- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Only 1 input cable for all vlans
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Only 1 input cable for all vlans
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2022 11:44 AM
I have a catalyst 3650-X switch and im setting up a netwotk with multiple vlans. The problem is that i dont want to have 1 cable pr vlan but just 1 cable that vcan deliver network to all my vlans. I tried using a trunk port but it only gives network to its native vlan. Can anybody tell me what im doing wrong?
- Labels:
-
Catalyst 3000
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2022 01:01 PM
as per the information you have allowed VLAN 1, 10 20 from the switch side, what is the other device and what config do you have other side?
when mentioned it only works native vlan (I take here as vlan 1) if other switch port belong to VLAN 10 or 20, they should be working ?
Again we need more information, what is other side device, where is Layer3 interface for all VLAN ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2022 02:08 PM - edited 09-11-2022 02:10 PM
you give us info about one side what about other side,
you config the port as trunk but are it work as truck ?
show interface x/y switchport
this give you is the port is trunk or not (share if you can)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2022 02:53 PM
The original poster asks "Can anybody tell me what im doing wrong?". We do not know nearly enough about what you have done to be able to suggest what might be wrong. What you have posted shows that there is a switch port configured as a trunk and carrying vlans 1, 10, 20 and that the trunking appears to be working (at least at layer 2). What we do not know includes:
1) what is this switch connected to on the trunk port? Would I be correct in guessing that it connects to some layer 3 device that is intended to supply routing for the 3 vlans?
2) If I am correct that the switch connects to some layer 3 device then how is this device configured?
3) Do devices in vlan 10 receive an IP address? If so are they able to ping their default gateway?
3) Do devices in vlan 20 receive an IP address? If so are they able to ping their default gateway?
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2022 08:01 AM
Sorry i have forgotten to look here🤦
First of all the trunk port is connected to the fiber box we get outr network from now. So its just an extention to the existing network.
You are right that it's connected to a layer 3 device but i cant check its configuration because its meant for use and not configuration (by the user)
vlan 10 and 20 can ping their default gateway (192.168.10.1 and 192.168.20.1 ant they can also ping 192.168.1.1 witch is the ip og the trunk port / vlan 1. But not out from the network.
You can see my whole config here. I made a few changes in it but i cant get it to work (i dont work in cli on a regular basis)
Building configuration...
Current configuration : 5294 bytes
!
version 12.2
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Switch
!
boot-start-marker
boot-end-marker
!
!
!
!
no aaa new-model
system mtu routing 1500
ip dhcp excluded-address 192.168.30.2 192.168.30.50
ip dhcp excluded-address 192.168.20.2 192.168.20.50
ip dhcp excluded-address 192.168.10.2 192.168.10.50
ip dhcp excluded-address 192.168.1.2 192.168.1.50
!
ip dhcp pool 1
network 192.168.1.0 255.255.255.0
default-router 192.168.1.1
dns-server 1.1.1.1 8.8.8.8
!
ip dhcp pool 10
network 192.168.10.0 255.255.255.0
default-router 192.168.10.1
dns-server 1.1.1.1 8.8.8.8
!
ip dhcp pool 20
network 192.168.20.0 255.255.255.0
default-router 192.168.20.1
dns-server 1.1.1.1 8.8.8.8
!
ip dhcp pool 30
network 192.168.30.0 255.255.255.0
default-router 192.168.30.1 255.255.255.0
dns-server 1.1.1.1 8.8.8.8
!
!
!
!
crypto pki trustpoint TP-self-signed-4142340096
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-4142340096
revocation-check none
rsakeypair TP-self-signed-4142340096
!
!
crypto pki certificate chain TP-self-signed-4142340096
certificate self-signed 01
3082023F 308201A8 A0030201 02020101 300D0609 2A864886 F70D0101 04050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 34313432 33343030 3936301E 170D3933 30333031 30303031
32305A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D34 31343233
34303039 3630819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
8100B5C1 B875D1AA 5CCA9FEF 024CD1DC 621E2B01 9F8E3635 5F136327 B2313461
F5D90093 1A67F07F 99FF2DE8 C859AAC3 9BF5BC65 0AE13513 81B6A232 6A20A614
043DB71D 274B3F2F D2E48060 8A20907A 2FD20D2B 1FCB8F80 34CA1D8A 505A6892
E2D80E20 D6C08CE2 DDF73F2B BA57E4DE C5EBF2C5 09DACF5B B5769D28 C36283C0
B5010203 010001A3 67306530 0F060355 1D130101 FF040530 030101FF 30120603
551D1104 0B300982 07537769 7463682E 301F0603 551D2304 18301680 14C15181
167445E0 EA6F4434 EE6AB744 FEC6F710 DF301D06 03551D0E 04160414 C1518116
7445E0EA 6F4434EE 6AB744FE C6F710DF 300D0609 2A864886 F70D0101 04050003
81810082 1B909F42 6A13A1E3 D52D734F A4DE0D01 C2FE99DA 332D82D8 528CBEB2
333B4E42 9EB368FB B6DF6E97 1718129D 6E8379FA 4C3F73B0 DE5966C1 6A3E3A85
E4C849F1 DBE2A4DF CF62535B 09B56155 1B443D72 DA44E110 EEC88AB8 71F6D030
83D6F08B 7D164A98 A87DC0F3 874D0C83 55E6D117 66973CB9 924E4152 45D930CB 7D93ED
quit
spanning-tree mode pvst
spanning-tree extend system-id
!
!
!
!
vlan internal allocation policy ascending
!
!
!
interface FastEthernet0
no ip address
!
interface GigabitEthernet0/1
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/2
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet0/3
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet0/4
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet0/5
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet0/6
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet0/7
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet0/8
switchport access vlan 10
switchport mode access
!
interface GigabitEthernet0/9
switchport access vlan 20
switchport mode access
!
interface GigabitEthernet0/10
switchport access vlan 20
switchport mode access
!
interface GigabitEthernet0/11
switchport access vlan 20
switchport mode access
!
interface GigabitEthernet0/12
switchport access vlan 20
switchport mode access
!
interface GigabitEthernet0/13
switchport access vlan 20
switchport mode access
!
interface GigabitEthernet0/14
switchport access vlan 20
switchport mode access
!
interface GigabitEthernet0/15
switchport access vlan 20
switchport mode access
!
interface GigabitEthernet0/16
switchport access vlan 20
switchport mode access
!
interface GigabitEthernet0/17
switchport access vlan 30
switchport mode access
!
interface GigabitEthernet0/18
switchport access vlan 30
switchport mode access
!
interface GigabitEthernet0/19
switchport access vlan 30
switchport mode access
!
interface GigabitEthernet0/20
switchport access vlan 30
switchport mode access
!
interface GigabitEthernet0/21
switchport access vlan 30
switchport mode access
!
interface GigabitEthernet0/22
switchport access vlan 30
switchport mode access
!
interface GigabitEthernet0/23
switchport access vlan 30
switchport mode access
!
interface GigabitEthernet0/24
switchport access vlan 30
switchport mode access
!
interface GigabitEthernet1/1
!
interface GigabitEthernet1/2
!
interface GigabitEthernet1/3
!
interface GigabitEthernet1/4
!
interface TenGigabitEthernet1/1
!
interface TenGigabitEthernet1/2
!
interface Vlan1
ip address 192.168.1.1 255.255.255.0
!
interface Vlan2
no ip address
!
interface Vlan10
ip address 192.168.10.1 255.255.255.0
!
interface Vlan20
ip address 192.168.20.1 255.255.255.0
!
interface Vlan30
ip address 192.168.30.1 255.255.255.0
!
ip classless
ip http server
ip http secure-server
!
!
!
line con 0
line vty 0 4
login
line vty 5 15
login
!
end
Switch#show vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active
10 VLAN0010 active Gi0/2, Gi0/3, Gi0/4, Gi0/5
Gi0/6, Gi0/7, Gi0/8
20 VLAN0020 active Gi0/9, Gi0/10, Gi0/11, Gi0/12
Gi0/13, Gi0/14, Gi0/15, Gi0/16
30 VLAN0030 active Gi0/17, Gi0/18, Gi0/19, Gi0/20
Gi0/21, Gi0/22, Gi0/23, Gi0/24
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------
1 enet 100001 1500 - - - - - 0 0
10 enet 100010 1500 - - - - - 0 0
20 enet 100020 1500 - - - - - 0 0
30 enet 100030 1500 - - - - - 0 0
1002 fddi 101002 1500 - - - - - 0 0
1003 tr 101003 1500 - - - - - 0 0
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------
1004 fdnet 101004 1500 - - - ieee - 0 0
1005 trnet 101005 1500 - - - ibm - 0 0
Remote SPAN VLANs
------------------------------------------------------------------------------
Primary Secondary Type Ports
------- --------- ----------------- ------------------------------------------
Switch#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2022 08:33 AM - edited 11-29-2022 08:35 AM
.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2022 08:36 AM - edited 11-29-2022 08:39 AM
woops this reply was meant for another comment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2022 11:09 AM
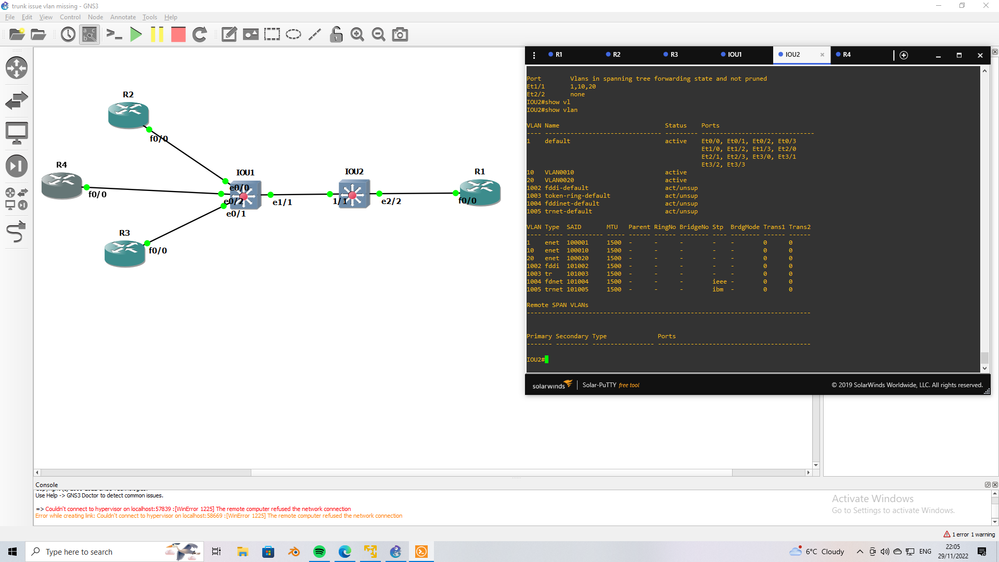
I run small lab
in IOU1 and IOU2 you need
interface x/x
switchport truck encap dot1q
switchport mode trunk <<-this need
switchport trunk native vlan 1
in IOU1 and IO2
you need to add vlan to database by
vlan 10
vlan 20
that it.
and it work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2022 11:20 AM
Oh that seems pretty straight forward. Thank you. But I’m not sure what an iou is and I don’t think what I can find on google makes sense. Can you give a quick explanation on what it is?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2022 12:13 PM
IOU is L2 image of GNS3VM.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide