- Cisco Community
- Technology and Support
- Security
- VPN
- ASA5505 Site to Site VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA5505 Site to Site VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2012 01:44 AM
Hi,
i am trying to configure a site to site VPN with one of my remote offices.
I have used the ADSM Wizard to go through the steps, and i have added the necessary access rules.
However, when i try and do a packet tracei get the following error (ad-drop) Flow is denied by configured rule. (see screen shot below)
Any help appreacited.
Thanks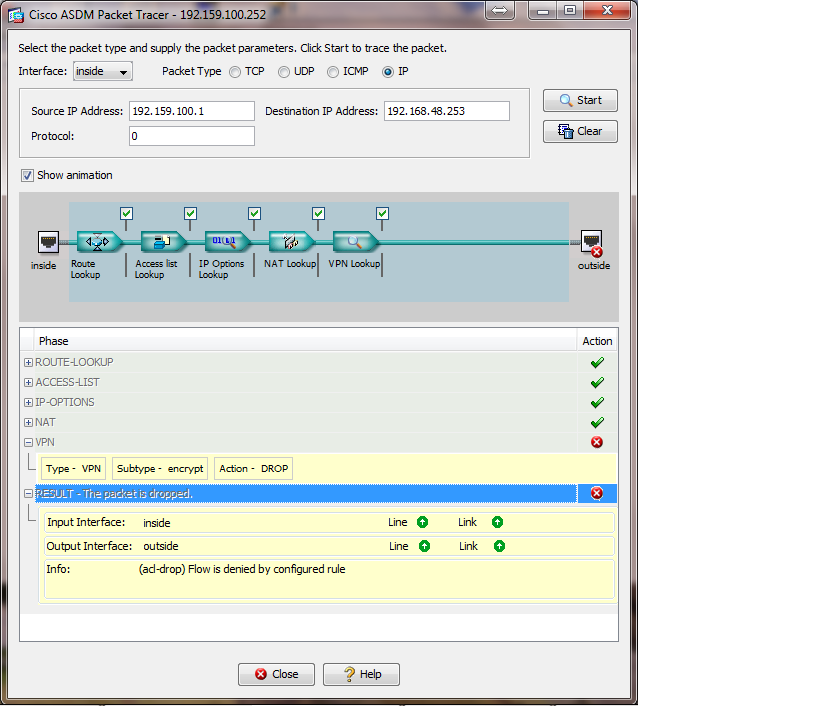
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2012 02:42 AM
You should post full config of both end.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2012 03:32 AM
Local Config:
: Saved
:
ASA Version 8.3(1)
!
hostname Primary
domain-name synlog.co.uk
enable password wN5U1JK95lCIofCc encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
name 10.48.106.0 scanw description scanw
name 10.48.38.0 scap description scap
name 10.48.106.2 NWCMS description SCANW_CMS
name 10.48.106.3 NWDB description SCANW_DB
name 10.48.106.4 NW_BK description SCANW_BK
name 10.48.38.127 PrudhoDB description Prudhoe_DB
name 10.48.38.135 PrudhoeBK description Prudhoe_BK
name 10.48.38.131 PrudhoeCMS description Prudhoe_CMS
name 10.250.37.0 Boston description Boston
name 10.249.14.0 iLondon description iLondon
!
interface Vlan1
nameif inside
security-level 100
ip address 192.159.100.252 255.255.255.0 standby 192.159.100.249
!
interface Vlan2
nameif outside
security-level 0
ip address 212.2.16.213 255.255.255.240 standby 212.2.16.215
!
interface Vlan5
shutdown
nameif dmz
security-level 50
ip address 192.200.200.254 255.255.255.0
!
interface Vlan15
description LAN Failover Interface
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
switchport access vlan 15
!
interface Ethernet0/6
switchport access vlan 5
!
interface Ethernet0/7
!
boot system disk0:/asa831-k8.bin
ftp mode passive
clock timezone GMT/BST 0
clock summer-time GMT/BDT recurring last Sun Mar 1:00 last Sun Oct 2:00
dns domain-lookup outside
dns server-group DefaultDNS
name-server 135.196.0.14
name-server 8.8.8.8
name-server 156.154.70.1
domain-name synlog.co.uk
same-security-traffic permit intra-interface
object network obj-192.159.100.128
subnet 192.159.100.128 255.255.255.224
object network obj-192.159.100.0
subnet 192.159.100.0 255.255.255.0
object network Boston
subnet 10.250.37.0 255.255.255.0
object network iLondon
subnet 10.249.14.0 255.255.255.0
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network Internal_Failover
host 10.0.0.1
object network Internal_Failover_1
host 10.0.0.1
object network Internal_Failover_2
host 10.0.0.2
object network Cisco_FW0
host 192.159.100.252
object network Cisco_FW1
host 192.159.100.249
object network DCS_VPN
subnet 192.168.48.0 255.255.255.0
description DCS VPN
object network NETWORK_OBJ_192.159.100.0_24
subnet 192.159.100.0 255.255.255.0
object network DCS_BK
host 192.168.48.253
description DCS_BK
object network DCS_CMS
host 192.168.48.241
description DCS_CMS
object network DCS_DB
host 192.168.48.254
description DCS_DB
object network 192.168.48.241
host 192.168.48.241
description DCS CMS
object-group network SCA
description SCA S2S VPN
network-object scanw 255.255.255.0
network-object scap 255.255.255.0
object-group protocol DM_INLINE_PROTOCOL_1
protocol-object ip
protocol-object udp
protocol-object tcp
object-group protocol DM_INLINE_PROTOCOL_2
protocol-object ip
protocol-object icmp
protocol-object udp
protocol-object tcp
object-group service DM_INLINE_SERVICE_1
service-object icmp
service-object tcp destination eq ftp
service-object tcp
service-object ip
object-group network SCAVPN
network-object host NWCMS
network-object host NWDB
network-object host NW_BK
network-object host PrudhoDB
network-object host PrudhoeCMS
network-object host PrudhoeBK
object-group service DM_INLINE_SERVICE_2
service-object ip
service-object icmp
service-object tcp-udp destination eq www
service-object tcp destination eq sqlnet
object-group protocol DM_INLINE_PROTOCOL_3
protocol-object ip
protocol-object icmp
protocol-object tcp
object-group service DM_INLINE_SERVICE_3
service-object ip
service-object icmp
service-object tcp
service-object tcp destination eq www
service-object tcp destination eq sqlnet
object-group service DM_INLINE_SERVICE_4
service-object ip
service-object icmp
service-object tcp
service-object tcp destination eq www
service-object tcp destination eq sqlnet
object-group network Internal_Fail
network-object object Internal_Failover_1
network-object object Internal_Failover_2
object-group service DM_INLINE_SERVICE_6
service-object ip
service-object icmp
service-object udp
service-object tcp
service-object tcp-udp destination eq echo
service-object tcp-udp destination eq www
object-group protocol DM_INLINE_PROTOCOL_4
protocol-object ip
protocol-object icmp
protocol-object udp
protocol-object tcp
object-group network DCS_VPN_GROUP
network-object object DCS_BK
network-object object DCS_CMS
network-object object DCS_DB
access-list outside_access_in extended permit icmp any any
access-list outside_access_in extended permit object-group DM_INLINE_PROTOCOL_2 object-group SCAVPN 192.159.100.0 255.255.255.0
access-list outside_access_in extended permit object-group DM_INLINE_PROTOCOL_3 object Boston 192.159.100.0 255.255.255.0
access-list outside_access_in extended permit object-group DM_INLINE_SERVICE_4 object iLondon 192.159.100.0 255.255.255.0
access-list outside_access_in remark DCS VPN IN
access-list outside_access_in extended permit object-group DM_INLINE_SERVICE_6 object DCS_BK 192.159.100.0 255.255.255.0
access-list inside_nat0_outbound extended permit ip any 192.159.100.128 255.255.255.224
access-list inside_nat0_outbound extended permit ip 192.159.100.0 255.255.255.0 object-group SCAVPN
access-list inside_nat0_outbound extended permit ip 192.159.100.0 255.255.255.0 object Boston
access-list inside_nat0_outbound extended permit ip 192.159.100.0 255.255.255.0 object iLondon
access-list inside_nat0_outbound extended permit ip 192.159.100.0 255.255.255.0 192.159.100.128 255.255.255.224
access-list inside_nat0_outbound extended permit ip object iLondon 192.159.100.128 255.255.255.224
access-list inside_nat0_outbound extended permit ip object Boston 192.159.100.128 255.255.255.224
access-list inside_nat0_outbound extended permit ip 192.159.100.0 255.255.255.0 object DCS_VPN
access-list outside_1_cryptomap extended permit ip 192.159.100.0 255.255.255.0 object-group SCAVPN
access-list inside_access_in extended permit object-group DM_INLINE_PROTOCOL_1 192.159.100.0 255.255.255.0 object-group SCAVPN
access-list inside_access_in extended permit object-group DM_INLINE_SERVICE_1 192.159.100.0 255.255.255.0 any
access-list inside_access_in extended permit object-group DM_INLINE_SERVICE_2 192.159.100.0 255.255.255.0 object Boston
access-list inside_access_in extended permit object-group DM_INLINE_SERVICE_3 192.159.100.0 255.255.255.0 object iLondon
access-list inside_access_in remark DCS VPN OUT
access-list inside_access_in extended permit object-group DM_INLINE_PROTOCOL_4 192.159.100.0 255.255.255.0 object DCS_BK
access-list outside_2_cryptomap extended permit ip 192.159.100.0 255.255.255.0 object Boston
access-list outside_3_cryptomap extended permit ip 192.159.100.0 255.255.255.0 object iLondon
access-list synvpn_cisco_splitTunnelAcl standard permit host 10.48.38.131
access-list synvpn_cisco_splitTunnelAcl standard permit host 10.48.38.135
access-list synvpn_cisco_splitTunnelAcl standard permit host 10.48.38.127
access-list synvpn_cisco_splitTunnelAcl standard permit host 10.48.106.3
access-list synvpn_cisco_splitTunnelAcl standard permit host 10.48.106.2
access-list synvpn_cisco_splitTunnelAcl standard permit host 10.48.106.4
access-list synvpn_cisco_splitTunnelAcl standard permit 10.250.37.0 255.255.255.0
access-list synvpn_cisco_splitTunnelAcl standard permit 10.249.14.0 255.255.255.0
access-list synvpn_cisco_splitTunnelAcl standard permit 192.159.100.0 255.255.255.0
access-list DefaultRAGroup_splitTunnelAcl standard permit 10.48.38.0 255.255.255.0
access-list DefaultRAGroup_splitTunnelAcl standard permit 10.48.106.0 255.255.255.0
access-list DefaultRAGroup_splitTunnelAcl standard permit host 10.48.106.3
access-list DefaultRAGroup_splitTunnelAcl standard permit 192.159.100.0 255.255.255.0
access-list DefaultRAGroup_splitTunnelAcl standard permit 10.249.14.0 255.255.255.0
access-list DefaultRAGroup_splitTunnelAcl standard permit 10.250.37.0 255.255.255.0
access-list Synergyvpn_splitTunnelAcl standard permit 10.48.38.0 255.255.255.0
access-list Synergyvpn_splitTunnelAcl standard permit 10.48.106.0 255.255.255.0
access-list Synergyvpn_splitTunnelAcl standard permit 10.249.14.0 255.255.255.0
access-list Synergyvpn_splitTunnelAcl standard permit 10.250.37.0 255.255.255.0
access-list Synergyvpn_splitTunnelAcl standard permit 192.159.100.0 255.255.255.0
access-list outside_4_cryptomap extended permit ip 192.159.100.0 255.255.255.0 object-group DCS_VPN_GROUP
pager lines 24
logging enable
logging asdm-buffer-size 350
logging asdm debugging
logging from-address cisco_asa@synergy-logistics.co.uk
logging recipient-address anish@synergy-logistics.co.uk level errors
logging ftp-bufferwrap
logging ftp-server 192.159.100.187 \log ciscolog *****
mtu inside 1500
mtu outside 1500
mtu dmz 1500
ip local pool VPN_IP_Pool 192.159.100.141-192.159.100.149 mask 255.255.255.0
failover
failover lan unit secondary
failover lan interface FAILOVER Vlan15
failover interface ip FAILOVER 10.0.0.1 255.255.255.0 standby 10.0.0.2
no monitor-interface dmz
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-631.bin
no asdm history enable
arp timeout 14400
nat (inside,any) source static any any destination static obj-192.159.100.128 obj-192.159.100.128
nat (inside,any) source static obj-192.159.100.0 obj-192.159.100.0 destination static SCAVPN SCAVPN
nat (inside,any) source static obj-192.159.100.0 obj-192.159.100.0 destination static Boston Boston
nat (inside,any) source static obj-192.159.100.0 obj-192.159.100.0 destination static iLondon iLondon
nat (inside,any) source static obj-192.159.100.0 obj-192.159.100.0 destination static obj-192.159.100.128 obj-192.159.100.128
nat (inside,any) source static iLondon iLondon destination static obj-192.159.100.128 obj-192.159.100.128
nat (inside,any) source static Boston Boston destination static obj-192.159.100.128 obj-192.159.100.128
nat (inside,any) source static obj-192.159.100.0 obj-192.159.100.0 destination static DCS_VPN_GROUP DCS_VPN_GROUP
!
object network obj_any
nat (inside,outside) dynamic interface
access-group inside_access_in in interface inside
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 212.2.16.211 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-record DfltAccessPolicy
http server enable
http server idle-timeout 10
http 192.159.100.0 255.255.255.0 inside
http 212.2.16.212 255.255.255.255 outside
http 66.236.139.46 255.255.255.255 outside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec transform-set TRANS_ESP_3DES_SHA esp-3des esp-md5-hmac
crypto ipsec transform-set TRANS_ESP_3DES_MD5 esp-3des esp-md5-hmac
crypto ipsec transform-set TRANS_ESP_3DES_MD5 mode transport
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 5 set pfs group1
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 5 set transform-set TRANS_ESP_3DES_MD5 ESP-3DES-MD5 ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 1 match address outside_1_cryptomap
crypto map outside_map 1 set pfs
crypto map outside_map 1 set peer 193.221.47.3
crypto map outside_map 1 set transform-set ESP-3DES-MD5
crypto map outside_map 2 match address outside_2_cryptomap
crypto map outside_map 2 set pfs
crypto map outside_map 2 set peer 64.18.218.2
crypto map outside_map 2 set transform-set ESP-3DES-SHA
crypto map outside_map 3 match address outside_3_cryptomap
crypto map outside_map 3 set peer 89.106.178.2
crypto map outside_map 3 set transform-set ESP-3DES-SHA
crypto map outside_map 4 match address outside_4_cryptomap
crypto map outside_map 4 set pfs
crypto map outside_map 4 set peer 86.188.170.82
crypto map outside_map 4 set transform-set ESP-3DES-SHA TRANS_ESP_3DES_SHA
crypto map outside_map 4 set security-association lifetime seconds 86400
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
telnet 192.159.100.0 255.255.255.0 inside
telnet timeout 5
ssh 66.236.139.46 255.255.255.255 outside
ssh timeout 60
ssh version 2
console timeout 0
dhcpd auto_config outside
!
dhcpd dns 192.159.100.201 192.159.100.204 interface inside
!
threat-detection basic-threat
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
threat-detection statistics tcp-intercept rate-interval 30 burst-rate 400 average-rate 200
ntp server 135.196.68.97 source outside prefer
ntp server 192.159.100.204 source inside prefer
webvpn
enable outside
group-policy DefaultRAGroup internal
group-policy DefaultRAGroup attributes
wins-server value 192.159.100.204 192.159.100.201
dns-server value 192.159.100.204 192.159.100.201
vpn-tunnel-protocol IPSec l2tp-ipsec
default-domain value synlog.co.uk
group-policy DefaultRAGroup_1 internal
group-policy DefaultRAGroup_1 attributes
dns-server value 192.159.100.204 192.159.100.201
vpn-tunnel-protocol IPSec l2tp-ipsec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value DefaultRAGroup_splitTunnelAcl
default-domain value synlog.co.uk
group-policy Synergyvpn internal
group-policy Synergyvpn attributes
wins-server value 192.159.100.204
dns-server value 192.159.100.204 192.159.100.201
vpn-tunnel-protocol IPSec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value DefaultRAGroup_splitTunnelAcl
default-domain value synlog.co.uk
username afell001 password 8VrHWA45uBkqQfOIU8Pjqw== nt-encrypted privilege 0
username afell001 attributes
vpn-group-policy DefaultRAGroup
username amackan password 3YGN2gDYGpVslfyx/ZiNqQ== nt-encrypted privilege 0
username amackan attributes
vpn-group-policy DefaultRAGroup
username anish password 8+idUUQRIw6HW9nYjNetZg== nt-encrypted privilege 0
username anish attributes
vpn-group-policy DefaultRAGroup_1
tunnel-group DefaultRAGroup general-attributes
address-pool VPN_IP_Pool
authorization-server-group LOCAL
default-group-policy DefaultRAGroup_1
tunnel-group DefaultRAGroup ipsec-attributes
pre-shared-key *****
isakmp keepalive disable
tunnel-group DefaultRAGroup ppp-attributes
authentication ms-chap-v2
tunnel-group 193.221.47.3 type ipsec-l2l
tunnel-group 193.221.47.3 ipsec-attributes
pre-shared-key *****
tunnel-group 64.18.218.2 type ipsec-l2l
tunnel-group 64.18.218.2 ipsec-attributes
pre-shared-key *****
tunnel-group 89.106.178.2 type ipsec-l2l
tunnel-group 89.106.178.2 ipsec-attributes
pre-shared-key *****
tunnel-group Synergyvpn type remote-access
tunnel-group Synergyvpn general-attributes
address-pool VPN_IP_Pool
default-group-policy Synergyvpn
tunnel-group Synergyvpn ipsec-attributes
pre-shared-key *****
tunnel-group 86.188.170.82 type ipsec-l2l
tunnel-group 86.188.170.82 ipsec-attributes
pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
smtp-server 192.159.100.199
prompt hostname context
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
hpm topN enable
Cryptochecksum:170b824246b70bf0115c390a5f091f8e
: end
asdm image disk0:/asdm-631.bin
asdm location scap 255.255.255.0 inside
asdm location scanw 255.255.255.0 inside
asdm location PrudhoDB 255.255.255.255 inside
asdm location PrudhoeCMS 255.255.255.255 inside
asdm location PrudhoeBK 255.255.255.255 inside
asdm location NWCMS 255.255.255.255 inside
asdm location NWDB 255.255.255.255 inside
asdm location NW_BK 255.255.255.255 inside
asdm location iLondon 255.255.255.0 inside
asdm location Boston 255.255.255.0 inside
no asdm history enable
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2012 04:12 AM
Lot of cleanup is required very difficult to understand- any specific peer is not working or none ?
no nat statement are not required here the way its configured can be removed.
object group-DM_INLINE_PROTOCOL_4 when you say IP not required to mention ip/tcp/udp.
Your trace should look like - packet-tracer input inside 192.159.100.1 1024 192.168.48.253 80
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2012 05:35 AM
Hi only the vpn to Network DCS is not working. All others are ok. the only other anomoly which i have noticed is that my network objects are displayed differently! and do not show up under ACL. Hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2012 12:24 PM
Anish,
Fix the transform set.
crypto map outside_map 4 set transform-set ESP-3DES-SHA TRANS_ESP_3DES_SHA
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide