- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Redundancy on 3650 using Virtual Stacking
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Redundancy on 3650 using Virtual Stacking
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2019 10:33 AM
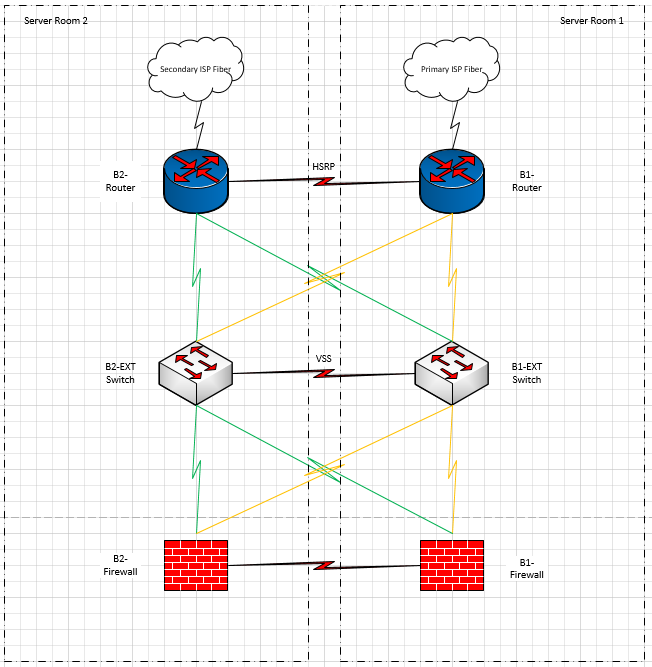
I am using 2 WS-C3650-24TD's for my external switch stack. They are both currently located in one of my two server rooms. I was hoping to move one to the other server room, for better redundancy. I thought that I could do a virtual stack between them however it doesn't look like it is supported. Any thoughts or advice on how to get this done. Attached a picture of where I am trying to go.
RTR - 4451 - 03.16.06.S
SW - 3650 - 03.06.06E
FW - FPR 2120
- Labels:
-
Catalyst 3000
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2019 10:41 AM
Sorry image didn't take.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2019 12:16 PM
Well I dont think you need to move one of the switches to the second IT room, instead you can have a physical redundancy to the second ISP router
obviously depend on how far are the IT rooms
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2019 12:21 PM - edited 09-03-2019 12:33 PM
Hello Stacia,
you cannot build a stack using fiber based 10 GE links on C3650 in your IOS XE version.
see
Restrictions for Switch Stacks
The following are restrictions for your switch stack configuration:
-
Switch stacks running the LAN Base license level do not support Layer 3 features.
-
A switch stack can have up to nine stacking-capable switches connected through their StackWise-160 ports.
-
You cannot have a switch stack containing a mix of Catalyst 3850 and Catalyst 3650 switches.
The stack cable can be only up to 3 meters (or 5 meters ) so it is not possible to keep the stack and move a switch in the other server room.
To be able to put the switches in different server rooms and to interconnect them with fiber based links you should remove the stack configuration and use each of them as indipendent switches.
But if you do that STP will be running on you topology.
And the the two devices will act as indipendent boxes so you would need to use HSRP/VRRP for providing a VIP next-hop to other devices if using static routes.
Please note that for B1 and B2 routers could use two different Vlans one on switch B1 and one on switch B2 and to provide two HSRP groups.
To make each router to have boths links in the same subnet you should use IRB, BVI interface and bridge group.
If you do that STP will block some links.
The same reasoning applies for interconnections to devices after the switches ( I mean the firewalls).
In case you choice to make the switches indipendent for moving one in the other server room I would suggest to consider using two Vlans one on Switch B1 and one on switch B2.
The same I would use two different Vlans to the ASA firewalls one hosted on switch B1 and one on switch B2.
(if the switches work only at OSI layer 2 the routers will use two Vlans to communicate with the firewalls but the same reasoning apply just L2 config is not performed on the switches).
At this point you wouldn't need to connect the two switches between themselves and you have two separated failure domains.
This was the way we made POPs many years ago before VSS and using two catalyst 6500 just as L2 switches.
Hope to help
Giuseppe
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide