- Cisco Community
- Technology and Support
- Networking
- Switching
- Routing over switchport but within VLAN/VRF
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Routing over switchport but within VLAN/VRF
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-18-2014 08:33 AM - edited 03-07-2019 06:16 PM
I currently have the topology as per the diagram below on the ‘Internal’ side.
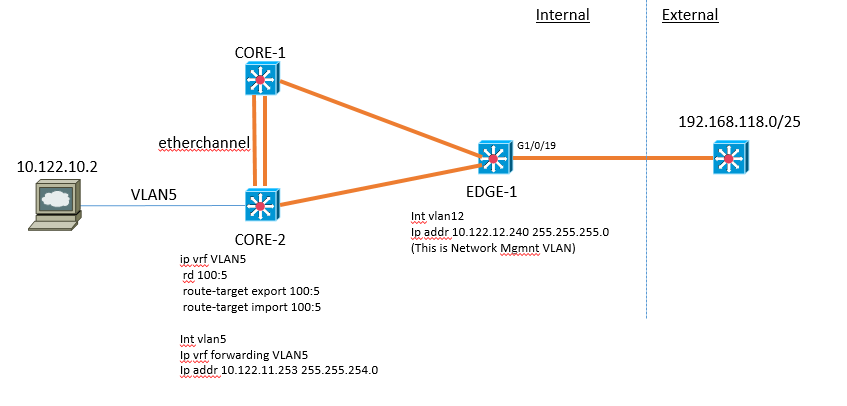
There is OSPF/BGP between the two cores.
VTP is used to ensure all the necessary VLANs are propagated to the edge switches.
I now have the requirement to connect one of the edge switchports to an external link so that clients on the external side of the link (192.168.118.0/24) can access a web server connected to CORE-01 as shown (10.122.10.2).
The question is how do I achieve this? I obviously need the route adding into the VLAN5 VRF, but where do I point it to and how do I point it down g1/0/19 on the edge switch? How will traffic coming into g1/0/19 on the edge switch know to be in VLAN 5 ?
I know I need to add access-lists somewhere too.
Any advice would be very warmly welcomed.
- Labels:
-
LAN Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2014 05:26 AM
Hi Jon,
Yes that makes much more sense thanks.
I beleive the config will look something like this then....(I think I need two routes on the edge switch as shown).
EDGE
Ip routing
Int gn/n/n
No switchport
Ip address 10.122.50.1 255.255.255.252 (10.122.50.2/30 at other[external] end)
Ip access-group 101 in
Ip access-group 102 out
Access-list 101 permit tcp 192.168.118.0 0.255.255.255 10.122.10.2 eq 443
Access-list 101 deny ip any any
Access-list 101 deny esp any any
Access-list 102 permit tcp 10.122.10.2 eq 443 192.168.118.0 0.255.255.255
Access-list 102 deny ip any any
Access-list 102 deny esp any any
Int vlan51
Desc For routing between core-edge
Ip addr 10.122.51.1 255.255.255.248
ip route 10.122.10.2 255.255.255.255 10.122.51.6 (hsrp addr on cores)
ip route 192.168.118.0 255.255.255.0 10.122.50.1 (or should this be .2?)
CORE-1
Vlan 51 name “For routing between core-edge”
Int vlan51
Desc For routing between core-edge
Ip addr 10.122.51.2 255.255.255.248
Ip vrf forwarding VLAN5
standby 51 ip 10.122.51.6
standby 51 priority 120
standby 51 preempt
ip route vrf VLAN5 192.168.118.0 0.0.0.255 10.122.51.1
CORE-2
Int vlan51
Desc For routing between core-edge
Ip addr 10.122.51.3 255.255.255.248
Ip vrf forwarding VLAN5
standby 51 ip 10.122.51.6
standby 51 preempt
ip route vrf VLAN5 192.168.118.0 0.0.0.255 10.122.51.1
Do you concur?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2014 05:50 AM
Steve
Yes you do need two routes on edge switch, one for the web server and one for the client. Looks good , just a few points -
1) you acls need to include the "host" keyword and the wildcard masks are wrong ie. -
access-list 101 permit tcp 192.168.118.0 0.0.0.255 host 10.122.10.2 eq 443
access-list 101 deny ip any any
access-list 101 deny esp any any
line 2 there is an implicit deny at the end of any acl so you don't need to have an entry unless you want to see how many hits there are.
line 3 - not sure what this is for ?
the above comments also apply to acl 102
2) your routes -
ip route 192.168.118.0 255.255.255.0 10.122.50.1 (or should this be .2?)
it should be 10.122.50.2
also note your VRF routes are using the wrong masks ie. they should be -
ip route vrf VLAN5 192.168.118.0 255.255.255.0 10.122.51.1
Jon
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2014 06:09 AM
Brilliant. Thanks very much Jon.
Ignore my line three, been faffing about with firewalls and permitting GRE tunnels.
Your input has been invaluable, and now that I've done it I can see the logic behind it.
Thanks again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2014 06:33 AM
Steve
No problem.
Would be interested to hear how it all goes when you get round to implementing it.
Jon
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide