- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Need Helping Fixing "Enable" Password & VPN Access
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Need Helping Fixing "Enable" Password & VPN Access
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2017 09:16 AM - edited 03-08-2019 12:26 PM
PROBLEM #1
I have 2 identical Cisco 3650 switches. I was trying to reset enable password on switch #1. Followed up tips in an older forum post I made and it ended up removing the pre-authentication that required I log in via privileged user first and then enter "enable" mode with enable password. Now, it logs in directly to enable mode instead. I cannot figure out how to re-add the user back so it requires that method first for extra security.
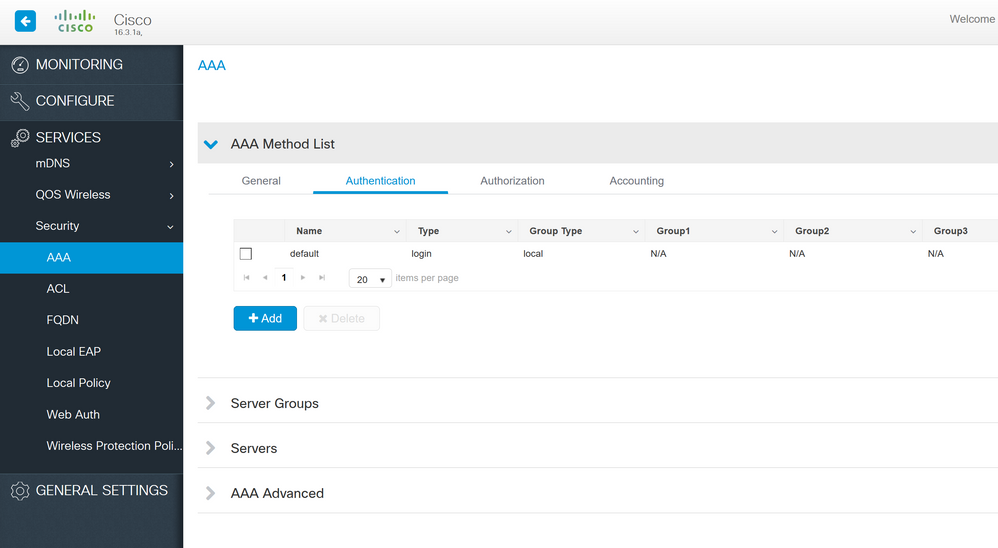
I'm using SecureCRT SSH2 protocol. I was able to access primary switch #1 via web gui using myusername still. I think I might be able to fix the issue via the interface there. See attached, not 100% sure though. Looks like the options are there, but I'd rather not fiddle until someone can clarify.
This is the only thing I see from the moment I log in (goes directly into enabled mode) and running that command, nothing else.
Cisco3650# Cisco3650#conf t Enter configuration commands, one per line. End with CNTL/Z. Cisco3650(config)#no aaa new-model Cisco3650(config)# Cisco3650(config)#end Cisco3650#wr Building configuration... Compressed configuration from 24401 bytes to 9027 bytes[OK] Cisco3650#
Here's a comparison of the 2 switches.
Switch #1 (main one trying to fix)
version 16.3 no service pad service timestamps debug datetime msec service timestamps log datetime msec service password-encryption service compress-config no service password-recovery no platform punt-keepalive disable-kernel-core ! hostname Cisco3650 ! ! vrf definition Mgmt-vrf ! address-family ipv4 exit-address-family ! address-family ipv6 exit-address-family ! ! no aaa new-model clock timezone EST -5 0 facility-alarm critical exceed-action shutdown switch 1 provision ws-c3650-24ts
Switch #2 (works correctly by logging into myusername first and manually having to enter "en" mode)
version 16.3 no service pad service timestamps debug datetime msec service timestamps log datetime msec service compress-config no service password-recovery no platform punt-keepalive disable-kernel-core ! hostname Switch2 ! ! vrf definition Mgmt-vrf ! address-family ipv4 exit-address-family ! address-family ipv6 exit-address-family ! no logging console enable secret 5 xxxxxxxxxxxxxxxx enable password TLNsxxxxxxxxxxxxxxxx ! no aaa new-model clock timezone EST -5 0 facility-alarm critical exceed-action shutdown switch 2 provision ws-c3650-24ts
PROBLEM #2
So in addition to the enable mode password issue on switch #1 I'm having this odd issue with switch #2 where it works fine (logs into myusername first, then into enable mode). However, it doesn't work with new enable password I set when I log in via VPN IP address which is already whitelisted in ACL and worked fine before I reset enable password. It's crazy, I log in just fine directly via SSH2 but via the VPN IP it no longer works. It works on myusername/pw but enable pw won't work. Same one works directly into switch. ACL config is 100% identical on switches #1 and #2 as well.
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2017 02:41 PM
If I understand you correctly, you have "privilege level" related issue. When you login with your username/password on SW#1 and have access to 'privilege level', you will need to change 'the privilege level' of the user to 'privilege 1'.
For the second problem, please check your configuration related with "line vty"-- mainly 'privilege level'. You can also share the output of the following command so that we can look at it: "sh run | s vty|privilege".
HTH,
Meheretab
Meheretab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2017 09:16 PM
Cisco3650#sh run | s vty|privilege username myusername privilege 15 secret 5 $1$xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx privilege 15 line vty 0 4 access-class Manage-SSH in exec-timeout 480 0 login local length 0 transport input ssh line vty 5 15 access-class Manage-SSH in exec-timeout 480 0 login local length 0 transport input ssh
Please assist from here. How do I get "myusername" forced to log in first prior to accessing enable mode? I want that extra layer of security.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2017 09:22 PM - edited 10-22-2017 09:25 PM
Hi,
Please change your configuration with the following:
username myusername privilege 1 secret 5 $1$xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx line vty 0 4 access-class Manage-SSH in exec-timeout 480 0 login local length 0 transport input ssh
transport output ssh line vty 5 15 access-class Manage-SSH in exec-timeout 480 0 login local length 0 transport input ssh
transport output ssh
I have changed the user "myusername" privilege level from level 15 (all commands access level) to level 1 (basic commands including show commands and enable).
I usually add "transport output ssh" command so that when I run remote session from the switch, it will use "SSH".
HTH,
Meheretab
Meheretab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2017 09:27 PM
This is how I had it originally but when I attempted to reset enable password, it got screwed up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2017 09:31 PM
HTH,
Meheretab
Meheretab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2017 09:37 PM
Here's a comparison of the 2 switches.
Switch #1 (main one trying to fix)
version 16.3 no service pad service timestamps debug datetime msec service timestamps log datetime msec service password-encryption service compress-config no service password-recovery no platform punt-keepalive disable-kernel-core ! hostname Cisco3650 ! ! vrf definition Mgmt-vrf ! address-family ipv4 exit-address-family ! address-family ipv6 exit-address-family ! ! no aaa new-model clock timezone EST -5 0 facility-alarm critical exceed-action shutdown switch 1 provision ws-c3650-24ts
Switch #2 (works correctly by logging into myusername first and manually having to enter "en" mode)
version 16.3 no service pad service timestamps debug datetime msec service timestamps log datetime msec service compress-config no service password-recovery no platform punt-keepalive disable-kernel-core ! hostname Switch2 ! ! vrf definition Mgmt-vrf ! address-family ipv4 exit-address-family ! address-family ipv6 exit-address-family ! no logging console enable secret 5 xxxxxxxxxxxxxxxx enable password TLNsxxxxxxxxxxxxxxxx ! no aaa new-model clock timezone EST -5 0 facility-alarm critical exceed-action shutdown switch 2 provision ws-c3650-24ts
Switch #1
control-plane service-policy input system-cpp-policy ! ! ! line con 0 exec-timeout 480 0 login local stopbits 1 line aux 0 stopbits 1 line vty 0 4 access-class Manage-SSH in exec-timeout 480 0 login local length 0 transport input ssh line vty 5 15 access-class Manage-SSH in exec-timeout 480 0 login local length 0 transport input ssh !
Switch #2
control-plane service-policy input system-cpp-policy ! ! ! line con 0 exec-timeout 480 0 login local stopbits 1 line aux 0 stopbits 1 line vty 0 4 access-class Manage-SSH in exec-timeout 480 0 login local length 0 transport input ssh line vty 5 15 access-class Manage-SSH in exec-timeout 480 0 login local length 0 transport input ssh !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2017 09:44 PM
HTH,
Meheretab
Meheretab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2017 10:14 PM
HTH,
Meheretab
Meheretab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 05:38 AM - edited 10-23-2017 05:39 AM
Here you go:
Cisco3650#sh run | s ssh ip ssh version 2 transport input ssh transport input ssh
I removed all interface/VLAN info from show run output as it's not needed for troubleshooting...
Cisco3650#show run
Building configuration...
Current configuration : 26017 bytes
!
! Last configuration change at 23:47:36 EST Sun Oct 22 2017
!
version 16.3
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
service compress-config
no service password-recovery
no platform punt-keepalive disable-kernel-core
!
hostname Cisco3650
!
!
vrf definition Mgmt-vrf
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
!
no aaa new-model
clock timezone EST -5 0
facility-alarm critical exceed-action shutdown
switch 1 provision ws-c3650-24ts
!
!
!
!
ip routing
!
!
!
ip name-server xxx.xxx.xxx.62 xxx.xxx.xxx.61
ip domain name companydomain.com
!
!
!
!
!
!
!
!
vtp mode transparent
!
!
crypto pki trustpoint HTTPS_SS_CERT_KEYPAIR
enrollment selfsigned
serial-number
revocation-check none
rsakeypair HTTPS_SS_CERT_KEYPAIR
!
!
crypto pki certificate chain HTTPS_SS_CERT_KEYPAIR
certificate self-signed 01
xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
quit
errdisable recovery cause udld
errdisable recovery cause bpduguard
errdisable recovery cause security-violation
errdisable recovery cause channel-misconfig
errdisable recovery cause pagp-flap
errdisable recovery cause dtp-flap
errdisable recovery cause link-flap
errdisable recovery cause gbic-invalid
errdisable recovery cause psecure-violation
errdisable recovery cause dhcp-rate-limit
errdisable recovery cause vmps
errdisable recovery cause loopback
errdisable recovery interval 120
license boot level ipbasek9
diagnostic bootup level minimal
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
username myusername privilege 15 secret 5 $1$xxxxxxxxxxxxxxxxxxxxxxxxxx
!
redundancy
mode sso
!
hw-switch switch 1 logging onboard message
!
class-map match-any system-cpp-police-topology-control
description Topology control
class-map match-any system-cpp-police-sw-forward
description Sw forwarding, SGT Cache Full, LOGGING
class-map match-any system-cpp-default
description DHCP snooping, show forward and rest of traffic
class-map match-any system-cpp-police-sys-data
description Learning cache ovfl, Crypto Control, Exception, EGR Exception, NFL SAMPLED DATA, Gold Pkt, RPF Failed
class-map match-any system-cpp-police-punt-webauth
description Punt Webauth
class-map match-any system-cpp-police-forus
description Forus Address resolution and Forus traffic
class-map match-any system-cpp-police-multicast-end-station
description MCAST END STATION
class-map match-any system-cpp-police-multicast
description Transit Traffic and MCAST Data
class-map match-any system-cpp-police-l2-control
description L2 control
class-map match-any system-cpp-police-dot1x-auth
description DOT1X Auth
class-map match-any system-cpp-police-data
description ICMP_GEN and BROADCAST
class-map match-any system-cpp-police-control-low-priority
description ICMP redirect and general punt
class-map match-any system-cpp-police-wireless-priority1
description Wireless priority 1
class-map match-any system-cpp-police-wireless-priority2
description Wireless priority 2
class-map match-any system-cpp-police-wireless-priority3-4-5
description Wireless priority 3,4 and 5
class-map match-any non-client-nrt-class
class-map match-any system-cpp-police-routing-control
description Routing control
class-map match-any system-cpp-police-protocol-snooping
description Protocol snooping
!
policy-map port_child_policy
class non-client-nrt-class
bandwidth remaining ratio 10
policy-map system-cpp-policy
class system-cpp-police-data
police rate 200 pps
class system-cpp-police-sys-data
police rate 100 pps
class system-cpp-police-sw-forward
police rate 1000 pps
class system-cpp-police-multicast
police rate 500 pps
class system-cpp-police-multicast-end-station
police rate 2000 pps
class system-cpp-police-punt-webauth
class system-cpp-police-l2-control
class system-cpp-police-routing-control
police rate 1800 pps
class system-cpp-police-control-low-priority
class system-cpp-police-wireless-priority1
class system-cpp-police-wireless-priority2
class system-cpp-police-wireless-priority3-4-5
class system-cpp-police-topology-control
class system-cpp-police-dot1x-auth
class system-cpp-police-protocol-snooping
class system-cpp-police-forus
class system-cpp-default
policy-map speed25
class class-default
police cir percent 25 conform-action transmit exceed-action drop
!
ip ssh version 2
!
ip access-list extended AutoQos-4.0-wlan-Acl-Bulk-Data
permit tcp any any eq 22
permit tcp any any eq 465
permit tcp any any eq 143
permit tcp any any eq 993
permit tcp any any eq 995
permit tcp any any eq 1914
permit tcp any any eq ftp
permit tcp any any eq ftp-data
permit tcp any any eq smtp
permit tcp any any eq pop3
ip access-list extended AutoQos-4.0-wlan-Acl-MultiEnhanced-Conf
permit udp any any range 16384 32767
permit tcp any any range 50000 59999
ip access-list extended AutoQos-4.0-wlan-Acl-Scavanger
permit tcp any any range 2300 2400
permit udp any any range 2300 2400
permit tcp any any range 6881 6999
permit tcp any any range 28800 29100
permit tcp any any eq 1214
permit udp any any eq 1214
permit tcp any any eq 3689
permit udp any any eq 3689
permit tcp any any eq 11999
ip access-list extended AutoQos-4.0-wlan-Acl-Signaling
permit tcp any any range 2000 2002
permit tcp any any range 5060 5061
permit udp any any range 5060 5061
ip access-list extended AutoQos-4.0-wlan-Acl-Transactional-Data
permit tcp any any eq 443
permit tcp any any eq 1521
permit udp any any eq 1521
permit tcp any any eq 1526
permit udp any any eq 1526
permit tcp any any eq 1575
permit udp any any eq 1575
permit tcp any any eq 1630
permit udp any any eq 1630
permit tcp any any eq 1527
permit tcp any any eq 6200
permit tcp any any eq 3389
permit tcp any any eq 5985
permit tcp any any eq 8080
ip access-list extended Manage-SSH
permit tcp host xxx.xxx.xxx.6 host 0.0.0.0 eq 22
permit tcp any host xxx.xxx.xxx.75 eq 22
permit tcp host xxx.xxx.xxx.10 host 0.0.0.0 eq 22
permit tcp host xxx.xxx.xxx.25 host 0.0.0.0 eq 22
!
access-list 1 permit xxx.xxx.xxx.25
access-list 101 permit tcp host xxx.xxx.xxx.25 host xxx.xxx.xxx.52 eq www
access-list 101 permit tcp host xxx.xxx.xxx.25 host xxx.xxx.xxx.52 eq 443
access-list 115 permit tcp host xxx.xxx.xxx.6 host 0.0.0.0 eq 22
!
snmp-server community public RO
snmp-server community private RW
!
control-plane
service-policy input system-cpp-policy
!
!
!
line con 0
exec-timeout 480 0
login local
stopbits 1
line aux 0
stopbits 1
line vty 0 4
access-class Manage-SSH in
exec-timeout 480 0
login local
length 0
transport input ssh
line vty 5 15
access-class Manage-SSH in
exec-timeout 480 0
login local
length 0
transport input ssh
!
ntp authenticate
ntp peer 81.6.42.224
ntp peer 96.47.67.105
ntp server 64.209.210.20
ntp server 50.255.89.205
wsma agent exec
profile httplistener
profile httpslistener
!
wsma agent config
profile httplistener
profile httpslistener
!
wsma agent filesys
profile httplistener
profile httpslistener
!
wsma agent notify
profile httplistener
profile httpslistener
!
!
wsma profile listener httplistener
transport http
!
wsma profile listener httpslistener
transport https
!
ap dot11 airtime-fairness policy-name Default 0
ap group default-group
ap hyperlocation ble-beacon 0
ap hyperlocation ble-beacon 1
ap hyperlocation ble-beacon 2
ap hyperlocation ble-beacon 3
ap hyperlocation ble-beacon 4
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 10:14 AM
I do not see any problem with the part of the configuration you shared. The only suggestion I have for you is to save your configuration (using 'write memory' or 'copy run start') and reboot the switch during maintenance window.
HTH,
Meheretab
Meheretab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 10:17 AM
@Meheretab Mengistu wrote:
The only thing I do not see in your command is the "enable secret" command. It should not affect the SSH login though.
No, that's the issue here. It *was* there before but now it's gone. I was given some advice from someone else here and followed their steps which ended up removing that user authentication despite the user being intact and with 15 privilege.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 10:39 AM
Usually when I have such a weird issue, I reboot the switch; it sometimes helps.
HTH,
Meheretab
Meheretab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 10:46 AM - edited 10-23-2017 10:47 AM
Ok did that, it added the line to show run output but still logging directly into enable mode, bypassing user authentication first.
enable secret 5 $1$U/xxxxxxxxxxxxxxxxxxx
I also just noticed it doesn't mention my username in that line, and says "5" instead of "15".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2017 10:53 AM
privilege level.
When you run 'sh run | s ssh|vty|enable|privilege' you will see all
configurations related with SSH. Post it here for one last-time. Also, do
not forget to save your configuration using 'wr mem' when you made a change.
HTH,
Meheretab
Meheretab
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide