- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: New To Vlan's - Configuring Vlan's With Sonic Wall
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
New To Vlan's - Configuring Vlan's With Sonic Wall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2019 11:28 AM
Hey There. Looking for some guidance.
Trying to refresh and re-learn vlan's on cisco gear. there is something i am missing as only vlan 1 will get internet, the rest, nothing. intervlan routing is working as i have enabled the ip route and DHCP is working to each vlan from my DHCP windows server. 2 main things that are getting me frustrated and that is internet to the other vlans and reaching my second switch.
I've added the route 0.0.0.0 .0.0.0.0 to 172.23.1.2 to get internet working on vlan 1
The other vlans, can reach other vlans and i can ping everything properly.
Just No internet. I read a few forums that say add static routes in my sonic wall, which i am trying to learn and figure out. i followed a tutorial to add a static route for vlan 2 but that still didn't work. from my core switch 1, i can ping all vlans interfaces etc etc.
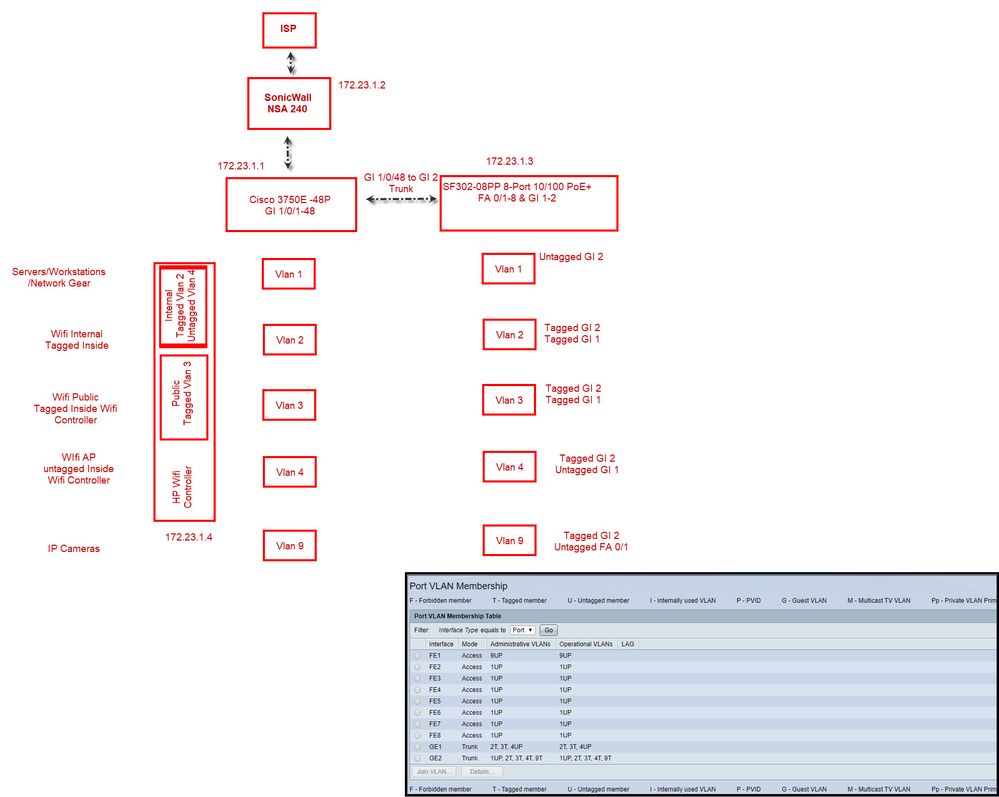
i also CANNOT ping or reach switch 2, 172.23.1.3, when i enable trunking on the first switch 172.23.1.1. even though my tag's and untags are working to get camera data from the switch 2, i cannot reach or ping this switch until i turn port 1/0/48 on switch 1 into access mode.
Here is my setup:
AD/DNS/DHCP - 172.23.1.150
attached is my running config form both switches.
what am i missing??
SW1
K-pup_Core#sh run
Building configuration...
Current configuration : 7393 bytes
!
version 12.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname K-pup_Core
!
boot-start-marker
boot-end-marker
!
enable secret 5 $1$3M1O$XNfgne.sdm4NfEDATxqjn/
enable password ******
!
username K-pup privilege 15 secret 5 $1$i/12$nKaFywyjvsL7hl8kIBSm71
!
!
no aaa new-model
switch 1 provision ws-c3750x-48p
system mtu routing 1500
ip routing
!
!
ip domain-name K-pup.com
!
!
crypto pki trustpoint TP-self-signed-4269839232
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-4269839232
revocation-check none
rsakeypair TP-self-signed-4269839232
!
!
crypto pki certificate chain TP-self-signed-4269839232
certificate self-signed 01
3082024C 308201B5 A0030201 02020101 300D0609 2A864886 F70D0101 04050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 34323639 38333932 3332301E 170D3933 30333031 30303031
32395A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D34 32363938
33393233 3230819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
8100A8C2 A2381905 9FCBFC41 AA501F01 08E8252A 6E8A46E1 44797633 878F86CE
F2923FE9 DF5B0CDB E2751CBA D8947B77 5F8EC618 062C5A26 6EDA7EE2 F8631CD6
A0FE8A08 7D957CB7 EC4FA5C8 E7BD9515 E15678A6 2436989E 8B502483 968196E7
79AAFEE8 13096BB5 59D12447 E33D702D 674FFC01 75D4EA07 438B80CD B52D3402
8B570203 010001A3 74307230 0F060355 1D130101 FF040530 030101FF 301F0603
551D1104 18301682 144B2D70 75705F43 6F72652E 4B2D7075 702E636F 6D301F06
03551D23 04183016 8014C6C1 9D35CCC7 579491A7 53BF08F7 6F370D3E 1EC6301D
0603551D 0E041604 14C6C19D 35CCC757 9491A753 BF08F76F 370D3E1E C6300D06
092A8648 86F70D01 01040500 03818100 7548A494 CE024170 13F09847 F16D2E86
A522B437 6B2B92E9 70425F77 05E59D76 82423152 36B861AB A19D5462 DDF9C05F
9A3F0733 70D85F44 96B2DF72 CAB3CD77 519A9251 59E7A4DA A138AE2F 39E3A33F
D62BC891 75016255 24ABDEC2 74948CB1 87026F86 CE8576EF EE56588B 9BD9A34A
D7773874 7ED4C174 B2BDE6FD 8795CC22
quit
spanning-tree mode pvst
spanning-tree extend system-id
!
!
!
!
vlan internal allocation policy ascending
!
ip ssh version 2
!
!
!
interface FastEthernet0
no ip address
no ip route-cache cef
no ip route-cache
no ip mroute-cache
shutdown
!
interface GigabitEthernet1/0/1
description K-pup_Room_1
spanning-tree portfast
!
interface GigabitEthernet1/0/2
description Wireless_Cont_Lan
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 2
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/3
description Wireless_Cont_Public
switchport access vlan 3
switchport trunk encapsulation dot1q
switchport trunk native vlan 3
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/4
description Wireless_AP_Basement
switchport trunk encapsulation dot1q
switchport trunk native vlan 4
switchport mode trunk
spanning-tree portfast
!
interface GigabitEthernet1/0/5
description Wireless_AP_Upstairs
switchport trunk encapsulation dot1q
switchport trunk native vlan 4
switchport trunk allowed vlan 2,3
switchport mode trunk
spanning-tree portfast
!
interface GigabitEthernet1/0/6
spanning-tree portfast
!
interface GigabitEthernet1/0/7
spanning-tree portfast
!
interface GigabitEthernet1/0/8
spanning-tree portfast
!
interface GigabitEthernet1/0/9
spanning-tree portfast
!
interface GigabitEthernet1/0/10
spanning-tree portfast
!
interface GigabitEthernet1/0/11
switchport access vlan 2
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/12
spanning-tree portfast
!
interface GigabitEthernet1/0/13
switchport trunk encapsulation dot1q
switchport trunk native vlan 4
switchport mode trunk
spanning-tree portfast
!
interface GigabitEthernet1/0/14
spanning-tree portfast
!
interface GigabitEthernet1/0/15
spanning-tree portfast
!
interface GigabitEthernet1/0/16
spanning-tree portfast
!
interface GigabitEthernet1/0/17
spanning-tree portfast
!
interface GigabitEthernet1/0/18
spanning-tree portfast
!
interface GigabitEthernet1/0/19
spanning-tree portfast
!
interface GigabitEthernet1/0/20
spanning-tree portfast
!
interface GigabitEthernet1/0/21
spanning-tree portfast
!
interface GigabitEthernet1/0/22
spanning-tree portfast
!
interface GigabitEthernet1/0/23
spanning-tree portfast
!
interface GigabitEthernet1/0/24
spanning-tree portfast
!
interface GigabitEthernet1/0/25
description Living-2B
spanning-tree portfast
!
interface GigabitEthernet1/0/26
spanning-tree portfast
!
interface GigabitEthernet1/0/27
spanning-tree portfast
!
interface GigabitEthernet1/0/28
spanning-tree portfast
!
interface GigabitEthernet1/0/29
spanning-tree portfast
!
interface GigabitEthernet1/0/30
spanning-tree portfast
!
interface GigabitEthernet1/0/31
spanning-tree portfast
!
interface GigabitEthernet1/0/32
spanning-tree portfast
!
interface GigabitEthernet1/0/33
spanning-tree portfast
!
interface GigabitEthernet1/0/34
spanning-tree portfast
!
interface GigabitEthernet1/0/35
spanning-tree portfast
!
interface GigabitEthernet1/0/36
spanning-tree portfast
!
interface GigabitEthernet1/0/37
switchport access vlan 2
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/38
description Cam_Living
switchport access vlan 9
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/39
switchport trunk encapsulation dot1q
switchport mode trunk
spanning-tree portfast
!
interface GigabitEthernet1/0/40
spanning-tree portfast
!
interface GigabitEthernet1/0/41
switchport access vlan 2
spanning-tree portfast
!
interface GigabitEthernet1/0/42
spanning-tree portfast
!
interface GigabitEthernet1/0/43
description Cam_Front_Left
switchport access vlan 9
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/44
spanning-tree portfast
!
interface GigabitEthernet1/0/45
spanning-tree portfast
!
interface GigabitEthernet1/0/46
spanning-tree portfast
!
interface GigabitEthernet1/0/47
description Cam_Back_Left
switchport access vlan 9
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/48
description Uplink_Garage
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 2-4,9
switchport mode trunk
spanning-tree portfast
!
interface GigabitEthernet1/1/1
!
interface GigabitEthernet1/1/2
!
interface GigabitEthernet1/1/3
!
interface GigabitEthernet1/1/4
!
interface TenGigabitEthernet1/1/1
!
interface TenGigabitEthernet1/1/2
!
interface Vlan1
ip address 172.23.1.1 255.255.255.0
!
interface Vlan2
description Wireless_Private
ip address 172.23.2.1 255.255.255.0
ip helper-address 172.23.1.150
!
interface Vlan3
description Wireless_Public
ip address 172.23.3.1 255.255.255.0
ip helper-address 172.23.1.150
!
interface Vlan4
description Wireless_AP's
ip address 172.23.4.1 255.255.255.0
ip helper-address 172.23.1.150
!
interface Vlan9
description Cameras
ip address 172.23.9.1 255.255.255.0
ip helper-address 172.23.1.150
!
ip classless
ip route 0.0.0.0 0.0.0.0 172.23.1.2
!
ip http server
ip http secure-server
!
ip sla enable reaction-alerts
!
!
!
line con 0
line vty 0 4
password ******
login local
transport input ssh
line vty 5 15
password ******
login
!
end
SW2
K-pup-SW2#sh run
config-file-header
K-pup-SW2
v1.4.0.88 / R800_NIK_1_4_194_194
CLI v1.0
set system mode switch
file SSD indicator encrypted
@
ssd-control-start
ssd config
ssd file passphrase control unrestricted
no ssd file integrity control
ssd-control-end cb0a3fdb1f3a1af4e4430033719968c0
!
vlan database
vlan 2-4,9
exit
voice vlan state disabled
voice vlan oui-table add 0001e3 Siemens_AG_phone________
voice vlan oui-table add 00036b Cisco_phone_____________
voice vlan oui-table add 00096e Avaya___________________
voice vlan oui-table add 000fe2 H3C_Aolynk______________
voice vlan oui-table add 0060b9 Philips_and_NEC_AG_phone
voice vlan oui-table add 00d01e Pingtel_phone___________
voice vlan oui-table add 00e075 Polycom/Veritel_phone___
voice vlan oui-table add 00e0bb 3Com_phone______________
green-ethernet energy-detect
hostname K-pup-SW2
line console
exec-timeout 0
exit
line ssh
exec-timeout 30
exit
enable password level 15 encrypted a17cb8fab036fcd14843dd338ab0e90e1741ccbc
username K-pup password encrypted a17cb8fab036fcd14843dd338ab0e90e1741ccbc privilege 15
ip ssh server
snmp-server location "K-pup Garage"
snmp-server contact K-pup
ip http timeout-policy 1800
clock timezone " " -7
clock source sntp
sntp unicast client poll
sntp server 172.23.1.150 poll
ip domain name k-pup.com
!
interface vlan 1
ip address 172.23.1.3 255.255.255.0
no ip address dhcp
!
interface vlan 2
name Wireless_Internal
!
interface vlan 3
name Wireless_Public
!
interface vlan 4
name Wireless_AP's
!
interface vlan 9
name Cameras
!
interface fastethernet1
description Cam_Garage_In
spanning-tree portfast
switchport mode access
switchport access vlan 9
!
interface fastethernet2
switchport mode access
!
interface fastethernet3
switchport mode access
!
interface fastethernet4
switchport mode access
!
interface fastethernet5
shutdown
switchport mode access
!
interface fastethernet6
switchport mode access
!
interface fastethernet7
switchport mode access
!
interface fastethernet8
switchport mode access
!
interface gigabitethernet1
description Wireless_AP
spanning-tree portfast
switchport trunk allowed vlan add 2-3
switchport trunk native vlan 4
!
interface gigabitethernet2
description Switch_Uplink
switchport trunk allowed vlan add 2-4,9
lldp notifications enable
!
exit
any help would be appreciated. been 2 days with me trying to figure out what routing i am missing to get internet to vlans. thanks!
- Labels:
-
LAN Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2019 11:46 AM
As per your post you able to communicate all the VLAN each other only internet not working if this correct.
Since SVI resides on 3750E switch, 172.23.2.1/ 3.1 so on,
1. SonicWALL required Static route back to 3750 for that VLAN since Sonicwall not aware of that routing tables
2. You required NAT for other VLAN IP address space to reach the internet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2019 06:02 PM
Thanks for the info. So your suggestions make sense, although firewalls aren't my strength. I have no idea how to do that on Sonic walls. I tried creating some static routes and still i got nothing when pinging from vlan 2 to the sonicwall. i have no idea how to do the NATTING part either to get internet part.
i have been trying to find a guide online with my similar setup but nothing i found is all about vlan's on the sonic wall.
what you said does make sense.
without creating routes, i am trying to understand rip routing so that i don't need to create the static routes everytime i create a new vlan. any thoughts on that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2019 12:52 AM
Sure if the SoniWAll can able to configured IGP protocol and most of the routing learn from IGP
here is static route :
NAt
RIP config :
http://help.sonicwall.com/help/sw/eng/7621/8/0/0/content/Policies_Network_RIP_Snwls.htm
Make sure you run same IGP on 3750 to learn routes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2019 01:21 PM
Thanks for the details. This is helping me learn alot! I appreciate it.
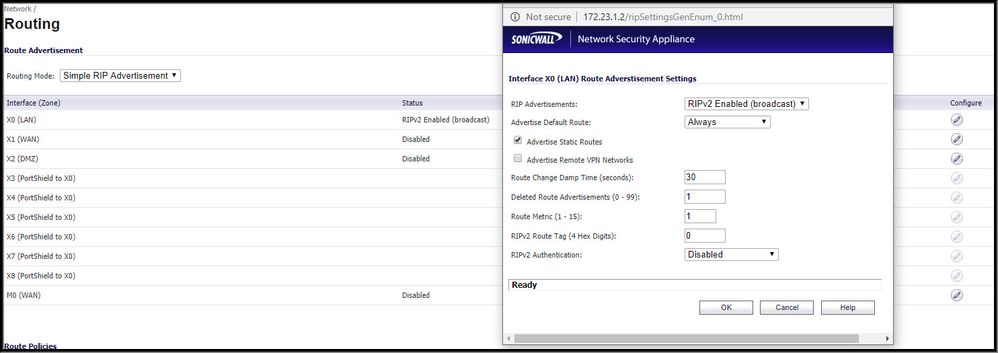
So instead of static routes, based on the reading, static routes isn't the best anyway on larger networks, i decided to use the RIP routing protocol.
So i enabled this on my sonic wall and trying to still learn what the metrics means:
I then went into my 3750 and enabled the same version:
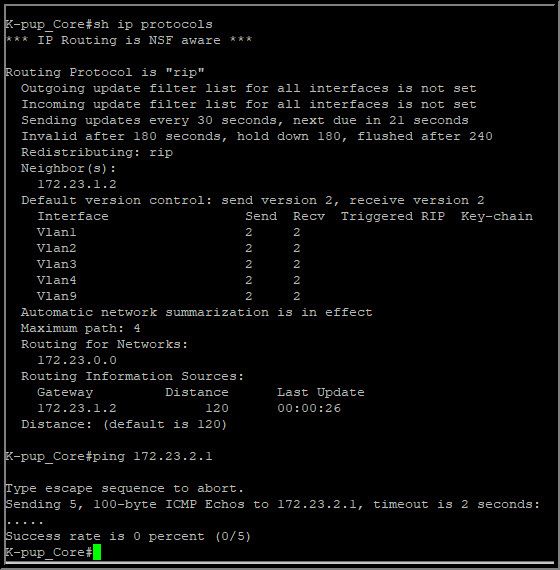
Does this look right to you?
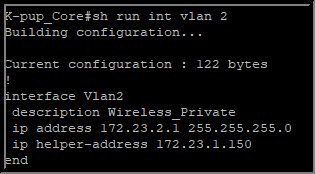
Also, the stupidest thing is happening now to me. I am unable to ping any vlan interface ip address anymore from my core switch??? if you see the image above, i cannot ping vlan 2 anymore:
Nothing has changed as far as I am aware. i confirmed that ip routing is enabled in the running config as well. but just in case i missed something, here is my running config as again
K-pup_Core#sh run
Building configuration...
Current configuration : 8291 bytes
!
version 12.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname K-pup_Core
!
boot-start-marker
boot-end-marker
!
enable secret 5 $1$3M1O$XNfgne.sdm4NfEDATxqjn/
enable password *****
!
username K-pup privilege 15 secret 5 $1$i/12$nKaFywyjvsL7hl8kIBSm71
!
!
no aaa new-model
switch 1 provision ws-c3750x-48p
system mtu routing 1500
ip routing
!
!
ip domain-name K-pup.com
!
!
crypto pki trustpoint TP-self-signed-4269839232
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-4269839232
revocation-check none
rsakeypair TP-self-signed-4269839232
!
!
crypto pki certificate chain TP-self-signed-4269839232
certificate self-signed 01
3082024C 308201B5 A0030201 02020101 300D0609 2A864886 F70D0101 04050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 34323639 38333932 3332301E 170D3933 30333031 30303031
32395A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D34 32363938
33393233 3230819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
8100A8C2 A2381905 9FCBFC41 AA501F01 08E8252A 6E8A46E1 44797633 878F86CE
F2923FE9 DF5B0CDB E2751CBA D8947B77 5F8EC618 062C5A26 6EDA7EE2 F8631CD6
A0FE8A08 7D957CB7 EC4FA5C8 E7BD9515 E15678A6 2436989E 8B502483 968196E7
79AAFEE8 13096BB5 59D12447 E33D702D 674FFC01 75D4EA07 438B80CD B52D3402
8B570203 010001A3 74307230 0F060355 1D130101 FF040530 030101FF 301F0603
551D1104 18301682 144B2D70 75705F43 6F72652E 4B2D7075 702E636F 6D301F06
03551D23 04183016 8014C6C1 9D35CCC7 579491A7 53BF08F7 6F370D3E 1EC6301D
0603551D 0E041604 14C6C19D 35CCC757 9491A753 BF08F76F 370D3E1E C6300D06
092A8648 86F70D01 01040500 03818100 7548A494 CE024170 13F09847 F16D2E86
A522B437 6B2B92E9 70425F77 05E59D76 82423152 36B861AB A19D5462 DDF9C05F
9A3F0733 70D85F44 96B2DF72 CAB3CD77 519A9251 59E7A4DA A138AE2F 39E3A33F
D62BC891 75016255 24ABDEC2 74948CB1 87026F86 CE8576EF EE56588B 9BD9A34A
D7773874 7ED4C174 B2BDE6FD 8795CC22
quit
spanning-tree mode pvst
spanning-tree extend system-id
!
!
!
!
vlan internal allocation policy ascending
!
ip ssh version 2
!
!
!
interface FastEthernet0
no ip address
no ip route-cache cef
no ip route-cache
no ip mroute-cache
shutdown
!
interface GigabitEthernet1/0/1
description K-pup_Room_1
spanning-tree portfast
!
interface GigabitEthernet1/0/2
description Wireless_Cont_Lan
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 2
switchport mode trunk
spanning-tree portfast
!
interface GigabitEthernet1/0/3
description Wireless_AP_Upstairs
switchport trunk encapsulation dot1q
switchport trunk native vlan 4
switchport trunk allowed vlan 2,3
switchport mode trunk
spanning-tree portfast
!
interface GigabitEthernet1/0/4
description Wireless_Cont_Public
switchport trunk encapsulation dot1q
switchport trunk native vlan 3
switchport mode trunk
spanning-tree portfast
!
interface GigabitEthernet1/0/5
description Wireless_AP_Basement
switchport trunk encapsulation dot1q
switchport trunk native vlan 4
switchport trunk allowed vlan 2,3
switchport mode trunk
spanning-tree portfast
!
interface GigabitEthernet1/0/6
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/7
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/8
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/9
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/10
switchport access vlan 2
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/11
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/12
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/13
switchport trunk encapsulation dot1q
switchport trunk native vlan 4
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/14
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/15
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/16
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/17
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/18
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/19
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/20
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/21
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/22
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/23
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/24
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/25
description Living-2B
switchport access vlan 2
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/26
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/27
switchport access vlan 9
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/28
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/29
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/30
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/31
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/32
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/33
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/34
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/35
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/36
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/37
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/38
description Cam_Living
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/39
switchport trunk encapsulation dot1q
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/40
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/41
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/42
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/43
description Cam_Front_Left
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/44
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/45
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/46
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/47
description Cam_Back_Left
switchport trunk encapsulation dot1q
switchport mode access
spanning-tree portfast
!
interface GigabitEthernet1/0/48
description Uplink_Garage
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 2-4,9
switchport mode trunk
spanning-tree portfast
!
interface GigabitEthernet1/1/1
!
interface GigabitEthernet1/1/2
!
interface GigabitEthernet1/1/3
!
interface GigabitEthernet1/1/4
!
interface TenGigabitEthernet1/1/1
!
interface TenGigabitEthernet1/1/2
!
interface Vlan1
ip address 172.23.1.1 255.255.255.0
!
interface Vlan2
description Wireless_Private
ip address 172.23.2.1 255.255.255.0
ip helper-address 172.23.1.150
!
interface Vlan3
description Wireless_Public
ip address 172.23.3.1 255.255.255.0
ip helper-address 172.23.1.150
!
interface Vlan4
description Wireless_AP's
ip address 172.23.4.1 255.255.255.0
ip helper-address 172.23.1.150
!
interface Vlan9
description Cameras
ip address 172.23.9.1 255.255.255.0
ip helper-address 172.23.1.150
!
router rip
version 2
network 172.23.0.0
neighbor 172.23.1.2
!
ip classless
ip route 0.0.0.0 0.0.0.0 172.23.1.2
!
ip http server
ip http secure-server
!
ip sla enable reaction-alerts
!
!
!
line con 0
line vty 0 4
password *****
login local
transport input ssh
line vty 5 15
password *****
login
!
end
K-pup_Core#
Thanks for the all the help. really love learning this stuff.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2019 01:50 PM
also, even if RIP routing is enabled and working, do I still need to enable NAT on the sonic wall for every vlan? i assume not since it has learnt all the vlans from rip routing on sonic wall interface X0 (LAN)?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide