- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: EtherChannel between cisco devices need help
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-20-2014 02:43 AM - edited 03-07-2019 06:19 PM
Hello,
At our company we use 2 asa 5525 firewalls in active/standby mode.
Both of them are connected to a single cisco router.
The goal is to have the cisco router to automatically send traffic to the active firewall (regardless which firewall is active at that point).
To solve this would it be possible to create an EtherChannel with 2 ports on the cisco router and then have 1 link going to the active firewall and 1 link to the standby firewall.
If the active firewall fails and the standby firewall takes over, will the standby firewall receive all the traffic that normally would go to the active firewall without any downtime?
Will this work or does another solution exists for this? Its important for us that the hosts on the network suffer small to none downtime at all.
The topology can be found in the following image.
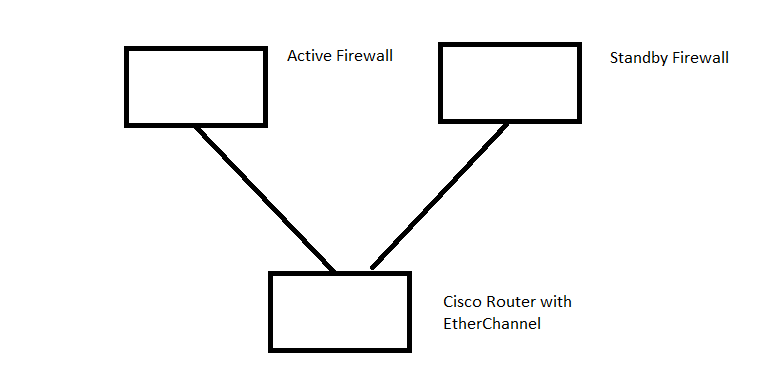
Solved! Go to Solution.
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2014 12:15 AM
Or should I create a "VLAN 101 Routing" on the Stack, and then assign IP addres 192.168.101.1 to it, and then set the gateway to 192.168.101.2 and link L2 ACCESS Ports in VLAN 101 to each Firewall?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2014 12:29 AM
Joris
With active/standby you cannot user L3 connections to the firewall.
For failover to work you need the inside interfaces in the same vlan. So you simply -
1) create a new vlan and allocate new IP subnet
2) create an SVI on the 3750 and give it an IP from that subnet
3) give each inside interface of the firewalls an IP from the same subnet
4) add a default route on the 3750 pointing to the active firewall IP
5) on the firewall any routes for the internal networks point to the SVI IP address
Note you could run a dynamic routing protocol between the 3750 and the firewalls if you would rather do that although when i last did ASAs the standby does not participate in the routing protcol so if it fails over new adjancencies need to be established. This may have changed but with statics you don't get that delay.
You obviously also need failover setup and the outside interfaces and any DMZs must also be in their own vlan ie
both outside interfaces must have their own vlan and if you have a DMZ those interfaces must be in the same vlan.
Just to be clear they would all be different vlans.
Finally you can reuse an existing vlan for the inside interfaces but it is a good idea to have a dedicated vlan for this.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2014 12:20 AM
Joris
So if I understand correctly, if we would link the routed L3 switch etherchannel ports physically to itself, to another Etherchannel on the same switch, in a specific VLAN, and then we would create an additional 2 ports in that VLAN that are L2, and then uplink those links to both Firewalls (Active/Standby), this would work??
But how can you explain such a 'solution' to customers, there most be a better way?
There is and you don't need any bridging or L3 etherchannel. If the router is actually a L3 switch then you have no problem at all, you just connect each firewall into a different switch in the stack and use a common vlan. This is a standard design with active/standby firewalls.
You would gain absolutely nothing from an additional switch, in fact you have more redundancy by using the switch stack.
You don't need L3 etherchannel anywhere. You simply have one connection from each switch. You are redundant because -
1) if active firewall or active firewall inside interface fails (and you are monitoring the inside interface with failover) the you move the standby firewall
2) if the phsyical switch the active firewall is connected to fails the again the firewall fails over to the standby firewall.
The solution we suggested was based on the assumption that you have a phsyical router and the ports were only L3 ports.
Note also if you need more bandwidth to each firewall you could use L2 etherchannels instead of single links, again they would be L2 not L3.
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2014 01:03 AM
Thank you!
System is online!
I created VLAN 101 ROUTING, set the VSI to 192.168.101.1 en changed the original L3 uplinks to L2 access ports in VLAN101, and it worked.
This was our first experience on this so, beginner mistake I guess.
We don' have enough fiber ports for dual links (etherchannel) to the firewall, so we are not going to do that.
Only question I still have is, how fast the L3 switch will converge if I pull out the uplink to the active firewall.
I think the firewall will notice this quite fast and set the Standby to Active, but I am not sure if the L3 switch will detect this fast. Will test this later.
Thanks again to all of you
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide