- Cisco Community
- Technology and Support
- Networking
- Switching
- DMZ Access restriction
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
DMZ Access restriction
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2012 03:13 PM - edited 03-07-2019 06:23 AM
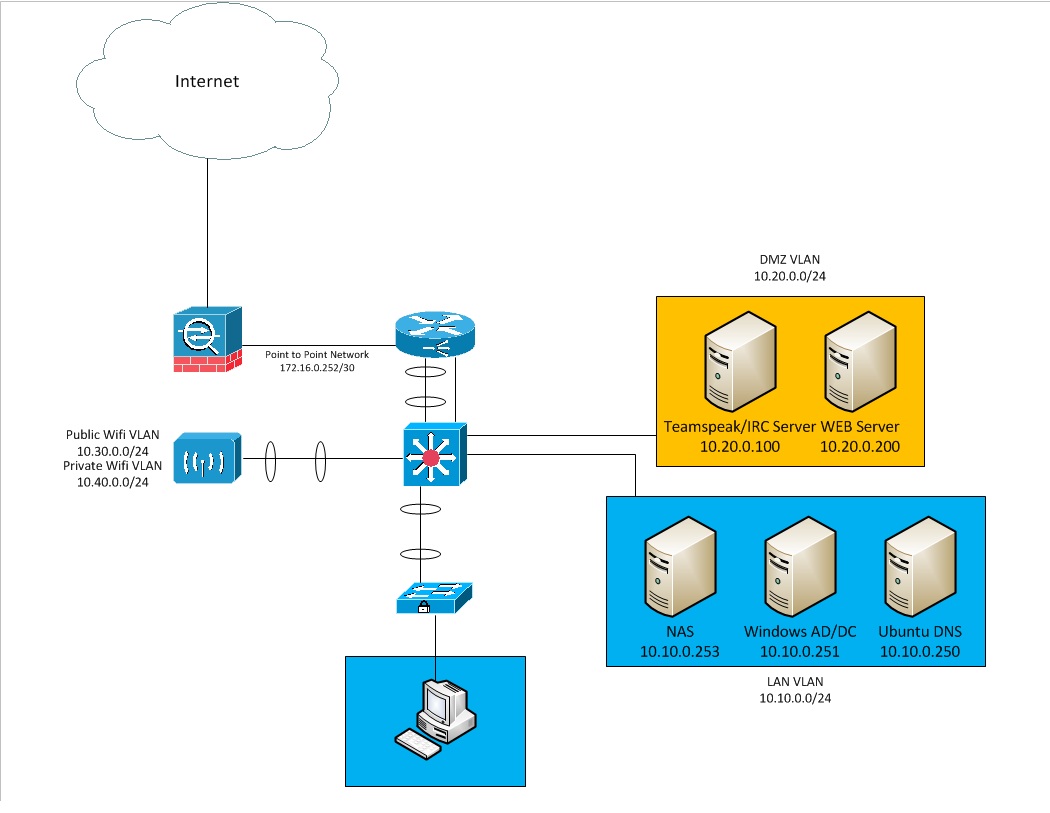
My issue lies in DMZ security. What i have is an ASA5505 acting as my firewall and NAT device. I am NATing ports 21, 80, 9987 and 6667 to servers on my DMZ. The DMZ has its own dedicated interface on my 2621XM router and has an IP address of 10.20.0.254. I want to permit the LAN and Private Wifi VLANs to access the DMZ, but i dont want the DMZ to access anything on my LAN except UDP over port 53 for DNS to my internal DNS servers. I was using the following ACL to acomplish this:
ip access-list extended DMZPolicy
permit udp any host 10.10.0.251 eq domain
permit udp any host 10.10.0.250 eq domain
deny ip any 10.10.0.0 0.0.0.255
deny ip any 10.30.0.0 0.0.0.255
deny ip any 10.40.0.0 0.0.0.255
permit ip any any
The issue with this is that no other network can access the DMZ. How can i permit LAN traffic to access the DMZ without allowing vice versa?
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2012 05:49 PM
If you're doing this on a router, your better bet would be either CBAC or zone based firewalls. I would recommend ZBF since it's a little more robust than CBAC:
ZBF:
http://www.cisco.com/en/US/products/ps6441/products_feature_guide09186a008060f6dd.html
CBAC:
HTH,
John
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide