- Cisco Community
- Technology and Support
- Networking
- Switching
- How to configure SGE2000 ACL?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-27-2011 06:03 PM - edited 03-07-2019 01:26 AM
Greetings to all Prof. and Engr. here in community a GOOD DAY!!!
Scenario 1.
Ncomputing Server 1 Address: 192.168.85.216
Ncomputing Server 2 Address: 192.168.85.215
I have a 20 VLAN ID's created in SGE2000 (Layer3 Mode). My 2 ncomputing server was a member of VLAN1 (default).
Question.
A. I want a certain vlan that can have an access to my ncomputing server, for example VLAN ID 20 should have to access Ncomputing server1 only and VLAN 25 to Ncomputing Server 2, then other VLAN ID's should have no access on the Ncomputing Server.
B. As default All Vlan Dont see each other and i want them to see each other.. like VLAN 30 IP can ping VLAN 40 IP
How to do this in access list?
Any ideas are welcome and appreciated, If my information need more details just let me know so i can post more details here..
Thank you in advance..
BS,
Mike
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2011 08:45 AM
Hi John,
Pretty simple thank goodness.
Firstly you create a ACL being very careful as to the fields you fill in.
In my example below, I plugged a IP phone onto Gig port 1 of my SGE2000P.
All I wanted my access list to do was filter all ICMP traffic ingressing into the switch port from my IP phone that is destined to go to the 192.168.10.0 network. This was a quick and dirty way to demonstrate if the filter was working or not. Blocking ICMP would kill any ping that I tried form my PC to the IP phone.
Look very closely, I set ACL entry priorities and used reverse subnet masks.
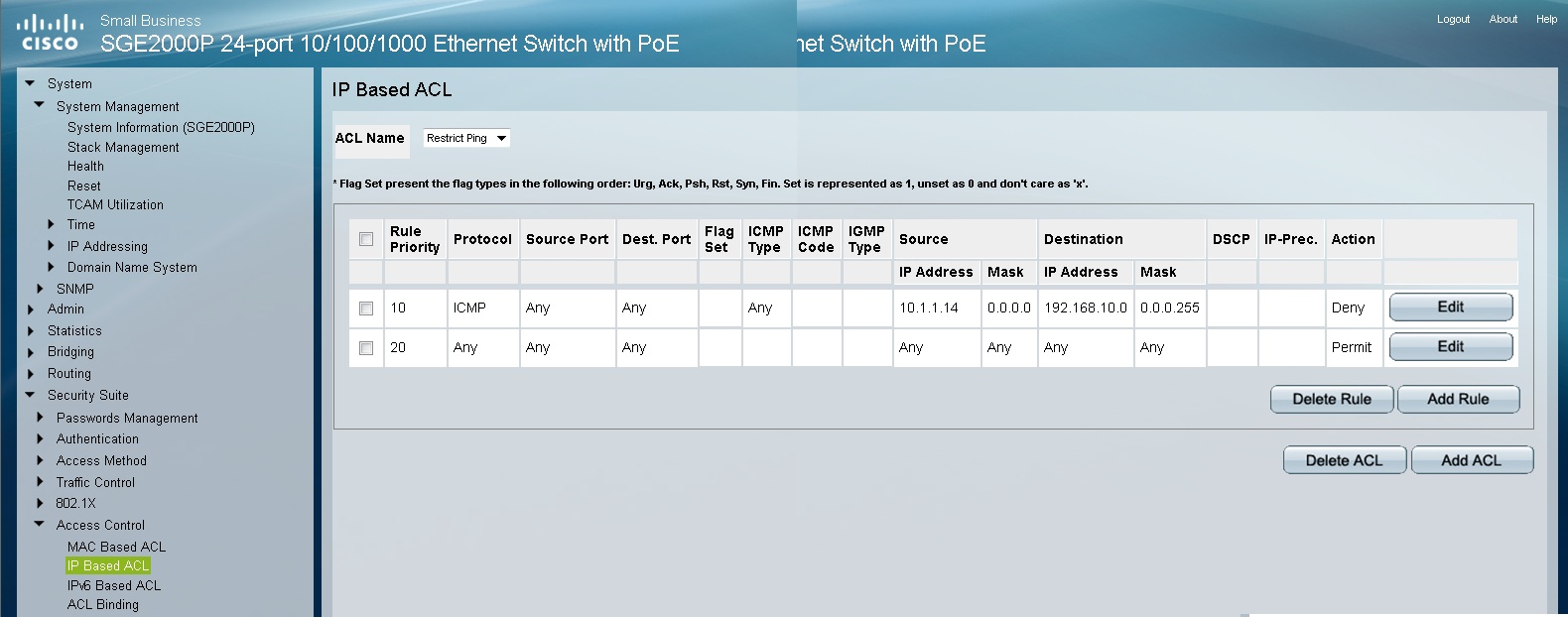
Notice that my second ACL entry is a allow all. the resaon for this is that there is always a unseen rule at the end of the access list (ACL) which is to deny all.
So my intention of this access list is only to restrict ICMP going back from 10.1.1.14 to the 192.168.10.0 network, not any other traffic..
Then I bound the ACL to a interface , as the access-list filters on ethernet frame ingress into the switch.
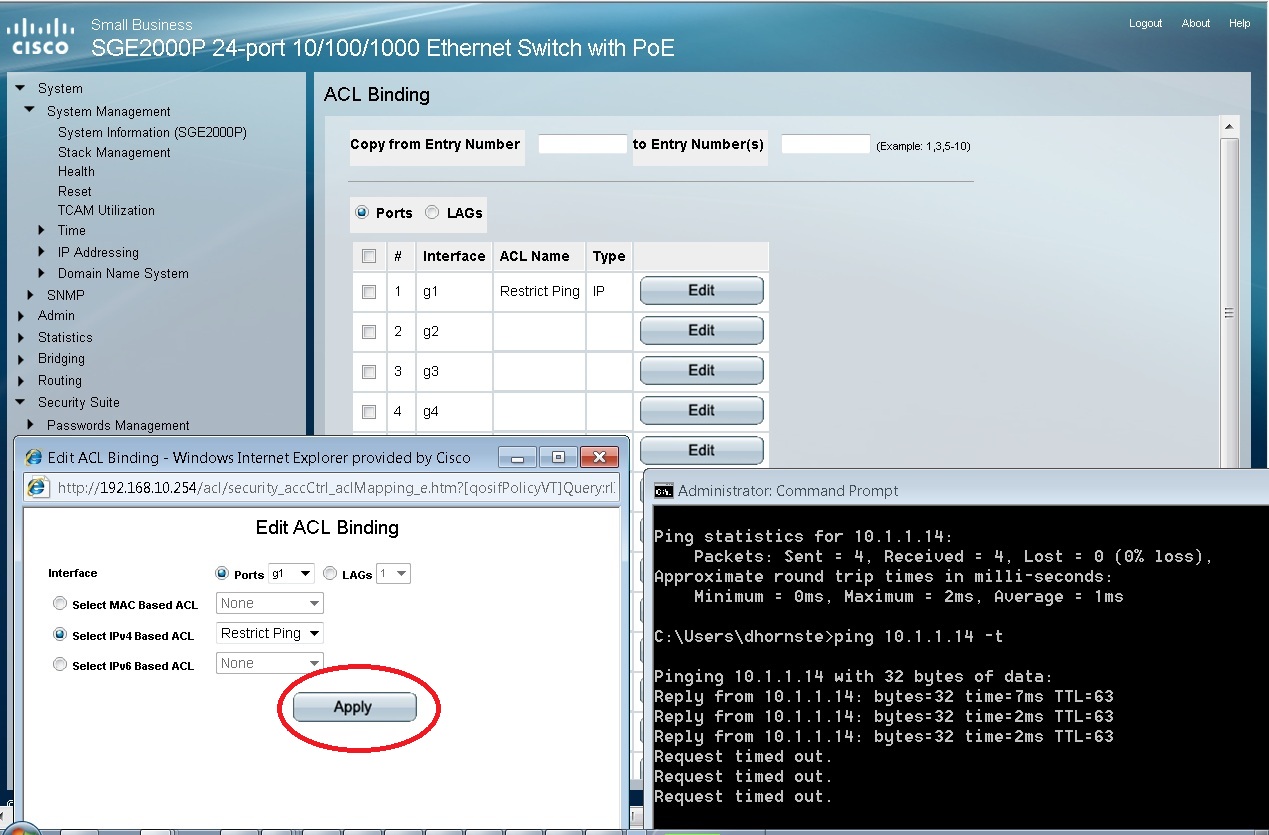
I applied the ACL to Gig port 1 and as you can see, the pinging stopped and ACL called restrict ping appear next to port 1 .
Hope this helps.
You would be better using the Small Business part of this community for any further questions regarding your switch.
regards Dave
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2011 08:33 PM
Thank you for your kind comments.
When the access list is applied to a switch port, it permits or denies ethernet frames.
Embedded in that ethernet frame could be a IP packet, which could be TCP, UDP or other protocol.
The switch silicon within the SGE2000 is very smart .
An access list tells the switch silicon to look well into the ethernet frame and pattern match certain fields.
Access lists filter network traffic by controlling whether ethernet are forwarded or blocked at the SGE2000 port interface.
Your switch examines each packet that comes in to a switch port to determine whether to forward or drop the packet, on the basis of the criteria you specified within the access lists.
Access list criteria could be the source address of the traffic, the destination address of the traffic, the upper-layer protocol, or other information.
When you apply a access list to a SGE2000 or even the SRW2024-K9-EU it examines ethernet frames as they enter the switch. The term in english, is that the access list filters on ingress of packets into the switch port.
So a access list applied on SGE2000 switch port 1, could monitor traffic coming in from port 1 and deny certain traffic that goes to a SRW2024-K9-EU via a trunked port.
A access list can be apllied to many of the SGE2000 switch ports at once.
SRW2XXX-K9 have extensive access list functionality that work the same way.
The SRW2XXX-K9 (300 series) also permit or deny ethernet frames on packet ingress into the switch.
Hope this helps
regards Dave
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-28-2011 08:21 PM
Anyone can help plz..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2011 05:09 AM
Go to page 85 of the pdf, the page is marked as 77).
http://www.cisco.com/en/US/docs/switches/lan/csbms/sge2000/reference/guide/sge_refguide.pdf
Please mark this post as correct answer if it is your solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2011 08:45 AM
Hi John,
Pretty simple thank goodness.
Firstly you create a ACL being very careful as to the fields you fill in.
In my example below, I plugged a IP phone onto Gig port 1 of my SGE2000P.
All I wanted my access list to do was filter all ICMP traffic ingressing into the switch port from my IP phone that is destined to go to the 192.168.10.0 network. This was a quick and dirty way to demonstrate if the filter was working or not. Blocking ICMP would kill any ping that I tried form my PC to the IP phone.
Look very closely, I set ACL entry priorities and used reverse subnet masks.

Notice that my second ACL entry is a allow all. the resaon for this is that there is always a unseen rule at the end of the access list (ACL) which is to deny all.
So my intention of this access list is only to restrict ICMP going back from 10.1.1.14 to the 192.168.10.0 network, not any other traffic..
Then I bound the ACL to a interface , as the access-list filters on ethernet frame ingress into the switch.

I applied the ACL to Gig port 1 and as you can see, the pinging stopped and ACL called restrict ping appear next to port 1 .
Hope this helps.
You would be better using the Small Business part of this community for any further questions regarding your switch.
regards Dave
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2011 06:55 PM
Goo Day,
Thank you sir Antonio for the reference.
Sir David, that was a great tut. I get what i want now. Sir May I ask some more?
Is the Access List settings from SGE2000 will carry to SRW2024 switch? I mean When i plug in this srw2024 switch, will the settings from sge2000 be apply also?
"My diagram was from sge2000 have a trunkline to SRW2024"
Thank you very much
WR,
Mike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2011 08:33 PM
Thank you for your kind comments.
When the access list is applied to a switch port, it permits or denies ethernet frames.
Embedded in that ethernet frame could be a IP packet, which could be TCP, UDP or other protocol.
The switch silicon within the SGE2000 is very smart .
An access list tells the switch silicon to look well into the ethernet frame and pattern match certain fields.
Access lists filter network traffic by controlling whether ethernet are forwarded or blocked at the SGE2000 port interface.
Your switch examines each packet that comes in to a switch port to determine whether to forward or drop the packet, on the basis of the criteria you specified within the access lists.
Access list criteria could be the source address of the traffic, the destination address of the traffic, the upper-layer protocol, or other information.
When you apply a access list to a SGE2000 or even the SRW2024-K9-EU it examines ethernet frames as they enter the switch. The term in english, is that the access list filters on ingress of packets into the switch port.
So a access list applied on SGE2000 switch port 1, could monitor traffic coming in from port 1 and deny certain traffic that goes to a SRW2024-K9-EU via a trunked port.
A access list can be apllied to many of the SGE2000 switch ports at once.
SRW2XXX-K9 have extensive access list functionality that work the same way.
The SRW2XXX-K9 (300 series) also permit or deny ethernet frames on packet ingress into the switch.
Hope this helps
regards Dave
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2011 10:18 PM
Good Day,
That was a great sir David, 1st im afraid to apply the ACL to one of the trunk line coz im not sure whats gonna happen next but as you said "
So a access list applied on SGE2000 switch port 1, could monitor traffic coming in from port 1 and deny certain traffic that goes to a SRW2024-K9-EU via a trunked port." then i try it then boom, it's working.
Once again sir its a very big help, althoug this is a newbi question but this is a big help for me..totally i dont have enough knowledge in networking specially the SGE2000 but w/ the help of forum, im on it.
Once again than you very much,
BR,
Mike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2011 10:22 PM
Sir David, If i have some question regarding SGE2000 will you help me out?
Tnx
WR,
Mike
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

