- Cisco Community
- Technology and Support
- Networking
- Switching
- use acl to limit traffic between vlans
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2011 07:21 AM - edited 03-07-2019 03:29 AM
hi:
i am back with another question.
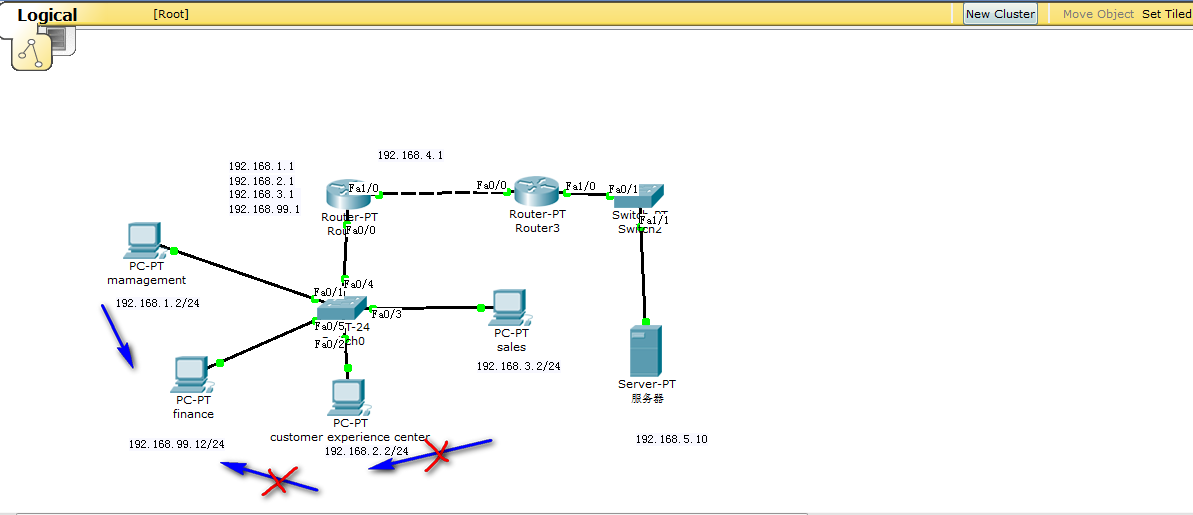
above is the scenario,
the IP addresses of 4 PCs were assigned by DHCP.
and each PC represent a vlan .
question :
how to block all incoming traffic to 192.168.99.0/24 except from 192.168.1.0/24 .
ip dhcp excluded-address 192.168.1.1 192.168.1.10
ip dhcp excluded-address 192.168.2.1 182.168.2.10
ip dhcp excluded-address 192.168.3.1 192.168.3.10
ip dhcp excluded-address 192.168.99.1 192.168.99.10
!
ip dhcp pool managment
network 192.168.1.0 255.255.255.0
default-router 192.168.1.1
ip dhcp pool finance
network 192.168.99.0 255.255.255.0
default-router 192.168.99.1
ip dhcp pool sales
network 192.168.3.0 255.255.255.0
default-router 192.168.3.1
ip dhcp pool customer_exp
network 192.168.2.0 255.255.255.0
default-router 192.168.2.1
interface FastEthernet0/0
no ip address
duplex auto
speed auto
!
interface FastEthernet0/0.1
encapsulation dot1Q 10
ip address 192.168.1.1 255.255.255.0
!
interface FastEthernet0/0.2
encapsulation dot1Q 20
ip address 192.168.2.1 255.255.255.0
!
interface FastEthernet0/0.3
encapsulation dot1Q 30
ip address 192.168.3.1 255.255.255.0
!
interface FastEthernet0/0.10
encapsulation dot1Q 99
ip address 192.168.99.1 255.255.255.0
ip access-group 1 in
!
interface FastEthernet1/0
ip address 192.168.4.1 255.255.255.0
duplex auto
speed auto
router eigrp 10
network 0.0.0.0
auto-summary
!
ip classless
!
!
access-list 1 permit host 192.168.1.0 // i think here i permited traffic of 192.168.1.0
the above configuration is missing something, because if i applied it, the 192.168.99.0 network rejected all kind of traffic including DHCP.
I think use standard ACL is enough but i am not so sure. i also tried to use extended ACL but it did not work as well.
please help.
thanks in advance
dannan
Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2011 01:40 AM
Hi Dannan,
You stand on the router and you see packets coming to you from the 99.0 network(source), so you have to apply acl to check the packets coming to you, so you have to apply as "in" to check the incoming packets.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2011 05:04 AM
Hi Dannan,
my question is why i must put "in" here instead of "out"
The above ip access-group "in" or "out" both will do different job.
The difference in applying an ACL in or out is like this....
When you apply an ACL "in", the router examines all traffic it RECEIVES on the interface against the ACL.
When you apply an ACL "out" on an interface the router examines any traffic attempting to leave that interface against the ACL.
Hope I clear you...
Please rate the helpfull posts.
Regards,
Naidu.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2011 07:57 AM
Try this and test again:
access-list 111 permit ip 192.168.1.0 0.0.0.255 192.168.99.0 0.0.0.255
access-list 111 deny ip any any
interface FastEthernet0/0.10
encapsulation dot1Q 99
ip address 192.168.99.1 255.255.255.0
ip access-group 111 in
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2011 08:09 AM
thanks Reza,
but it did not work
access-list 111 permit ip 192.168.1.0 0.0.0.255 192.168.99.0 0.0.0.255
access-list 111 deny ip any any
it rejected DHCP service as well.
any thoughts???
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2011 08:14 AM
how about first deny all the other subnets
access-list 111 deny ip 192.168.2.0 0.0.0.255 192.168.99.0 0.0.0.255
access-list 111 deny ip 192.168.3.0 0.0.0.255 192.168.99.0 0.0.0.255
access-list 111 deny ip 192.168.5.0 0.0.0.255 192.168.99.0 0.0.0.255
access-list 111 deny ip 192.168.12.0 0.0.0.255 192.168.99.0 0.0.0.255
then permit all
access-list 111 permit ip any any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2011 08:35 AM
ummm, i didn't deny all sunbets but
i did one
access-list 111 deny ip 192.168.2.0 0.0.0.255 192.168.99.0 0.0.0.255
and permited all
this time dhcp worked but 192.168.2.0 networkt can still ping 192.168.99.0 network.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2011 09:00 AM
i figured out
if i use
access-list 101 permit udp any any eq bootps
i can keep the dhcp running
but i still don't know how to deny other pc access to 192.168.99.0 network .
i used
access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.99.0 0.0.0.255
but it blocked all access to 192.168.99.0 which is not i wanted.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2011 09:03 AM
dannan lin wrote:
i figured out
if i use
access-list 101 permit udp any any eq bootps
i can keep the dhcp running
but i still don't know how to deny other pc access to 192.168.99.0 network .
i used
access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.99.0 0.0.0.255
but it blocked all access to 192.168.99.0 which is not i wanted.
For this, you should try this
access-list 101 permit ip 192.168.99.0 0.0.0.255 192.168.1.0 0.0.0.255
access-list 101 permit udp any eq bootpc any
Message was edited by: Manjunath Shivanna
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2011 09:01 AM
Hi,
dannan lin wrote:
ummm, i didn't deny all sunbets but
i did one
access-list 111 deny ip 192.168.2.0 0.0.0.255 192.168.99.0 0.0.0.255
and permited all
this time dhcp worked but 192.168.2.0 networkt can still ping 192.168.99.0 network.
It should be the other way,
try
access-list 111 deny ip 192.168.99.0 0.0.0.255 192.168.2.0 0.0.0.255
and permit all
Message was edited by: Manjunath Shivanna
Corrected the ip subnet, sorry for typo.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2011 06:48 PM
thank you manju,
but i got another stupid question to ask .
as you suggested
i put
Extended IP access list 101
permit ip 192.168.99.0 0.0.0.255 192.168.1.0 0.0.0.255 (3 match(es))
permit udp any eq bootpc any
permit ip 192.168.99.0 0.0.0.255 host 192.168.5.10 (13 match(es)) // i added extra statement to allow traffic to the server
and
interface FastEthernet0/0.10
encapsulation dot1Q 99
ip address 192.168.99.1 255.255.255.0
ip access-group 101 in // the "out" option didn't work
my question is why i must put "in" here instead of "out"
according to the statement
permit ip 192.168.99.0 0.0.0.255 192.168.1.0 0.0.0.255
192.168.99.0 is the source network and 192.168.1.0 is the destination network and we are configuring at int f0/0.10
which ip address is 192.168.99.1 .
from 192.168.99.0 to 192.168.1.0 looks like "out"relationship to me .
(192.168.99.0) -> (192.168.1.0)
???? i am a little confused here.
thanks to your help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2011 01:40 AM
Hi Dannan,
You stand on the router and you see packets coming to you from the 99.0 network(source), so you have to apply acl to check the packets coming to you, so you have to apply as "in" to check the incoming packets.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2011 05:04 AM
Hi Dannan,
my question is why i must put "in" here instead of "out"
The above ip access-group "in" or "out" both will do different job.
The difference in applying an ACL in or out is like this....
When you apply an ACL "in", the router examines all traffic it RECEIVES on the interface against the ACL.
When you apply an ACL "out" on an interface the router examines any traffic attempting to leave that interface against the ACL.
Hope I clear you...
Please rate the helpfull posts.
Regards,
Naidu.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2011 05:17 AM
thanks guys, you are internet heros.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide