- Cisco Community
- Technology and Support
- Networking
- Switching
- Tricky HSRP problem - failover without IP SLA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2012 04:19 AM - edited 03-07-2019 08:46 AM
Hi all,
Once again, I need the help of the community if possible.
Below is a basic image of the HSRP and backup link setup for our LAN.
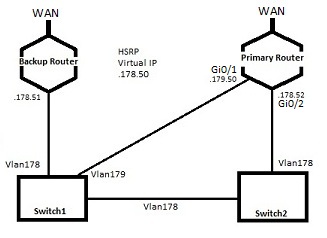
The virtual IP 192.168.178.50 resides on the primary router and fails over to the backup router. Internal default gateways for the switches are set to 178.50.
Switch1 is Layer3 and has two static default routes configured as:
ip route 0.0.0.0 0.0.0.0 192.168.179.50 track 1 - - - (interface line-protocol track)
ip route 0.0.0.0 0.0.0.0 192.168.178.50 2
And the primary router has a static route out 179.50 which tracks the interface (route goes down if interface is down), and a backup static route.
ip route (internal LAN) Gi0/1 track 1 - - - (interface line-protocol track)
ip route (internal LAN) Gi0/2 2
Everything works fine. If the primary router fails, Switch1 tears down the route across Vlan179, HSRP fails over the IP to the backup router and routing continues as normal. If the link across Vlan179 fails, the routers tear down the primary routes and again, things continue as normal.
The problem comes when the primary WAN link fails but the router remains up. This means the default route is still across Vlan179. Normally, Id set an IP SLA on Switch1 to track the WAN link BUT Switch1 only has the BASE IOS and the company wont pay for the Advanced IP IOS so I dont have IP SLA as an option.
How can I get the static default route to failover in the event that only the primary WAN link goes down?
Any help is greatly appreciated.
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2012 11:50 AM
Hi Paul,
How can I stop EIGRP advertising routes inwards other than the default route?
ip summary-address eigrp 6000 0.0.0.0 0.0.0.0
Yes, if this command is applied on the primary/backup router interfaces towards the switches, it will cause the EIGRP-advertised routes to be summarized to 0.0.0.0/0. However, I suggest a slight modification of this command:
ip summary-address eigrp 6000 0.0.0.0 0.0.0.0 254
The added number 254 represents the administrative distance of a summary route towards Null0 interface that EIGRP would automatically create on your primary and backup router and place into the routing table. Normally, such a route is used to prevent routing loops when performing summarization, but in your case, it could override the existing default route. By artificially increasing this AD to 254, we make sure that whatever default route is configured on your primary/backup router, it won't get overriden by this so-called discard route.
Ive got the other router as a neighbour on the same VLAN so will it affect traffic coming from that too?
If you are asking whether the summarization configured on one router will cause the other router to see only the summarized route then the answer is yes. A summarization configured on an interface will affect all neighbors reachable via that interface.
If this is not what you need to accomplish then an alternative way is to let the primary/backup routers advertise all networks in EIGRP including a default route, and use distribute lists on the switches to filter out all networks except the default route. This way, the switches would see just a default route while the primary/backup router would still exchange the full set of routes.
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2012 05:30 AM
Paul,
What kind of routers are these? Can you set up tracking on the router? The reason that I ask is because if you can create a track on the primary router, you can then watch your wan interface. When it fails, you can force hsrp to move to the other router. If you can't do it on the router either, I'm not sure you're going to be able to work around this problem.
HTH,
John
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2012 05:42 AM
Hi Paul,
I wonder... is there any common routing protocol supported by both your primary/backup routers and the switches, e.g. RIPv2 or OSPF for Routed Access? I am thinking of originating a default route on the WAN routers based on their own WAN connectivity. The switches would merely learn the default route originated accordingly.
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2012 07:07 AM
Peter,
I never even thought about that, and that's amazing . I tested this, and honestly after I configured it the solution seems very simple (if I'm thinking along the same lines you are). I configured ospf between the internal interfaces and set the primary with a default route pointing to the ISP. Then I advertised that default route into ospf and made sure the internal router had the route. On the internal router, I set a floating default route pointing to the other router. After shutting down the interface to the ISP, HSRP did NOT fail over (as expected), but my default route does change to the other router. Is that what you suggested? If so, that's just ingenious. +5 for you!
John
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2012 08:23 AM
Hi John,
Yes, I was thinking along the same lines as you. But in addition, with a little luck, the IP BASE on Paul's switches supports track ip route metric threshold command that allows us to track the presence and metric of a selected route. Assuming that the primary router issues the default route with significantly lower metric than the backup router, we could tie the metric value into the tracking object state, and depending on the tracking object state, change the HSRP Active role.
In short words: if the default route metric is low, it means that the originating router is the primary, thereby leaving the Active router in place. If the default route metric is high, it means that the originating router is the backup router, thereby making the track object go to Down state, lowering the HSRP priority and let the Standby router take over the Active role.
I am not sure if I am entirely clear on this but I hope you and Paul get the general idea.
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2012 09:38 AM
Yes sir that works too I labbed it up to see this work, and this was the first time I've used the 'metric threshold' option.
I have something like the following:
R1
/ \
R2---R3
R2 and R3 run hsrp with R2 being primary. I have a loopback on R1 addressed as 1.1.1.1. On R2, I configured:
track 1 ip route 1.1.1.1 255.255.255.255 metric threshold
threshold metric up 11 down 12
standby 1 track 1 decrement 10
Under the interface that hsrp is configured on R2, I configured "standby 1 track 1 dec 10".
Then I changed the cost on the loopback interface on R1 to be 15, and here's the result:
Track 1
IP route 1.1.1.1 255.255.255.255 metric threshold
Metric threshold is Down (OSPF/25/25)
2 changes, last change 00:03:45
Metric threshold down 12 up 11
First-hop interface is FastEthernet0/0
Tracked by:
HSRP FastEthernet0/1 1
Show standby
Priority 95 (configured 105)
Track object 1 state Down decrement 10
That's a very good thing to know! Thanks Peter!
John
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2012 10:28 AM
Hello John,
Thank you very much for your kind words and generous ratings!
You may be interested in reading the following guide:
The track ip route metric threshold uses a scaled metric, and it is important to know how the scaled metric is computed, as it is different for each routing protocol. The document above contains a table that shows the default scaling factors by which the metrics are divided to yield the scaled metric used in the track object configuration. These default scaling factors can be modified using the track resolution ip route command.
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2012 12:00 AM
Thanks both for your input.
Im going to try these things tonight after hours. The track metric threshold sounds promising. I saw it on the switch when ??ing through the track options but didnt know if it would help.
We use EIGRP on the routers but not all our LAN switches are Cisco or even L3.
Ill report back as soon as I have some results.
THanks again
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2012 05:47 AM
I am apprehensive about enabling full EIGRP routing on my internal LAN. Will this affect my spanning tree?
Can I enable EIGRP but not add network statements and just use a neighbor command to create the neighbourship?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2012 05:58 AM
Hi Paul,
I am apprehensive about enabling full EIGRP routing on my internal LAN. Will this affect my spanning tree?
Absolutely not. In fact, EIGRP running within a particular VLAN will always be constrained to the active topology determined by the spanning tree.
Can I enable EIGRP but not add network statements and just use a neighbor command to create the neighbourship?
No, that is not possible. Even if specifying static neighbors using the neighbor command, these neighbors must be directly reachable on interfaces that are included into EIGRP using appropriate network commands.
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2012 11:11 AM
Ok so the EIGRP got straight to it but this is a bad thing. I now have a switch with a hundred routes instead of just one default one.
Both routers also connect to 30 GRE tunnels externally to the rest of the company sites. So Ive a lot of other subnets besides the internal LAN.
How can I stop EIGRP advertising routes inwards other than the default route? ip summary-address eigrp 6000 0.0.0.0 0.0.0.0
Will that work? Ive got the other router as a neighbour on the same VLAN so will it affect traffic coming from that too?
many thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-11-2012 11:50 AM
Hi Paul,
How can I stop EIGRP advertising routes inwards other than the default route?
ip summary-address eigrp 6000 0.0.0.0 0.0.0.0
Yes, if this command is applied on the primary/backup router interfaces towards the switches, it will cause the EIGRP-advertised routes to be summarized to 0.0.0.0/0. However, I suggest a slight modification of this command:
ip summary-address eigrp 6000 0.0.0.0 0.0.0.0 254
The added number 254 represents the administrative distance of a summary route towards Null0 interface that EIGRP would automatically create on your primary and backup router and place into the routing table. Normally, such a route is used to prevent routing loops when performing summarization, but in your case, it could override the existing default route. By artificially increasing this AD to 254, we make sure that whatever default route is configured on your primary/backup router, it won't get overriden by this so-called discard route.
Ive got the other router as a neighbour on the same VLAN so will it affect traffic coming from that too?
If you are asking whether the summarization configured on one router will cause the other router to see only the summarized route then the answer is yes. A summarization configured on an interface will affect all neighbors reachable via that interface.
If this is not what you need to accomplish then an alternative way is to let the primary/backup routers advertise all networks in EIGRP including a default route, and use distribute lists on the switches to filter out all networks except the default route. This way, the switches would see just a default route while the primary/backup router would still exchange the full set of routes.
Best regards,
Peter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2012 05:19 AM
In the end, the only way to resolve this was to advertise a default route from Primary Router but to distribute-list block it from all but Switch1. This meant that if the outbound internet interface went down (ADSL drops), the route would be lost and the lower metric backup default route would be installed in the route table on Switch1. Since the failure of the interface also causes a tracked object controlling the HSRP failover on the Primary Router to trip, the overall effect is that both default routing and default-gateways move across the network.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
