- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Community Ask Me Anything- Configuration, Troubleshooting and Best Practices: Anyconnect Remote ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2020
05:28 PM
- last edited on
04-27-2020
09:00 AM
by
Hilda Arteaga
![]()
| Español | Português | Français | Русский | 日本語 | 简体中文 |
This event continues the conversation of our recent Community Ask Me Anything event "Secure Remote Workers".
Here’s your chance to discuss more about the configuration, troubleshooting and best practices for AnyConnect secure mobility client on a Cisco Adaptive Security Appliances (ASA) and Firepower Threat Defense (FTD) and its integration with other Cisco security portfolio devices and technologies like ISE and Duo.
This session provides an opportunity to learn and ask questions about various aspects of AnyConnect implementation (using SSL and Ikev2) including (but not limited to) emergency licenses, configuration, deployment and troubleshooting AnyConnect that provides the security necessary to help ensure that your organization is safe and protected in such critical situation.
To participate in this event, please use the ![]() button below to ask your questions
button below to ask your questions
Ask questions from Monday 6 to Friday, April 17, 2020
 Dinesh Moudgil is a High Touch Technical Support (HTTS) Engineer with the Security team at Cisco. He has been working on Cisco technologies for more than 6 years focusing on Cisco Next Generation Firewalls, Intrusion Prevention Systems, Identity Management and Access Control (AAA) and VPNs. He holds a CCNP, CCDP and CCIE #58881 certifications, and multiple vendors certifications such as ACE, PCNSE and VCP.
Dinesh Moudgil is a High Touch Technical Support (HTTS) Engineer with the Security team at Cisco. He has been working on Cisco technologies for more than 6 years focusing on Cisco Next Generation Firewalls, Intrusion Prevention Systems, Identity Management and Access Control (AAA) and VPNs. He holds a CCNP, CCDP and CCIE #58881 certifications, and multiple vendors certifications such as ACE, PCNSE and VCP. Pulkit Saxena works as High Touch Technical Support (HTTS) Engineer in Security Domain with Cisco bring nearly 7 years of experience in the industry to the team. He has hands on experience with multiple firewalls, different VPN solutions, AAA and Next Generation IPS along with delivering multiple trainings. Pulkit holds certifications from multiple vendors, namely Cisco and Juniper, (CCIE Security and JNCIA).
Pulkit Saxena works as High Touch Technical Support (HTTS) Engineer in Security Domain with Cisco bring nearly 7 years of experience in the industry to the team. He has hands on experience with multiple firewalls, different VPN solutions, AAA and Next Generation IPS along with delivering multiple trainings. Pulkit holds certifications from multiple vendors, namely Cisco and Juniper, (CCIE Security and JNCIA). Jason Grudier is the Technical leader on the VPN TAC team in Raleigh, NC. He has been working for Cisco on the VPN team for six years. Prior to joining the team, he was a network engineer at Labcorp. He works primarily with AnyConnect troubleshooting and configuration across all Cisco platforms as well as DMVPN, GETVPN, Radius, LDAP and Certificate authentications.
Jason Grudier is the Technical leader on the VPN TAC team in Raleigh, NC. He has been working for Cisco on the VPN team for six years. Prior to joining the team, he was a network engineer at Labcorp. He works primarily with AnyConnect troubleshooting and configuration across all Cisco platforms as well as DMVPN, GETVPN, Radius, LDAP and Certificate authentications. Gustavo Medina is a Systems Sales Engineer with the Enterprise Networking Sales team. He has more than 10 years of experience in security and enterprise networking. In his career he has focused on different tasks from technical escalations and partner adoption to the revision of Cisco Certification evaluations. Gustavo holds a CCNA, CCNP CCSI, and a CCIE in security (#51487).
Gustavo Medina is a Systems Sales Engineer with the Enterprise Networking Sales team. He has more than 10 years of experience in security and enterprise networking. In his career he has focused on different tasks from technical escalations and partner adoption to the revision of Cisco Certification evaluations. Gustavo holds a CCNA, CCNP CCSI, and a CCIE in security (#51487).By posting a question on this event you're giving permission to be translated in all languages we have in the community.
**Helpful votes Encourage Participation! **
Please be sure to rate the Answers to Questions
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
Other VPN Topics
- Adaptive Security appliance
- AMA
- Annyconnect integration
- anyconnect
- Anyconnect Ikev2
- anyconnect posture
- anyconnect vpn
- asa
- ask me anything
- cisco
- Cisco Community
- cisco tac
- classic licensing
- coronavirus
- COVID 19
- Dinesh Moudgil
- Dynamic Access Policy
- emergency
- firepower
- firepower forum vent
- FirePOWER Threat Defense
- forum event
- FTD
- Gustavo Medina
- Host scan
- Jason Grudier
- license
- nam
- ogs
- Optimal Gateway Selection
- pandemic
- Pulkit Saxena
- remote access vpn
- secure remote worker
- security
- smart licensing
- ssl vpn
- tnd
- trusted network detection
- vpn
- wfo
- working from home
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 08:07 AM
Hello David,
It's supported and should not be missing. Should be available in the latest ASDM.
If you cannot upgrade right now then you can configure it through CLI as well:
https://www.cisco.com/c/en/us/td/docs/security/asa/asa98/configuration/vpn/asa-98-vpn-config/vpn-params.html
Regards,
Gustavo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 08:48 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 01:16 PM
Hi David,
7.14.1 is the latest: https://software.cisco.com/download/home/283123066/type/280775064/release/7.14.1
From the image you attached you can see the 2nd option: "anyconnect-custom"
But first you need to configure the attribute under webvpn, see the 3 steps below:
https://www.cisco.com/c/en/us/td/docs/security/asa/asa98/configuration/vpn/asa-98-vpn-config/vpn-params.html
Regards,
Gustavo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2020 02:47 AM
Hi Gustavo,
Thanks for that, that solved my issue :)
I have one other question, with Dynamic split tunnelling, can we exclude certain public subnets? Or is it only DNS names? Our customer is trying to break out MS Teams traffic locally, and it seems teams only uses IP addresses and not DNS names.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2020 04:54 AM
As per 4.8 administrator guide :
https://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/anyconnect48/administration/guide/b_AnyConnect_Administrator_Guide_4-8/b_AnyConnect_Administrator_Guide_4-7_chapter_01100.html#concept_fly_15q_tz
It seems this will cater only DNS names, I will check further and revert.
-
Pulkit
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2020 09:28 AM
Glad that one is solved. Dynamic Split is for DNS only but it works together with regular excludespecified.
I replied on this thread that is doing the same optimization you are looking for. There's a MS caveat I mentioned there:
https://community.cisco.com/t5/vpn/anyconnect-split-vpn/m-p/4058772#M271373
Let me know if you have further questions.
-Gustavo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 08:13 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 08:23 AM - edited 04-07-2020 09:19 AM
Hello Marvin,
Here are some key points:
1. Use AnyConnect 4.7.x or higher as we fixed some buffer and HW acceleration issues.
2. Use DTLS v1.2 or IKEv2, as they will result in higher performance. Do *not* use TLS only as a transport protocol, as this will result in decreased/poor performance.
NOTE: DTLS 1.2 support was introduced in ASA versions 9.10.x and above. Previous ASA versions do not support DTLS 1.2. Therefore, and to avoid Bug CSCvp07143  = DTLS 1.2 and AnyConnect oMTU, the following minimum versions of ASA are required:
= DTLS 1.2 and AnyConnect oMTU, the following minimum versions of ASA are required:
- 9.10(1)22 or higher - latest 9.10.x version recommended
- 9.10(2)1 or higher - latest 9.12.x version recommended
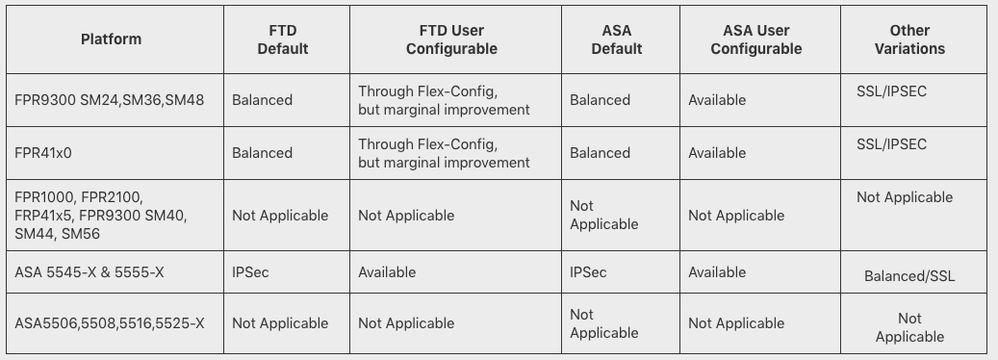
3. Depending on headend hardware in use and/or Customer specific ASA/FPR environments, configuration(s) regarding 'crypto engine accelerator-bias' should be reviewed and/or modified if applicable. Apply the appropriate bias settings that best suits the Customer environment/configuration, taking into consideration the primary transport protocol being used DTLSv1.2 or IKEv2. In your specific case this is not needed as you use a 2100 but use the below table for future reference:
4. Cipher Suite: Ideally, the AES-GCM will provide the best performance results.
5. MTU configuration on the Group Policy: Ideally the higher the better, never exceeding 1406. Suggested value being 1406 (at minimum ‘start’ at 1406, lowering only to suite Customer environment(s)
6. The AnyConnect TunnelOptimizations Custom Attribute MUST BE configured/enabled on ASA/Group Policy:
webvpn anyconnect-custom-attr TunnelOptimizationsEnabled description Tunnel Optimizations Enabled anyconnect-custom-data TunnelOptimizationsEnabled False false anyconnect-custom-data TunnelOptimizationsEnabled True true group-policy <Group Policy Name> attributes anyconnect-custom TunnelOptimizationsEnabled value True
All that being said, I've been able to get 200Mbps from a single client in my lab setup.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 08:57 AM
Thanks @Gustavo Medina that's all helpful.
1. The bug you mentioned was linked to an internal CDETS site but I see it publicly at https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvp07143
2. I believe DTLS 1.2 is not supported for FTD SSL VPN clients until we upgrade to FTD 6.6 (which just came out yesterday). I do see that on the ASAv in question we are using 9.12(3.9) and AnyConnect 4.8.03036. Thus the clients are thus connecting with DTLS 1.2 tunnels and we are seeing somewhat better performance for them.
3. Are the AnyConnect tunnel optimizations supported though Flexconfig on FMC to use with a managed FTD device?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 09:19 AM
Correct. 6.6 introduced the feature to allow configuration of DTLS v1.2 protocol
FDM - REST API Only
FMC GUI configuration support
*Platforms which do not have support from hardware crypto chip are unsupported (meaning 5508 and 5516)
Yes, you can use Flexconfig for these custom-attributes. Similar to how is documented here for dynamic split.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 09:48 AM - edited 04-07-2020 09:50 AM
Thanks - the "TunnelOptimizationsEnabled" bumped up the speed for SSL VPN clients on the ASAv a good bit.
I was also able to deploy via FlexConfig to an FTD 6.4.0.8 device; but it didn't appear to help the speed there - I suspect we are hitting a cap imposed in part by DTLS 1.0.
I couldn't find much documentation on this setting other than a recent TAC article recommending we use it: https://www.cisco.com/c/en/us/td/docs/security/asa/misc/anyconnect-faq/anyconnect-faq.html Is there any other source material I've missed?
By the way, this ENH bug should be marked as fixed with the release of Firepower 6.6: https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvr51516
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2020 12:47 PM
I'll file a DOC bug to include this in the config guides, command reference and Anyconnect Admin guide.
Anyconnect 4.9 will have it enabled by default.
I'll also work on moving CSCvr51516 to the correct state.
Regards,
Gustavo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2020 05:43 AM
Apparently the flexconfig option for FTD is not listed here :
https://www.cisco.com/c/en/us/td/docs/security/asa/misc/anyconnect-faq/anyconnect-faq.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 09:37 AM
my module does not work model cisco sp112
This question is a translation of a post originally created in French by christianbabin98030. It has been translated by Cisco Community to share the inquiry and its solution in different languages.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2020 11:01 AM
This question is unclear. what module is not working with which device. What do they mean by doesn't work?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide