- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: PVLAN and promiscuos port
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2010 03:01 AM - edited 03-06-2019 02:16 PM
Hi to all, i'm Fabio and i have the following scenario:
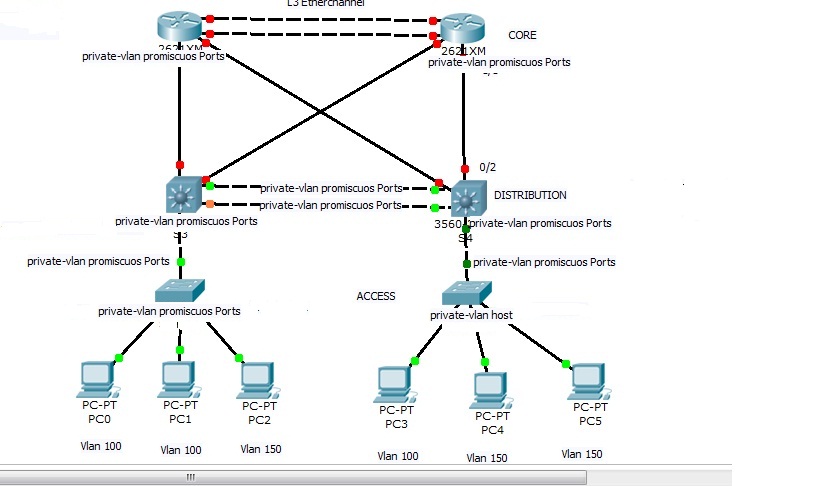
->PC1 cannot communicate with PC3
->PC3 cannot communicate with PC1
->PC1, PC3 can communicate with PC0
As indicated by Peter in a different thread, https://supportforums.cisco.com/thread/2054922, i created an isolated pvlan for PC1, PC3 and a primary Vlan for PC 0 in order to satisfy requests.
My questions are:
1)I have to configure primary vlan and secondary vlan in all switches (access, distribution, core)? I think yes, because PVLAN doesn't support VTP
2)Based on the scenario showed, is correct my interface configuration plane? I mean, i need to configure all carry traffic interfaces as promiscuos interfaces, excluded tha access interface to PC 1,3 configured as "switchport mode private-vlan host"?
3)Finally, because of the presence of normal VLAN and private VLAN, i have to configure interfaces of access switch both in "access-mode" (access to vlan 100, 150) and "switchport mode private-vlan host"?
Thanks, regards Fabio.
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2010 11:49 AM
Hi Fabio,
Sorry for responding lately.
As indicated by Peter in a different thread, https://supportforums.cisco.com/thread/2054922, i created an isolated pvlan for PC1, PC3 and a primary Vlan for PC 0 in order to satisfy requests.
Correct but perhaps not described entirely precisely. What you need to do is to create a primary VLAN, then create another secondary isolated VLAN and associate it with the primary VLAN. PC1 and PC3 will be assigned to the secondary isolated PVLAN using the commands switchport mode private-vlan host and switchport private-vlan host-association primary-VLAN secondary-VLAN. In addition, you declare the port to PC0 as promiscuous port using the commands switchport mode private-vlan promiscuous and switchport private-vlan mapping primary-VLAN secondary-VLAN-list
1)I have to configure primary vlan and secondary vlan in all switches (access, distribution, core)? I think yes, because PVLAN doesn't support VTP
Yes. The primary and secondary VLANs have to be manually created on all switches including their types and attributes (primary, secondary community, secondary isolated, association under the primary VLAN). If using the VTPv3, however, this is not necessary - the VTPv3 will distribute this information automatically among all VTPv3-compliant switches.
2)Based on the scenario showed, is correct my interface configuration plane? I mean, i need to configure all carry traffic interfaces as promiscuos interfaces, excluded tha access interface to PC 1,3 configured as "switchport mode private-vlan host"?
No, I am afraid that port types you have suggested are wrong. All inter-switch links shall be configured as normal trunks. Only ports to end stations shall be configured either as host ports or promisc ports. Note that the host port or the promisc port is very similar to an access port - it does not perform tagging and it belongs only to a single VLAN (the host port belongs to a particular secondary VLAN, the promisc port belongs to a particular primary VLAN). Because inter-switch links will possibly carry frames from different VLANs, these absolutely must be configured as trunks.
So - inter-switch links should be normal trunks. Ports to PC1 and PC3 will be private-vlan host, and port to the PC0 will be private-vlan promisc.
3)Finally, because of the presence of normal VLAN and private VLAN, i have to configure interfaces of access switch both in "access-mode" (access to vlan 100, 150) and "switchport mode private-vlan host"?
No. There is no normal VLAN in this case. The private VLAN is actually a system of VLANs, visible from outside by the primary VLAN and internally divided into subgroups using the secondary VLANs. But the entire system consisting of the primary VLAN and the associated secondary VLANs is actually what is called the "Private VLAN". Thus, there shall be no access VLAN defined.
Let's assume that we have the primary VLAN 100, and secondary VLANs 101, 102, and 103. The 101 and 102 are community VLANs, the 103 is an isolated secondary VLAN. The example configuration of individual ports would be as follows:
interface FastEthernet0/1
! This is a community port in secondary VLAN 101
switchport private-vlan host-association 100 101
switchport mode private-vlan host
interface FastEthernet0/2
! This is a community port in secondary VLAN 102
switchport private-vlan host-association 100 102
switchport mode private-vlan host
interface FastEthernet0/3
! This is an isolated port in secondary VLAN 103
switchport private-vlan host-association 100 103
switchport mode private-vlan host
interface FastEthernet0/4
! This is a promisc port
switchport private-vlan mapping 100 101-103
switchport mode private-vlan promiscuous
Please feel free to ask further.
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2010 11:49 AM
Hi Fabio,
Sorry for responding lately.
As indicated by Peter in a different thread, https://supportforums.cisco.com/thread/2054922, i created an isolated pvlan for PC1, PC3 and a primary Vlan for PC 0 in order to satisfy requests.
Correct but perhaps not described entirely precisely. What you need to do is to create a primary VLAN, then create another secondary isolated VLAN and associate it with the primary VLAN. PC1 and PC3 will be assigned to the secondary isolated PVLAN using the commands switchport mode private-vlan host and switchport private-vlan host-association primary-VLAN secondary-VLAN. In addition, you declare the port to PC0 as promiscuous port using the commands switchport mode private-vlan promiscuous and switchport private-vlan mapping primary-VLAN secondary-VLAN-list
1)I have to configure primary vlan and secondary vlan in all switches (access, distribution, core)? I think yes, because PVLAN doesn't support VTP
Yes. The primary and secondary VLANs have to be manually created on all switches including their types and attributes (primary, secondary community, secondary isolated, association under the primary VLAN). If using the VTPv3, however, this is not necessary - the VTPv3 will distribute this information automatically among all VTPv3-compliant switches.
2)Based on the scenario showed, is correct my interface configuration plane? I mean, i need to configure all carry traffic interfaces as promiscuos interfaces, excluded tha access interface to PC 1,3 configured as "switchport mode private-vlan host"?
No, I am afraid that port types you have suggested are wrong. All inter-switch links shall be configured as normal trunks. Only ports to end stations shall be configured either as host ports or promisc ports. Note that the host port or the promisc port is very similar to an access port - it does not perform tagging and it belongs only to a single VLAN (the host port belongs to a particular secondary VLAN, the promisc port belongs to a particular primary VLAN). Because inter-switch links will possibly carry frames from different VLANs, these absolutely must be configured as trunks.
So - inter-switch links should be normal trunks. Ports to PC1 and PC3 will be private-vlan host, and port to the PC0 will be private-vlan promisc.
3)Finally, because of the presence of normal VLAN and private VLAN, i have to configure interfaces of access switch both in "access-mode" (access to vlan 100, 150) and "switchport mode private-vlan host"?
No. There is no normal VLAN in this case. The private VLAN is actually a system of VLANs, visible from outside by the primary VLAN and internally divided into subgroups using the secondary VLANs. But the entire system consisting of the primary VLAN and the associated secondary VLANs is actually what is called the "Private VLAN". Thus, there shall be no access VLAN defined.
Let's assume that we have the primary VLAN 100, and secondary VLANs 101, 102, and 103. The 101 and 102 are community VLANs, the 103 is an isolated secondary VLAN. The example configuration of individual ports would be as follows:
interface FastEthernet0/1
! This is a community port in secondary VLAN 101
switchport private-vlan host-association 100 101
switchport mode private-vlan host
interface FastEthernet0/2
! This is a community port in secondary VLAN 102
switchport private-vlan host-association 100 102
switchport mode private-vlan host
interface FastEthernet0/3
! This is an isolated port in secondary VLAN 103
switchport private-vlan host-association 100 103
switchport mode private-vlan host
interface FastEthernet0/4
! This is a promisc port
switchport private-vlan mapping 100 101-103
switchport mode private-vlan promiscuous
Please feel free to ask further.
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2010 03:26 AM
Fabio,
There is an RFC you may be interested in reading about Private VLANs - the RFC 5517 describing them in more detail. See
http://tools.ietf.org/html/rfc5517
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2010 03:04 AM
Hi Peter,
thanks i need to implement your suggestion. I read it and know i'm going to analyze it. Thanks, good job.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
