- Cisco Community
- Technology and Support
- Collaboration
- TelePresence and Video Infrastructure
- The TLS verify subject name
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
"Peer's TLS certificate identity was unacceptable" issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2016 10:03 AM - edited 03-18-2019 06:15 AM
Hello,
i try to configure mobile remote access on expressway E.
The problem is that, when i create "Unified Communications traversal" zone for Expressway E and C i got this error on expressway E. This is expressway E event Log.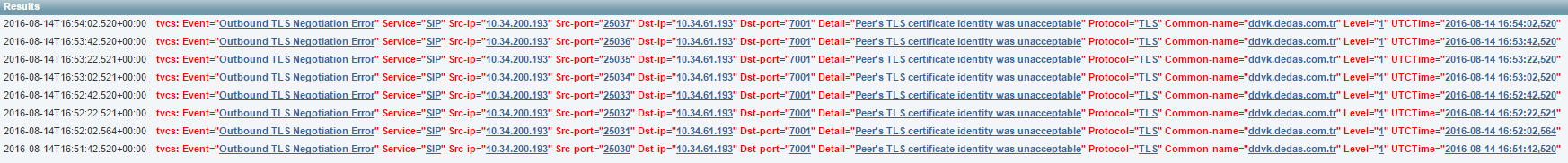
If you cant see:
| 2016-08-14T16:54:02.520+00:00 | tvcs: Event="Outbound TLS Negotiation Error" Service="SIP" Src-ip="10.34.200.193" Src-port="25037" Dst-ip="10.34.61.193" Dst-port="7001" Detail="Peer's TLS certificate identity was unacceptable" Protocol="TLS" Common-name="ddvk.dedas.com.tr" Level="1" UTCTime="2016-08-14 16:54:02,520" |
ı uploaded certificates each other. ı think it is work. because they have active traversal zone (traversal client and traversal server) each other with TLS.
I try to write also ip address of expressway e as a common name insteady of "ddvk.dedas.com.tr". i got this error also.
how can i solve this problem?
- Labels:
-
Room Endpoints
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2016 02:30 PM
Did you configure the certificates per the Mobile and Remote Access via Cisco Expressway Deployment Guide (X8.8), refer to the "Unified Communications Prerequisites" on pg 19.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2016 03:00 PM
The certificates that i uploaded are self-signed. I guess it must be CA certificate. But ı dont now how to generate CA certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2016 03:10 PM
The TLS verify subject name configured in the UC traversal zone on Expressway E must match the Common Name or the SAN of the Expressway-C certificate. Make sure there isn't any difference between the two (like a small typo).
Besides, the Exp-E needs to have the root certificate of the CA that signed the certificate of Exp-C in its trusted CA certificates (and the other way around too, of course).
Expressway certificates must have Server and Client Extended Key Usage
And as of X8.8 forward AND reverse DNS lookups must be valid and working (i.e. Expressway-C looking up the IP of Expressway-E should receive it's correct hostname matching its certificate.
a complete guide on certificates for Expressways is here:
http://www.cisco.com/c/dam/en/us/td/docs/voice_ip_comm/expressway/config_guide/X8-8/Cisco-Expressway-Certificate-Creation-and-Use-Deployment-Guide-X8-8.pdf
Cheers,
Zoltan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2016 03:17 PM
Dns lookup is working.
Between two expressways has travelzone with TLS and it is working. that means certificates that i uploaded each other are working. Rght?
So, how is it possible when i try to configure "unifed communication travel zone" i got certificate error message?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2016 03:30 PM
Even if the zone may show "active" I wouldn't be quite so sure that it is working if you are seeing this error.
On Expressway-C go to Maintenance > Security Certificates > Secure traversal test and fill in the exp-e fqdn as well as the exp-c fqdn.
Does that work as expected?
How did you generate the "self signed" certificates, as Expressways do not have a GUI for that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2016 03:41 PM
In secure traversal test, it couldnt verify fqdn of expressway c or c. But i uploaded as a trusted certificate. i am sure that fqdn names are correct in certificates.
I generated self-signed with using openssl.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2016 04:05 PM
Just to clarify some concepts:
- self-signed certificate: the issuer of the certificate is equal to the subject of the certificate.
- CA signed certificate: the issuer is different than the subject
- Public CA signed certificate: as above, but the issuer is a well known authority with it's root certificates shipped with most OSes, devices etc.
Whoever the issuer is, it's certificate must be in the trusted certificates store on the remote party. So with self-signed certificates, the certificate of source must be in the trusted store of destination. Since Expressways are doing mutual TLS, this must be true both ways.
If the certificate issuer in your certificates does not match the subject, the issuer's root certificate must be installed as a trusted CA certificate on both expressways.
MRA has a number of requirements for certificates as I mentioned before:
- they must be both Web Client and Web Server certificates
- they must contain the fqdn as CN or SAN
- the exp-e certificate must contain the domain among its SANs
- also, key length should be less than 4096
- etc (the rest were probably already met as you were able to upload the certificates to begin with)
On Expressway-C, the UC traversal zone's peer address must be an FQDN, must match the subject (CN or SAN) of the Exp-E certificate and must resolve to the internal LAN IP in Dual NIC or public IP in single NIC mode of Expressway-E.
On Expressway-E the TLS subject verify name in the UC traversal zone must match the subject (CN or SAN) of the Expressway-C certificate.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide