- Cisco Community
- Technology and Support
- Networking
- Switching
- Hello Ganesh,
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2016 02:34 AM - edited 03-08-2019 03:30 AM
Hello,
I have a Cisco SG300-28 in Layer 3 mode and configured routing between VLANs. I have 3 VLANs.
VLAN 10: 10.1.10.0\24
VLAN 20: 10.1.20.0\24
VLAN 99: 192.168.178.0\24
Right now VLAN 10 can communicate with VLAN 20 and VLAN 20 can communicate with VLAN 10.
But now I want VLAN 10 can communicate with any PC in VLAN 20 but VLAN 20 cannot communicate with VLAN 10. I heard this should work with a "reflexive ACL"?! Does the SG300-28 support reflexive ACL?
Thanks
Markus
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2016 10:34 PM
Hello,I have a Cisco SG300-28 in Layer 3 mode and configured routing between VLANs. I have 3 VLANs.VLAN 10: 10.1.10.0\24VLAN 20: 10.1.20.0\24VLAN 99: 192.168.178.0\24Right now VLAN 10 can communicate with VLAN 20 and VLAN 20 can communicate with VLAN 10.But now I want VLAN 10 can communicate with any PC in VLAN 20 but VLAN 20 cannot communicate with VLAN 10. I heard this should work with a "reflexive ACL"?! Does the SG300-28 support reflexive ACL?ThanksMarkus
Hello Markus,
Have you seen the below thread which gives better explanation of ACL implementation on SG300.
Hope it Helps..
-GI
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2016 10:34 PM
Hello,I have a Cisco SG300-28 in Layer 3 mode and configured routing between VLANs. I have 3 VLANs.VLAN 10: 10.1.10.0\24VLAN 20: 10.1.20.0\24VLAN 99: 192.168.178.0\24Right now VLAN 10 can communicate with VLAN 20 and VLAN 20 can communicate with VLAN 10.But now I want VLAN 10 can communicate with any PC in VLAN 20 but VLAN 20 cannot communicate with VLAN 10. I heard this should work with a "reflexive ACL"?! Does the SG300-28 support reflexive ACL?ThanksMarkus
Hello Markus,
Have you seen the below thread which gives better explanation of ACL implementation on SG300.
Hope it Helps..
-GI
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-24-2016 11:50 PM
Hello Ganesh,
thanks for your reply. The explanation to open just one port is a good idea and helps me in most cases.
But I think it wont help me if I have the following example:
I have 2 Windows-PCs. PC1 is in VLAN 10. PC2 is in VLAN20. I want to copy some files via SMB from PC1 to PC2.
So I have to open the Port(s) for SMB from VLAN10 to VLAN20 and from VLAN20 to VLAN10. The second rule is neccessary to receive the answer packages. But if I open the Ports for VLAN20 to VLAN10 PC2 can access the Shares of PC1 too. And that's what I don't want.
Theirfor I wanted to create a ACE-Rule which only allow Packages from VLAN20 to VLAN10 which where established in VLAN10.
Markus
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-25-2016 04:42 AM
Hi,
Provided your SMB implementation uses TCP as a transport protocol (natively through port 445 or via NBT through port 139) you can try to filter traffic from VLAN20 to VLAN10 based on ACK or RST flags. You would create an ACL with two "permit tcp" entries using "match-all +ack" and "match-all +rst" parameters respectively.
Best regards,
Antonin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2016 04:55 AM
It works now.
I created a ACE with the following parameters in the screenshots.
VLAN20 can now access the SMB-shares from VLAN10 but VLAN10 can't access SMB-shares from VLAN20.

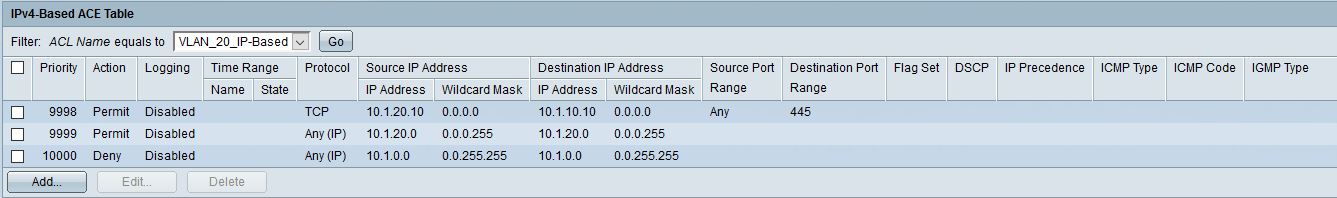
Thanks to both of you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2017 02:03 AM
Is this really works? the way i see it. you still permitted TCP traffic to flow both ways. from vlan 10 to vlan 20. and vlan 20 to vlan 10. Im having the same problem with my SG350 series. most switches uses "permit tcp any any -established-"in CLI. That way vlan will respond only to established connection and cannot start a 3 way handshake.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
