- Cisco Community
- Technology and Support
- Networking
- Switching
- How to setup two LAN on C2960XR Switch with Port-Based VLAN ?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to setup two LAN on C2960XR Switch with Port-Based VLAN ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2019 12:28 PM
Hi to all,
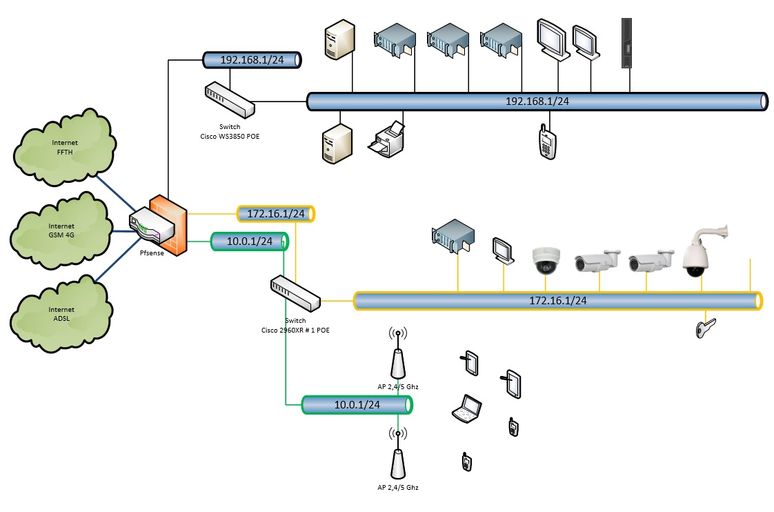
I'm looking to create two LAN isolated on a single physical switch with port-based VLAN (untagged).
One port from each VLAN will be plugged to switch (link in yellow and green), see picture below.
VLAN 2000, name = GUEST, subnet = 172.16.1/24
VLAN 3000, name = WIFI, subnet = 10.0.1/24
I need to be sure that both VLAN cannot communicate to each one for security reason.
Currently, my switch has only VLAN1, setup is like this :
Using 3379 out of 524288 bytes ! ! Last configuration change at 13:25:47 CET Sat Feb 16 2019 ! NVRAM config last updated at 13:26:02 CET Sat Feb 16 2019 ! version 15.2 no service pad service timestamps debug datetime localtime service timestamps log datetime localtime service password-encryption ! hostname C2960XR#1 ! boot-start-marker boot-end-marker ! enable secret 5 XXXXXXXXXXXXXXX enable password 7 XXXXXXXXXXXXXXXXX ! username Cisco privilege 15 secret 5 XXXXXXXXXXXXXXXXXXXXXXXXXXXX. no aaa new-model clock timezone CET 1 0 clock summer-time CET recurring last Sun Mar 1:00 last Sun Oct 1:00 switch 1 provision ws-c2960xr-48lpd-i system mtu routing 1500 ! ! ! crypto pki trustpoint TP-self-signed-XXXXXXXXXXXXX enrollment selfsigned subject-name cn=IOS-Self-Signed-Certificate-XXXXXXXXXXXX revocation-check none rsakeypair TP-self-signed-XXXXXXXXXXXXXXXX ! ! crypto pki certificate chain TP-self-signed-XXXXXXXXXXXXXX certificate self-signed 01 nvram:IOS-Self-Sig#1.cer ! spanning-tree mode pvst spanning-tree extend system-id ! ! ! interface Bluetooth0 no ip address shutdown downshift disable ! interface FastEthernet0 no ip address shutdown ! interface GigabitEthernet1/0/1 ! interface GigabitEthernet1/0/2 ! interface GigabitEthernet1/0/3 ! interface GigabitEthernet1/0/4 ! interface GigabitEthernet1/0/5 ! interface GigabitEthernet1/0/6 ! interface GigabitEthernet1/0/7 ! interface GigabitEthernet1/0/8 ! interface GigabitEthernet1/0/9 ! interface GigabitEthernet1/0/10 ! interface GigabitEthernet1/0/11 ! interface GigabitEthernet1/0/12 ! interface GigabitEthernet1/0/13 ! interface GigabitEthernet1/0/14 ! interface GigabitEthernet1/0/15 ! interface GigabitEthernet1/0/16 ! interface GigabitEthernet1/0/17 ! interface GigabitEthernet1/0/18 ! interface GigabitEthernet1/0/19 ! interface GigabitEthernet1/0/20 ! interface GigabitEthernet1/0/21 ! interface GigabitEthernet1/0/22 ! interface GigabitEthernet1/0/23 ! interface GigabitEthernet1/0/24 ! interface GigabitEthernet1/0/25 ! interface GigabitEthernet1/0/26 ! interface GigabitEthernet1/0/27 ! interface GigabitEthernet1/0/28 ! interface GigabitEthernet1/0/29 ! interface GigabitEthernet1/0/30 ! interface GigabitEthernet1/0/31 ! interface GigabitEthernet1/0/32 ! interface GigabitEthernet1/0/33 ! interface GigabitEthernet1/0/34 ! interface GigabitEthernet1/0/35 ! interface GigabitEthernet1/0/36 ! interface GigabitEthernet1/0/37 ! interface GigabitEthernet1/0/38 ! interface GigabitEthernet1/0/39 ! interface GigabitEthernet1/0/40 ! interface GigabitEthernet1/0/41 ! interface GigabitEthernet1/0/42 ! interface GigabitEthernet1/0/43 ! interface GigabitEthernet1/0/44 ! interface GigabitEthernet1/0/45 ! interface GigabitEthernet1/0/46 ! interface GigabitEthernet1/0/47 ! interface GigabitEthernet1/0/48 ! interface GigabitEthernet1/0/49 ! interface GigabitEthernet1/0/50 ! interface TenGigabitEthernet1/0/1 ! interface TenGigabitEthernet1/0/2 ! interface Vlan1 ip address 192.168.1.233 255.255.255.0 ! ip default-gateway 192.168.1.1 ip forward-protocol nd no ip http server ip http authentication local ip http secure-server ! ! no vstack ! line con 0 password 7 XXXXXXXXXXXXXXXXXX login line vty 0 4 password 7 XXXXXXXXXXXXXXXXXX login line vty 5 15 password 7 XXXXXXXXXXXXXXXXXX login ! ntp server ntp.deuza.net ntp server pool.ntp.org ! end
I think that i need to use these command, do you confirm that is correct ? Is it enough ?
configure #vlan 2000 #name VLAN GUEST #no shutdown #exit configure #vlan 3000 #name VLAN WIFI #no shutdown #exit configure #interface vlan 2000 #ip address 172.16.1.254 255.255.255.0 #no shut #exit configure #interface vlan 3000 #ip address 10.0.1.254 255.255.255.0 #no shut #exit configure #interface range Gi1/0/3-48,Te1/1/1,Te1/1/2 #switchport mode access #switchport access vlan 2000 #exit #interface range Gi1/0/1, Gi1/0/2,Te1/0/1,Te1/0/2 #switchport mode access #switchport access vlan 3000 #exit
Best Regards,
Elrick
- Labels:
-
Catalyst 2000
-
LAN Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2019 12:34 PM
yes that is correct, make sure your uplink side allow these VLAN (in the port-channel or trunk) towards FW side.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2019 12:37 PM
Yes, it's correct man. No shutdown on VLAN creation is not needed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2019 01:59 PM
Hello
@Elrick Landon wrote:
Hi to all,
I'm looking to create two LAN isolated on a single physical switch with port-based VLAN (untagged).
One port from each VLAN will be plugged to switch (link in yellow and green), see picture below.
VLAN 2000, name = GUEST, subnet = 172.16.1/24
VLAN 3000, name = WIFI, subnet = 10.0.1/24
I need to be sure that both VLAN cannot communicate to each one for security reason.
On the svi of each vlan you can apply a RACL to negate access between the vlans
Example:
access-list 100 deny ip 10.0.1.0 0.0.0.255 any
access-list 100 deny icmp 10.1.0 0.0.0.255 any echo-reply
access-list 100 permit ip any any
access-list 100 permit icmp any any
int vlan 2000
ip access-group 100 out
access-list 101 deny ip 172.16.10 0.0.0.255 any
access-list 101 deny icmp 172.16.10 0.0.0.255 any echo-reply
access-list 101 permit ip any any
access-list 101 permit icmp any any
int vlan 3000
ip access-group 101 out
Also highly recommend you check the internal vlan usage (show vlan internal usage) of the switch prior to designing and allowing any extended vlans, so you dont by mistake create a SVI and vlan that is being used internally by the switch.
Lasty note extended vlans can only be configured in the vlan database,stored to the vlan.dat file and propagated throughout the vlan estate via version 3 of vtp vtp version 1/2 can be used but each switch would require to be in vtp transparent mode and saved to the running config.
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-31-2019 11:16 PM
I was thinking that two VLANs created in this way are completely isolated, like if I have two physical switches, meaning that it was impossible to have communication between VLAN 2000 and VLAN 3000, is that right ?
Does RACL purpose is just a safeguard method in case of hack or something like this ?
Regarding the VLAN1, it seems to me that it is impossible to delete it (by design), for security reasons, i need to tack care that it is not affected on port, is that right? or i have something special to do to 'disable' it ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2019 02:37 AM
Hello
@Elrick Landon wrote:
I was thinking that two VLANs created in this way are completely isolated, like if I have two physical switches, meaning that it was impossible to have communication between VLAN 2000 and VLAN 3000, is that right ?
You absolutely correct, Having separate vlans on separate switches would be applicable, Initially looking your topology I saw two Switch Virtual Interfaces (SVI) on one switch and my assumption was this switch would be performing the inter-vlan routing but after looking again at your topology that doesnt seem the case as the FW looks like it would be doing that correct- so apologies!
I see now also there will be separate links into the FW from this switch for either vlan so you could go even as far as putting the guest vlan it own VRF or DMZ.
Does RACL purpose is just a safeguard method in case of hack or something like this ?
Regarding the VLAN1, it seems to me that it is impossible to delete it (by design), for security reasons, i need to tack care that it is not affected on port, is that right? or i have something special to do to 'disable' it ?
One of it uses on a L3 switch can be to deny inter-vlan communication between vlans like the example I previously posted
From a L2 perspective you cannot delete, suspend or shutdown vlan 1 but at a l3 perspective it doesn't have to have an ip address associated to it and its interface can be shutdown
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2019 12:06 PM - edited 04-04-2019 11:24 AM
One of it uses on a L3 switch can be to deny inter-vlan communication between vlans like the example I previously posted
Yes, but by default, two vlan with port based different cannot communicate right ?
From a L2 perspective you cannot delete, suspend or shutdown vlan 1 but at a l3 perspective it doesn't have to have an ip address associated to it and its interface can be shutdown
My switch is 2960XR (L3), how can i shutdown vlan 1 interface from CLI please ?
Best Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2019 02:07 AM
Hello
Apologies i missed your reply-
Yes, but by default, two vlan with port based different cannot communicate right ?
Correct they cannot unless some routing is involved
My switch is 2960XR (L3), how can i shutdown vlan 1 interface from CLI please ?
conf t
int vlan 1
shutdown
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide