- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Unable to ping other VLANS using ReMote Vpn
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2022 06:51 AM
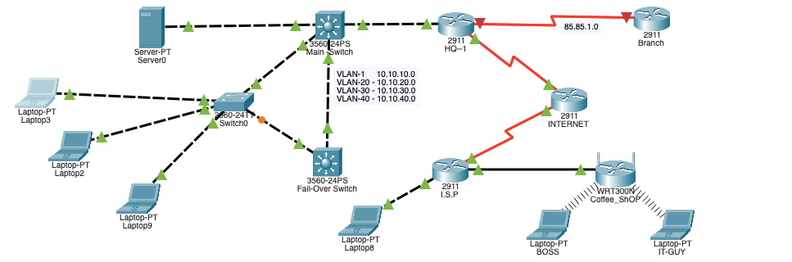
Hi Guys,
I have a a tricky problem with my network . I have both a wired and wireless connection going thru the ISP to HQ router. The VPN remote access connects fine but I cannot ping other VLANS except VLAN 1 (Native). I have configured static routes between my core and HQ router but i got no reply back other than timed out messages... Does anyone have an idea of how i can go about this. I'll appreciate any materials or explanations. Thank you
~Chike
Solved! Go to Solution.
- Labels:
-
Community Feedback Forum
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2022 03:57 AM
Hello,
the problem is simply that the VPN pool is part of the same address space you have configured for Vlan 20 on the switch. Change the pool to:
MSA-RT(config)#no ip local pool POOLVPN 10.10.20.50 10.10.20.60
MSA-RT(config)#ip local pool POOLVPN 10.10.50.50 10.10.50.60
Also, although that is a minor problem and not related to the VPN connectivity issue, your DHCP server dishes out the wrong default gateway for Vlan 1 (10.10.10.1 instead of 10.10.10.2).
Attached the revised file...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2022 05:05 AM
Hello,
the DHCP server handing out the wrong default gateway was the minor problem. Sorry for the misunderstanding. The local pool being part of a remote network (Vlan 20 on the remote switch) is a major problem and will not work. Basically, your VPN clients get IP addresses from an existing network that is not even local to the VPN router, but exists on a remote network. There is no way to route this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2022 04:34 PM - edited 12-12-2022 04:37 PM
Can you do a traceroute from a device on the VPN to one of the VLANs to see what path it is trying to take, and make sure that each device in the traceroute has the proper next hop configured to get it to the other VLANs, and has the proper next hop for th return route back to the VPN?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-12-2022 10:30 PM - edited 12-12-2022 11:47 PM
Thanks for hopping on this issue for me ... Yes i did a tracert but it seems to be going via it's serial interface of the ISP... which wows me. After the VPN connects is creates a static route automatically.. Pasting configs of each routes from HQ
==HQ VPN Router==
Gateway of last resort is 0.0.0.0 to network 0.0.0.0
10.0.0.0/8 is variably subnetted, 6 subnets, 2 masks
C 10.10.10.0/24 is directly connected, GigabitEthernet0/0
L 10.10.10.1/32 is directly connected, GigabitEthernet0/0
S 10.10.20.0/24 [1/0] via 10.10.10.2
S 10.10.20.51/32 [1/0] via 85.85.3.1 ==== THis the Static route left by the VPN connection from the coffee shop node clients and every other static routes points to the Vlans in my Core router which runs inter_Vlans using SVI's. it can only ping hosts on vlan 1-(10.10.10.0 network) which is native i understand that .... but not other VLANS despite having static routes configured. It says timed out every-time.
S 10.10.30.0/24 [1/0] via 10.10.10.2
S 10.10.40.0/24 [1/0] via 10.10.10.2
85.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 85.85.2.0/30 is directly connected, Serial0/0/0
L 85.85.2.1/32 is directly connected, Serial0/0/0
S* 0.0.0.0/0 is directly connected, Serial0/0/0
=== INTERNET ROUTER=== Route Table
Gateway of last resort is not set
85.0.0.0/8 is variably subnetted, 4 subnets, 2 masks
C 85.85.2.0/30 is directly connected, Serial0/0/1
L 85.85.2.2/32 is directly connected, Serial0/0/1
C 85.85.3.0/30 is directly connected, Serial0/0/0
L 85.85.3.2/32 is directly connected, Serial0/0/0
=ISP ROUTER= Route Table
Gateway of last resort is 0.0.0.0 to network 0.0.0.0
20.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 20.20.20.0/30 is directly connected, GigabitEthernet0/0
L 20.20.20.1/32 is directly connected, GigabitEthernet0/0
85.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 85.85.3.0/30 is directly connected, Serial0/0/0
L 85.85.3.1/32 is directly connected, Serial0/0/0 === This is the automatic static route for the Remote Access VPN Connection on the HQ VPN router after the VPN connects. I have tried to define so many tactics using dynamic and static routing it refused to communicate with rest of VLANS in the network except Vlan 1.. I can't delete the VPN static route either another issue for me.
192.168.5.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.5.0/30 is directly connected, GigabitEthernet0/1
L 192.168.5.1/32 is directly connected, GigabitEthernet0/1
S* 0.0.0.0/0 is directly connected, Serial0/0/0
I attached the topology on this issue and I'll appreciate any ideas you got this issue. I await your response .
~Chike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2022 12:56 AM - edited 12-13-2022 12:59 AM
You say: "Yes i did a tracert but it seems to be going via it's serial interface of the ISP... "
This means client traffic is being sent to the ISP router in order to reach the other VLANs.
Make sure that the clients are not doing any split tunneling where they route internet traffic to the ISP router when the VPN is connected without properly sending all the needed LAN routes to the VPN client upon connection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2022 01:27 AM - edited 12-13-2022 01:29 AM
Thanks for writing back ... No split tunneling ... just full tunneling encrypting all traffic from the coffee shop nodes into the HQ LAN network which is also hosting the VPN connection ... After it receives an IP address from VLan 20 pool of IP addresses it just creates static routes going via the ISP serial interface. I don't know what else to do or am i to conclude that on the CCNA level we can only do Remote Access VPN for just the native VLAN-1 cos i'm reading somewhere that it is possible with Generic Routing Encapsulation (GRE).. which is in the new CCNP series. You can run the configs on PT to get better understanding of what i'm referring to. Let me know what you think.
~Chike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2022 03:57 AM
Hello,
the problem is simply that the VPN pool is part of the same address space you have configured for Vlan 20 on the switch. Change the pool to:
MSA-RT(config)#no ip local pool POOLVPN 10.10.20.50 10.10.20.60
MSA-RT(config)#ip local pool POOLVPN 10.10.50.50 10.10.50.60
Also, although that is a minor problem and not related to the VPN connectivity issue, your DHCP server dishes out the wrong default gateway for Vlan 1 (10.10.10.1 instead of 10.10.10.2).
Attached the revised file...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2022 04:51 AM
OMG!!! George You are a lifesaver my man. Thank you for pointing out my mistake I did not ever imagine my DHCP was handling out wrong gateway address to vlan 1 because (10.10.10.1) is the HQ-Router Gateway interface. Thank you so much you have made my day now I can continue my design to scale my LAN network into Voip, Wifi connections using aaa authentication.
Please George one more question : Are you saying that I can't hand out POOL of ip addresses from my VLAN 20 to the VPN clients to be part of my internal LAN HQ network? Because you said it was a minor problem i just wanted to know if it is a good practice to do so.
Many thanks,
~Chike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2022 05:05 AM
Hello,
the DHCP server handing out the wrong default gateway was the minor problem. Sorry for the misunderstanding. The local pool being part of a remote network (Vlan 20 on the remote switch) is a major problem and will not work. Basically, your VPN clients get IP addresses from an existing network that is not even local to the VPN router, but exists on a remote network. There is no way to route this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2022 05:23 AM
Thank you for taking your time clarifying this to me. Keep doing helping as much as you can man ... You won yourself a fan.
Blessings
~Chike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2022 08:04 AM - edited 12-13-2022 11:52 AM
Ok.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
