- Cisco Community
- Technology and Support
- Data Center and Cloud
- Unified Computing System (UCS)
- Unified Computing System Discussions
- Re: Modify Certificate Request Properties
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2023 12:04 PM
Good afternoon,
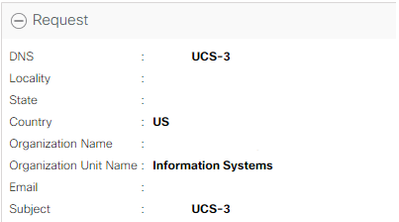
Is there a way to modify the properties of the keyring certificate request? Our certificate has expired and when I go to import a new one, I noticed that the DNS and Subject fields are the same. I went ahead and tried to import the new cert that was generated from our CA, but I get an error saying that the two fields are the same and to modify either one and retry.
Solved! Go to Solution.
- Labels:
-
UCS Manager
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2023 07:30 AM
So, after discussing this with a Cisco technician via Service Request, I was told that there is a bug with the version that we're running, 4.2(2d), that was preventing me from modifying the certificate request. What I did as a workaround was to delete the certificate request, not the keyring, and create a new request. Once I did that, I was able use the new certificate request to create a new certificate and upload it. Within a few minutes it was showing to be valid.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2023 12:44 PM
Creating a Certificate Request for a Key Ring with Advanced Options
Procedure
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
UCS-A# scope security |
Enters security mode. |
| Step 2 |
UCS-A /security # scope keyring keyring-name |
Enters configuration mode for the key ring. |
| Step 3 |
UCS-A /security/keyring # create certreq |
Creates a certificate request. |
| Step 4 |
UCS-A /security/keyring/certreq* # set country country name |
Specifies the country code of the country in which the company resides. |
| Step 5 |
UCS-A /security/keyring/certreq* # set dns DNS Name |
Specifies the Domain Name Server (DNS) address associated with the request. |
| Step 6 |
UCS-A /security/keyring/certreq* # set e-mail E-mail name |
Specifies the email address associated with the certificate request. |
| Step 7 |
UCS-A /security/keyring/certreq* # set ip certificate request ip-address | ipv6 certificate request ipv6-address |
Specifies the IPv4 or IPv6 address of the Cisco UCS domain. |
| Step 8 |
UCS-A /security/keyring/certreq* # set fi-a-ip certificate request FI A ip-address | fi-a-ipv6 certificate request FI A ipv6-address |
The IPv4 or IPv6 address of fabric interconnect A. |
| Step 9 |
UCS-A /security/keyring/certreq* # set fi-b-ip certificate request FI B ip-address | fi-b-ipv6 certificate request FI B ipv6-address |
The IPv4 or IPv6 address of fabric interconnect B. |
| Step 10 |
UCS-A /security/keyring/certreq* # set locality locality name (eg, city) |
Specifies the city or town in which the company requesting the certificate is headquartered. |
| Step 11 |
UCS-A /security/keyring/certreq* # set org-name organization name |
Specifies the organization requesting the certificate. |
| Step 12 |
UCS-A /security/keyring/certreq* # set org-unit-name organizational unit name |
Specifies the organizational unit. |
| Step 13 |
UCS-A /security/keyring/certreq* # set password certificate request password |
Specifies an optional password for the certificate request. |
| Step 14 |
UCS-A /security/keyring/certreq* # set state state, province or county |
Specifies the state or province in which the company requesting the certificate is headquartered. |
| Step 15 |
UCS-A /security/keyring/certreq* # set subject-name certificate request name |
Specifies the fully qualified domain name of the Fabric Interconnect. |
| Step 16 |
UCS-A /security/keyring/certreq* # commit-buffer |
Commits the transaction. |
| Step 17 |
UCS-A /security/keyring # show certreq |
Displays the certificate request, which you can copy and send to a trust anchor or certificate authority. |
Example
The following example creates and displays a certificate request with an IPv4 address for a key ring, with advanced options:
UCS-A# scope security
UCS-A /security # scope keyring kr220
UCS-A /security/keyring # create certreq
UCS-A /security/keyring/certreq* # set ip 192.168.200.123
UCS-A /security/keyring/certreq* # set fi-a-ip 192.168.200.124
UCS-A /security/keyring/certreq* # set fi-b-ip 192.168.200.125
UCS-A /security/keyring/certreq* # set subject-name sjc04
UCS-A /security/keyring/certreq* # set country US
UCS-A /security/keyring/certreq* # set dns bg1-samc-15A
UCS-A /security/keyring/certreq* # set e-mail test@cisco.com
UCS-A /security/keyring/certreq* # set locality new york city
UCS-A /security/keyring/certreq* # set org-name "Cisco Systems"
UCS-A /security/keyring/certreq* # set org-unit-name Testing
UCS-A /security/keyring/certreq* # set state new york
UCS-A /security/keyring/certreq* # commit-buffer
UCS-A /security/keyring/certreq # show certreq
Certificate request subject name: sjc04
Certificate request ip address: 192.168.200.123
Certificate request FI A ip address: 192.168.200.124
Certificate request FI B ip address: 192.168.200.125
Certificate request e-mail name: test@cisco.com
Certificate request ipv6 address: ::
Certificate request FI A ipv6 address: ::
Certificate request FI B ipv6 address: ::
Certificate request country name: US
State, province or county (full name): New York
Locality name (eg, city): new york city
Organization name (eg, company): Cisco
Organization Unit name (eg, section): Testing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2023 11:09 AM
Thank you for the reply and information. I have already looked at this before creating this discussion. I just wanted to know if it was possible to edit the existing request instead of creating a new one. When I try to import a new certificate using the existing request an error pops up saying that I can modify either the dns value or subject value and retry.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-23-2023 07:30 AM
So, after discussing this with a Cisco technician via Service Request, I was told that there is a bug with the version that we're running, 4.2(2d), that was preventing me from modifying the certificate request. What I did as a workaround was to delete the certificate request, not the keyring, and create a new request. Once I did that, I was able use the new certificate request to create a new certificate and upload it. Within a few minutes it was showing to be valid.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide