- Cisco Community
- Technology and Support
- Networking
- Switching
- Promiscuous port mapping to different Isolated PVLANs within a single Primary PVLAN?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Promiscuous port mapping to different Isolated PVLANs within a single Primary PVLAN?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2019 12:16 PM
Hello,
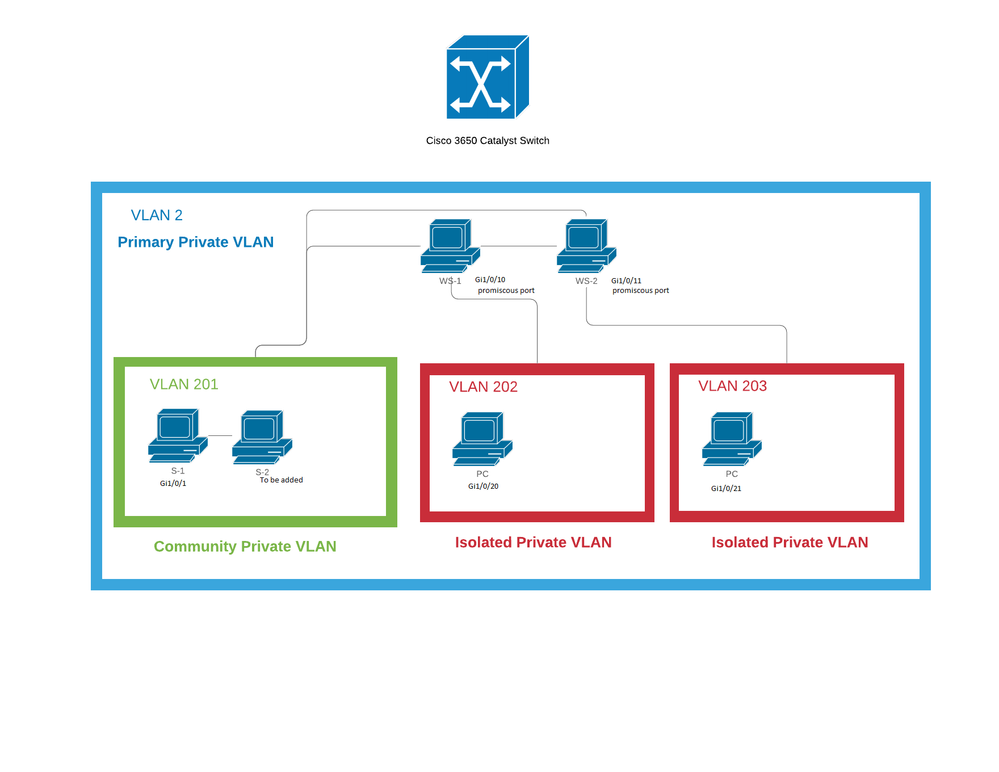
I am working on a unique system & switch configuration where there are middle-man workstations that communicate with each other and a community of servers. Each workstation must also be able to communicate with one single isolated workstation/PC. This is all being configured on one Catalyst 3650 switch. Below is a diagram depicting the goal of the project.
I have been able to create the proper communication between VLAN 201 (i.e servers), WS-1, and VLAN 202 (isolated PC 1) with this config guide https://learningnetwork.cisco.com/docs/DOC-16110. With my current configuration, WS-1 can ping VLAN 202 and VLAN 201 but VLAN 201 and VLAN 202 cannot ping each other.
When I attempt to expand the configuration by adding a second workstation and isolated VLAN to the primary VLAN I am getting errors stating that only 1 isolated VLAN can be associated with the primary VLAN.
Switch(config)#int Gi1/0/11 Switch(config-if)#switchport mode private-vlan promiscuous Switch(config-if)#switchport private-vlan mapping 2 203 %Command rejected: invalid private vlan association between vlan2 and vlan203. Isolated VLAN 202 is already associated with VLAN 2. Switch(config-if)#exit
Is it possible to configure promiscuous ports with there own isolated PVLAN as a workaround to avoid having multiple isolated PVLANS on the Primary PVLAN?
Is this config even viable for what I am looking to accomplish?
Thanks!
Current Config Info
Primary Secondary Type Ports ------- --------- ----------------- ------------------------------------------ 2 201 community Gi1/0/1, Gi1/0/10, Gi1/0/11 2 202 isolated Gi1/0/10, Gi1/0/20 none 203 isolated ! vlan 2 name prim-vlan private-vlan primary private-vlan association 201-202 end ! vlan 201 name server-comm private-vlan community end ! vlan 202 name iso-1 private-vlan isolated end ! vlan 203 name iso-2 private-vlan isolated end ! interface GigabitEthernet1/0/1 switchport private-vlan host-association 2 201 switchport mode private-vlan host end ! interface GigabitEthernet1/0/10 switchport private-vlan mapping 2 201-202 switchport mode private-vlan promiscuous end Current configuration : 120 bytes ! interface GigabitEthernet1/0/11 switchport private-vlan mapping 2 201 switchport mode private-vlan promiscuous end ! interface GigabitEthernet1/0/20 switchport private-vlan host-association 2 202 switchport mode private-vlan host end ! interface GigabitEthernet1/0/21 end
- Labels:
-
Catalyst 3000
-
LAN Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2019 02:41 PM
I don't think you can do it with this MITM computers on the path. I suggest to make inter-vlan routing and with ACLs limit which hosts/vlans can comunicate with others
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide