- Cisco Community
- Technology and Support
- Collaboration
- Unified Communications Infrastructure
- CSCwa25099, CSCwa25100 and CSCwa25074 - Expressway Cross-Site Vulnerab
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
CSCwa25099, CSCwa25100 and CSCwa25074 - Expressway Cross-Site Vulnerab
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2024 10:05 AM
Hello,
the Cisco Security Advisory raised yesterday relates to bugs CSCwa25099, CSCwa25100 and CSCwa25074:
and basically mention: "This vulnerability is due to insufficient CSRF protections for the web-based management interface of an affected system."
and also mention that there is no workaround, must upgrade to a fixed release.
If the bug is specific to the web-based management, I was wondering we disable web access to the expressway, either by block with internal or external firewall or directly disabling web mgmt interface, would be enough to not be exposed, while planning the upgrade to a fixed release.
Any thoughts?
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2024 10:51 AM
You need to use the GUI to configure everything. If you block it, you won't be able to manage Expressway.
You should upgrade to the fixed release. Running a version with vulnerabilities and applying unofficial fixes that Cisco doesn't mention in the BUG ID is risky.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-08-2024 12:05 PM
We understand that the web is needed, but If this bug affect the web-management only, to block the access to the web o directly disable it could allow the customer a few more days to deploy a new version. The alternative is to shut down the cluster to do not be exposed and disrupt the service.
Take into account that the customer may have a previous version due to some specific reason, that may be unsupported HW, unsupported VMware version, compatibility with other machines, integrations, etc that may slowdown the upgrade.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2024 01:00 AM
When we face controversial information it generates some concerns and distrust...
In one hand, the advisory and bugs mentions that the problem affects web-management interface only and reading how a CSRF works and the related CWE-352 that states: "An attacker could effectively perform any operations as the victim. If the victim is an administrator or privileged user, the consequences may include obtaining complete control over the web application... Because the attacker has the identity of the victim, the scope of CSRF is limited only by the victim's privileges", it lead us to interpret that the device used to access the Expressway web-management is the one that must be compromised and that it is related with logins and its privileges.
By the other hand, the information received confirms that it affects the web-management interface only but also says that the vulnerability affects the entire system and anyone with network access to the Expressway could exploit this vulnerability.
There are thousands of Expressways running on HW/hosts that cannot be quickly upgraded to the fixed releases and I think that an advisory with that magnitud should be better written and detailed.
Best Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2024 09:40 AM
Does it affect Exp Version 14.0.7 ? The bug says the affected version is 14.0.3 ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2024 10:15 AM
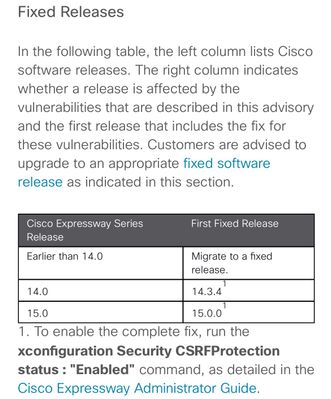
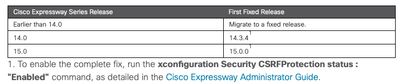
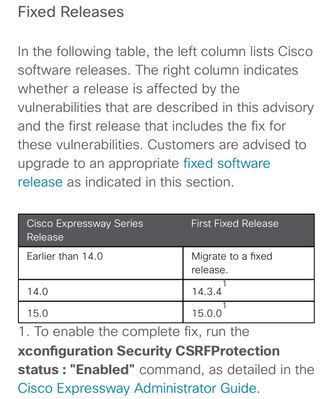
It say clearly that any version prior to 14.0 and including any 14.0 is affected. You need to be on 14.3.4 or 15.0.0 to not be affected.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2024 06:01 AM
We are running release 14.3.3. Do we need to upgrade to 14.3.4 or are we good since it says effects 14.0 and earlier?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2024 08:24 AM
Fixed release is X14.3.4. So every things else / lower than this version is affected.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-12-2024 11:25 AM
How hard can this be. Did you even read the previous answer before you asked?

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2024 01:31 AM
The release note explicitly indicates version 14.3.4, and if you are currently on 14.3.3, you are indeed affected and should upgrade to the fixed versions, which is 14.3.4

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2024 11:49 PM
hello @Nithin Eluvathingal ,Does this bug affect MRA calls? Or internal calls on EXP?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2024 12:30 AM - edited 02-16-2024 12:59 AM
The defect is not related to any specific service that runs on Expressway, it affects the whole Expressway. So anything on Expressway below the mentioned fixed versions, ie x14.3.4 and x15.0.0, are affected, regardless what services the Expressway provides.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2024 06:59 AM
Hi Team,
If my system Expressway C y E have an version Earlier than 14.X, Does vulnerability also apply?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2024 07:31 AM
According to the advisory: YES
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-09-2024 07:49 AM - edited 02-09-2024 11:19 PM
Yes. You need to be on 14.3.4 or 15.0.0 to not be affected.

Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide