This clarification is quite useful. To be clear you want a named acl on interface vlan 20 which will allow a specific host to obtain an IP address from the dhcp server but will not allow any other access from that host to that server. You want all other devices in that vlan/subnet to have full access to the server?
I suggest that your config might look somewhat like this:
ip access-list vlan20 extended
deny ip host 193.168.44.h host <serverIP> where h is the IP of the host you want to deny
permit ip any any
interface vlan 20
ip access-group vlan20 in
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2022 02:51 PM
Thank you! this worked!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-26-2022 12:20 AM
You are welcome. Good to know that it is working now. I am glad that our suggestions have been helpful. Thank you for marking this question as solved. This will help other participants in the community to identify discussions which have helpful information. This community is an excellent place to ask questions and to learn about networking. I hope to see you continue to be active in the community.
Rick