- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2020 08:23 AM
Hello,
we recently bought new VPN-Servers (Firepower 1140, 1150) to replace our older ASA 5540 servers.
We exported and imported the configuration via ASDM.
Because of the Coronavirus we did not wanted to started from scratch and get the server running fast.
In general this worked and Windows-Servers can log into the server via AnyConnect 4.7.
But when we try to connect via Android or iOS (AnyConnect 4.8) we get the following error after entering our credentials and accepting the welcome banner.
"Der sichere Gateway hat den Verbindungsversuch zurückgewiesen. Es ist ein neuer Verbindungsversuch mit dem gleichen oder einem anderen sicheren Gateway notwendig. Dieser erfordert die erneute Authentifizierung. Die folgende Nachricht wurde vom sicheren Gateway empfangen: Other error"
my translation: "The secure gateway rejected the connection attempt. [..] The following message wa received from the secure gateway: Other error"
Of cause "other error" does not lead to any usefull information when googleing.
We also took another new device and configured it step by step like the old server.
Here is the syslog-debug from the server: (anonymized username and ip addresses)
10:19:18 UTC: %ASA-svc-4-722041: TunnelGroup <DefaultWEBVPNGroup> GroupPolicy <DfltGrpPolicy> User <userABC> IP <1.2.3.192> No IPv6 address available for SVC connection
10:19:18 UTC: %ASA-svc-5-722033: Group <DfltGrpPolicy> User <userABC> IP <1.2.3.192> First TCP SVC connection established for SVC session.
10:19:18 UTC: %ASA-svc-4-722051: Group <DfltGrpPolicy> User <userABC> IP <1.2.3.192> IPv4 Address <1.2.1.215> IPv6 address <::> assigned to session
10:19:23 UTC: %ASA-svc-5-722033: Group <DfltGrpPolicy> User <userABC> IP <1.2.3.192> First UDP SVC connection established for SVC session.
10:21:32 UTC: %ASA-svc-4-722037: Group <DfltGrpPolicy> User <userABC> IP <1.2.3.192> SVC closing connection: Transport closing.
10:21:32 UTC: %ASA-svc-5-722012: Group <DfltGrpPolicy> User <userABC> IP <1.2.3.192> SVC Message: 16/NOTICE: The user has requested to disconnect the connection..
10:21:32 UTC: %ASA-auth-4-113019: Group = DefaultWEBVPNGroup, Username = userABC, IP = 1.2.3.192, Session disconnected. Session Type: SSL, Duration: 0h:02m:16s, Bytes xmt: 19935, Bytes rcv: 262195, Reason: User Requested
11:15:19 UTC: %ASA-auth-4-113019: Group = DefaultWEBVPNGroup, Username = userABC, IP = 1.2.3.192, Session disconnected. Session Type: SSL, Duration: 0h:30m:32s, Bytes xmt: 4351588, Bytes rcv: 339289, Reason: Idle Timeout
12:33:20 UTC: %ASA-svc-4-722003: IP <1.2.3.4> Error authenticating SVC connect request.
13:03:44 UTC: %ASA-auth-4-113019: Group = DefaultWEBVPNGroup, Username = userABC, IP = 1.2.3.4, Session disconnected. Session Type: AnyConnect-Parent, Duration: 0h:30m:27s, Bytes xmt: 3087, Bytes rcv: 201, Reason: Idle Timeout
14:51:55 UTC: %ASA-svc-4-722003: IP <1.2.3.4> Error authenticating SVC connect request.
15:01:18 UTC: %ASA-session-7-609001: Built local-host redundant:1.2.3.4
15:01:18 UTC: %ASA-session-6-302013: Built inbound TCP connection 77687 for redundant:1.2.3.4/35454 (1.2.3.4/35454) to identity:1.2.0.5/443 (1.2.0.5/443)
15:01:18 UTC: %ASA-ssl-6-725001: Starting SSL handshake with client redundant:1.2.3.4/35454 to 1.2.0.5/443 for TLS session
15:01:18 UTC: %ASA-ssl-7-725008: SSL client redundant:1.2.3.4/35454 to 1.2.0.5/443 proposes the following 21 cipher(s)
15:01:18 UTC: %ASA-ssl-7-725012: Device chooses cipher ECDHE-RSA-AES256-GCM-SHA384 for the SSL session with client redundant:1.2.3.4/35454 to 1.2.0.5/443
15:01:18 UTC: %ASA-ssl-6-725016: Device selects trust-point vpn for client redundant:1.2.3.4/35454 to 1.2.0.5/443
15:01:19 UTC: %ASA-ssl-6-725002: Device completed SSL handshake with client redundant:1.2.3.4/35454 to 1.2.0.5/443 for TLSv1.2 session
15:01:24 UTC: %ASA-auth-6-113004: AAA user authentication Successful : server = 1.2.1.32 : user = userABC
15:01:24 UTC: %ASA-webvpn-6-716002: Group <DfltGrpPolicy> User <userABC> IP <1.2.3.4> WebVPN session terminated: Connection Preempted.
15:01:24 UTC: %ASA-auth-6-113009: AAA retrieved default group policy (DfltGrpPolicy) for user = userABC
15:01:24 UTC: %ASA-auth-4-113019: Group = DefaultWEBVPNGroup, Username = userABC, IP = 1.2.3.4, Session disconnected. Session Type: AnyConnect-Parent, Duration: 0h:09m:31s, Bytes xmt: 52, Bytes rcv: 0, Reason: Connection Preempte
15:01:24 UTC: %ASA-auth-6-113008: AAA transaction status ACCEPT : user = userABC
15:01:24 UTC: %ASA-dap-7-734003: DAP: User userABC, Addr 1.2.3.4: Session Attribute aaa.radius["6"]["1"] = 2
15:01:24 UTC: %ASA-dap-7-734003: DAP: User userABC, Addr 1.2.3.4: Session Attribute aaa.radius["18"]["1"] = (User found in PAP)
15:01:24 UTC: %ASA-dap-7-734003: DAP: User userABC, Addr 1.2.3.4: Session Attribute aaa.radius["8"]["1"] = 2332426711
15:01:24 UTC: %ASA-dap-7-734003: DAP: User userABC, Addr 1.2.3.4: Session Attribute aaa.cisco.grouppolicy = DfltGrpPolicy
15:01:24 UTC: %ASA-dap-7-734003: DAP: User userABC, Addr 1.2.3.4: Session Attribute aaa.cisco.ipaddress = 1.2.1.215
15:01:24 UTC: %ASA-dap-7-734003: DAP: User userABC, Addr 1.2.3.4: Session Attribute aaa.cisco.username = userABC
15:01:24 UTC: %ASA-dap-7-734003: DAP: User userABC, Addr 1.2.3.4: Session Attribute aaa.cisco.username1 = userABC
15:01:24 UTC: %ASA-dap-7-734003: DAP: User userABC, Addr 1.2.3.4: Session Attribute aaa.cisco.username2 =
15:01:24 UTC: %ASA-dap-7-734003: DAP: User userABC, Addr 1.2.3.4: Session Attribute aaa.cisco.tunnelgroup = DefaultWEBVPNGroup
15:01:24 UTC: %ASA-dap-6-734001: DAP: User userABC, Addr 1.2.3.4, Connection AnyConnect: The following DAP records were selected for this connection: DfltAccessPolicy
15:01:24 UTC: %ASA-auth-6-113039: Group <DfltGrpPolicy> User <userABC> IP <1.2.3.4> AnyConnect parent session started.
15:01:24 UTC: %ASA-ssl-6-725016: Device selects trust-point vpn for client redundant:1.2.3.4/35454 to 1.2.0.5/443
15:01:25 UTC: %ASA-session-6-302013: Built inbound TCP connection 77689 for redundant:1.2.3.4/35456 (1.2.3.4/35456) to identity:1.2.0.5/443 (1.2.0.5/443)
15:01:25 UTC: %ASA-ssl-6-725001: Starting SSL handshake with client redundant:1.2.3.4/35456 to 1.2.0.5/443 for TLS session
15:01:25 UTC: %ASA-ssl-7-725008: SSL client redundant:1.2.3.4/35456 to 1.2.0.5/443 proposes the following 21 cipher(s)
15:01:25 UTC: %ASA-ssl-7-725012: Device chooses cipher ECDHE-RSA-AES256-GCM-SHA384 for the SSL session with client redundant:1.2.3.4/35456 to 1.2.0.5/443
15:01:25 UTC: %ASA-ssl-6-725016: Device selects trust-point vpn for client redundant:1.2.3.4/35456 to 1.2.0.5/443
15:01:26 UTC: %ASA-ssl-6-725002: Device completed SSL handshake with client redundant:1.2.3.4/35456 to 1.2.0.5/443 for TLSv1.2 session
15:01:26 UTC: %ASA-svc-4-722003: IP <1.2.3.4> Error authenticating SVC connect request.
15:01:26 UTC: %ASA-ssl-6-725007: SSL session with client redundant:1.2.3.4/35456 to 1.2.0.5/443 terminated
15:01:26 UTC: %ASA-session-6-302014: Teardown TCP connection 77689 for redundant:1.2.3.4/35456 to identity:1.2.0.5/443 duration 0:00:00 bytes 6843 TCP Reset-O from identity
15:01:26 UTC: %ASA-session-6-106015: Deny TCP (no connection) from 1.2.3.4/35456 to 1.2.0.5/443 flags FIN ACK on interface redundant
15:01:26 UTC: %ASA-session-7-710005: TCP request discarded from 1.2.3.4/35456 to redundant:1.2.0.5/443
15:01:26 UTC: %ASA-ssl-6-725007: SSL session with client redundant:1.2.3.4/35454 to 1.2.0.5/443 terminated
15:01:26 UTC: %ASA-session-6-302014: Teardown TCP connection 77687 for redundant:1.2.3.4/35454 to identity:1.2.0.5/443 duration 0:00:07 bytes 9642 TCP FINs from identity
15:01:26 UTC: %ASA-session-7-609002: Teardown local-host redundant:1.2.3.4 duration 0:00:07
Only the following line looks relevant, but does not offer much.
15:01:26 UTC: %ASA-svc-4-722003: IP <1.2.3.4> Error authenticating SVC connect request.
We also took another new device and configured it step by step like the old server.
Any idea what is causing this issue?
AnyConnect 2.x (i think) is working on an older iPad from my colleague.
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2020 12:41 PM
I checked within ASDM to update the Software and it returned "up to date".
But it seems we do not have the entitlement to download the latest software. (Will figure this out tomorrow)
Looks like the issue is fixed in the latest update.
AnyConnect 4.8 is not working on the FPR1000 series |
Thanks :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2020 09:46 AM
Hi,
I understand you run ASA? What software version? Does it work for some devices and for others not, because it's not clear to me. Is the ASA licensed for AnyConnect?
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2020 02:58 AM
It works for Windows devices (Mac and Linux not tested). (AnyConnect 4.6 and 4.7)
And it work with an ol iPad with an old AnyConnact version. (2.x or 3.x?)
But it does not work for Android and iOS. (latest version from app store; 4.8)
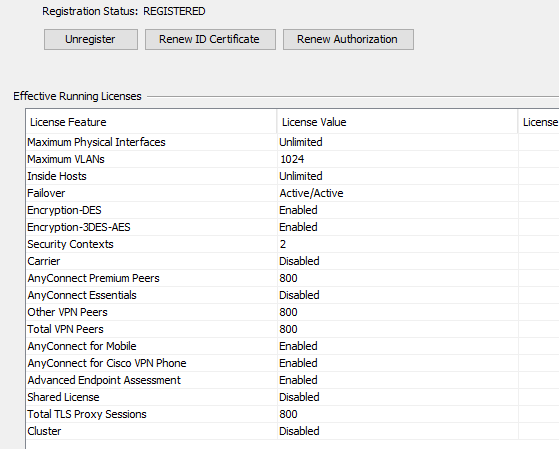
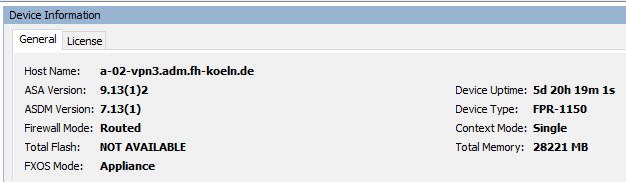
Here are my device info and licensing:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2020 06:08 AM - edited 03-19-2020 06:51 AM
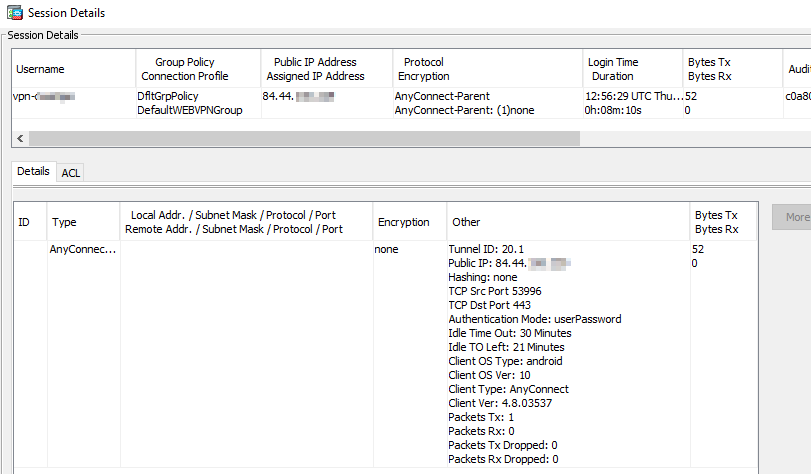
Another strange thing:
After I get the error on my Android device, there is still some kind of vpn session active on the ASA.
It only disconnects, when I try the next login.
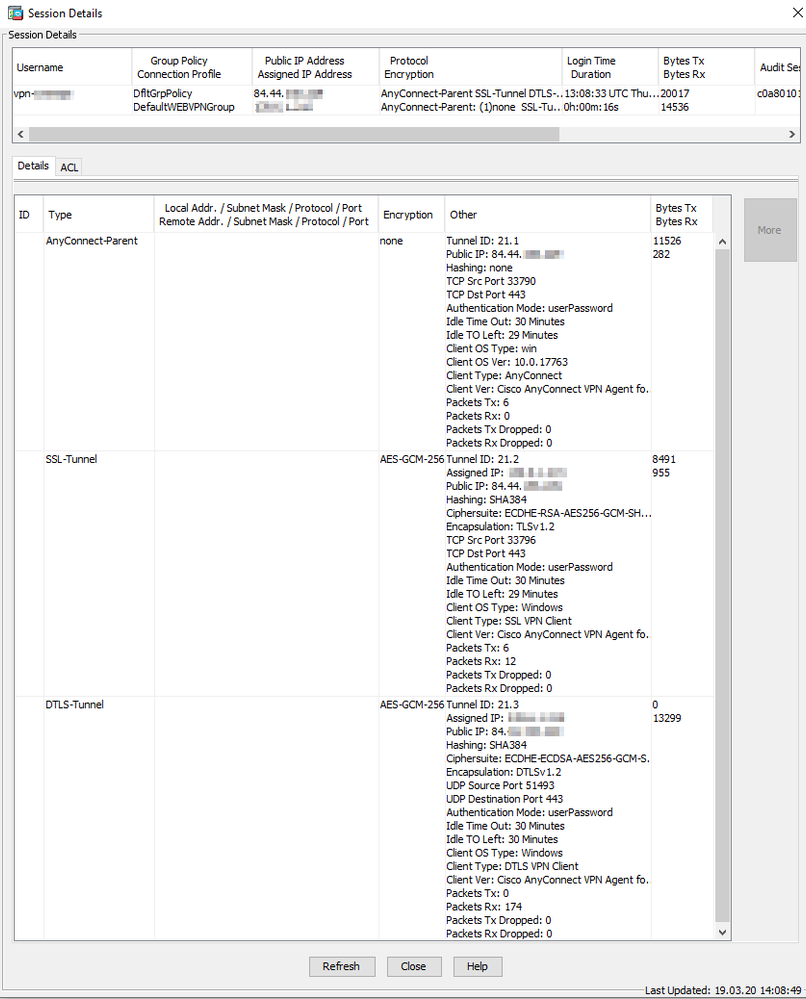
Here is a working connection from Win10:
So it looks like there is a problem with establishing the SSL-Tunnel.
EDIT:
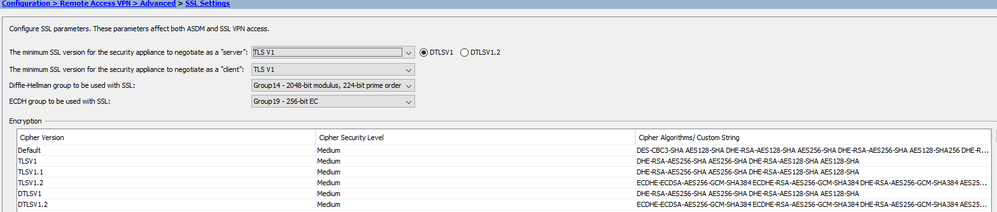
And some some information regarding my configuration.
a-02-vpn3# sh ssl Accept connections using SSLv3 or greater and negotiate to TLSv1 or greater Start connections using TLSv1 and negotiate to TLSv1 or greater SSL DH Group: group14 (2048-bit modulus, 224-bit prime order subgroup, FIPS) SSL ECDH Group: group19 (256-bit EC) SSL trust-points: Self-signed (RSA 2048 bits RSA-SHA256) certificate available Self-signed (EC 256 bits ecdsa-with-SHA256) certificate available Interface management: vpn (RSA 2048 bits RSA-SHA256) Interface redundant: vpn (RSA 2048 bits RSA-SHA256) Certificate authentication is not enabled
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2020 11:57 AM
Hi,
Set "External Control" on client side to "Prompt" or "Enabled", enable VPN Debugging on the client side and post the logs. I would also upgrade the ASA to 9.13.1.7.
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2020 12:41 PM
I checked within ASDM to update the Software and it returned "up to date".
But it seems we do not have the entitlement to download the latest software. (Will figure this out tomorrow)
Looks like the issue is fixed in the latest update.
AnyConnect 4.8 is not working on the FPR1000 series |
Thanks :)