- Cisco Community
- Technology and Support
- Security
- VPN
- Community Ask Me Anything- Configuration, Troubleshooting and Best Practices: AnyConnect Remote Acce...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-03-2020
05:28 PM
- last edited on
04-27-2020
09:00 AM
by
Hilda Arteaga
![]()
| Español | Português | Français | Русский | 日本語 | 简体中文 |
This event continues the conversation of our recent Community Ask Me Anything event "Secure Remote Workers".
Here’s your chance to discuss more about the configuration, troubleshooting and best practices for AnyConnect secure mobility client on a Cisco Adaptive Security Appliances (ASA) and Firepower Threat Defense (FTD) and its integration with other Cisco security portfolio devices and technologies like ISE and Duo.
This session provides an opportunity to learn and ask questions about various aspects of AnyConnect implementation (using SSL and Ikev2) including (but not limited to) emergency licenses, configuration, deployment and troubleshooting AnyConnect that provides the security necessary to help ensure that your organization is safe and protected in such critical situation.
To participate in this event, please use the ![]() button below to ask your questions
button below to ask your questions
Ask questions from Monday 6 to Friday, April 17, 2020
 Dinesh Moudgil is a High Touch Technical Support (HTTS) Engineer with the Security team at Cisco. He has been working on Cisco technologies for more than 6 years focusing on Cisco Next Generation Firewalls, Intrusion Prevention Systems, Identity Management and Access Control (AAA) and VPNs. He holds a CCNP, CCDP and CCIE #58881 certifications, and multiple vendors certifications such as ACE, PCNSE and VCP.
Dinesh Moudgil is a High Touch Technical Support (HTTS) Engineer with the Security team at Cisco. He has been working on Cisco technologies for more than 6 years focusing on Cisco Next Generation Firewalls, Intrusion Prevention Systems, Identity Management and Access Control (AAA) and VPNs. He holds a CCNP, CCDP and CCIE #58881 certifications, and multiple vendors certifications such as ACE, PCNSE and VCP. Pulkit Saxena works as High Touch Technical Support (HTTS) Engineer in Security Domain with Cisco bring nearly 7 years of experience in the industry to the team. He has hands on experience with multiple firewalls, different VPN solutions, AAA and Next Generation IPS along with delivering multiple trainings. Pulkit holds certifications from multiple vendors, namely Cisco and Juniper, (CCIE Security and JNCIA).
Pulkit Saxena works as High Touch Technical Support (HTTS) Engineer in Security Domain with Cisco bring nearly 7 years of experience in the industry to the team. He has hands on experience with multiple firewalls, different VPN solutions, AAA and Next Generation IPS along with delivering multiple trainings. Pulkit holds certifications from multiple vendors, namely Cisco and Juniper, (CCIE Security and JNCIA). Jason Grudier is the Technical leader on the VPN TAC team in Raleigh, NC. He has been working for Cisco on the VPN team for six years. Prior to joining the team, he was a network engineer at Labcorp. He works primarily with AnyConnect troubleshooting and configuration across all Cisco platforms as well as DMVPN, GETVPN, Radius, LDAP and Certificate authentications.
Jason Grudier is the Technical leader on the VPN TAC team in Raleigh, NC. He has been working for Cisco on the VPN team for six years. Prior to joining the team, he was a network engineer at Labcorp. He works primarily with AnyConnect troubleshooting and configuration across all Cisco platforms as well as DMVPN, GETVPN, Radius, LDAP and Certificate authentications. Gustavo Medina is a Systems Sales Engineer with the Enterprise Networking Sales team. He has more than 10 years of experience in security and enterprise networking. In his career he has focused on different tasks from technical escalations and partner adoption to the revision of Cisco Certification evaluations. Gustavo holds a CCNA, CCNP CCSI, and a CCIE in security (#51487).
Gustavo Medina is a Systems Sales Engineer with the Enterprise Networking Sales team. He has more than 10 years of experience in security and enterprise networking. In his career he has focused on different tasks from technical escalations and partner adoption to the revision of Cisco Certification evaluations. Gustavo holds a CCNA, CCNP CCSI, and a CCIE in security (#51487).By posting a question on this event you're giving permission to be translated in all languages we have in the community.
**Helpful votes Encourage Participation! **
Please be sure to rate the Answers to Questions
Solved! Go to Solution.
- Labels:
-
AnyConnect
-
Other VPN Topics
- Adaptive Security appliance
- AMA
- Annyconnect integration
- anyconnect
- Anyconnect Ikev2
- anyconnect posture
- anyconnect vpn
- asa
- ask me anything
- cisco
- Cisco Community
- cisco tac
- classic licensing
- coronavirus
- COVID 19
- Dinesh Moudgil
- Dynamic Access Policy
- emergency
- firepower
- firepower forum vent
- FirePOWER Threat Defense
- forum event
- FTD
- Gustavo Medina
- Host scan
- Jason Grudier
- license
- nam
- ogs
- Optimal Gateway Selection
- pandemic
- Pulkit Saxena
- remote access vpn
- secure remote worker
- security
- smart licensing
- ssl vpn
- tnd
- trusted network detection
- vpn
- wfo
- working from home
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2020 03:15 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2020 04:43 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2020 09:12 AM
My profile does contain the serverlist and hostentry sections for the servers I want to connect to. I was following along this comment (https://community.cisco.com/t5/vpn/community-ask-me-anything-configuration-troubleshooting-and-best/m-p/4063991/highlight/true#M271759) "If you modify the XML profile and push it to the clients along with your OnConnect script to the right location it will work".
We will be using a combo of GPO/MEMCM to push the files along to the clients.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2020 09:47 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2020 02:26 PM
Yes. It has all of the ServerList, HostEntry, HostName, HostAddress, and UserGroup sections...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2020 05:16 PM - edited 04-15-2020 05:22 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2020 05:27 PM
Hi again,
We have a physical FMC2500 and I am evaluating the option to use FTDv in VMware ESX.
I know that with ASAv is necessary to purchase a throughput license, is there a similar requirement for FTDv?
As I could read all what should be required at the minimum in our case is
- FTDv image to deploy
- Hardware requirements in VMware ESX to spin up the image
- Availability on the FMC (no additional license needed since it's hardware FMC2500)
- Anyconnect license available in our smart account for the number of users to connect
Considering we have already ESX hardware available and the FMC and the anyconnect licenses we would purchase anyway, I understand there is no additional costs I am missing, correct?
In case we should then add
- Threat license for IPS and Security intelligence / geolocation
- Malware in case of analysis via AMP of file in transit
- URL in case of URL filtering requirements
Thanks in advance!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2020 03:17 AM
To answer your question, there is no such requirement like a throughput license for FTDv as needed in ASAv.
So yes, what all steps you mentioned, that should be enough to setup FTDv in virtual environment.
Also, in case you need additional features, one you have the specific licenses purchased, you can install them.
-
Pulkit
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2020 03:52 AM - edited 04-16-2020 03:53 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2020 03:56 AM
Thank you Pulkit,
I am looking at the ordering guide for Firepower Threat Defense Virtual and I am a bit confused, I hope you can help.
From your answer I understood that the FTDv does not need a specific license for the Firewall to operate on a Physical FMC as base license is always applied in that case and in our situation only Threat and Anyconnect licenses should be purchased.
Then I saw the following table from the ordering guide :
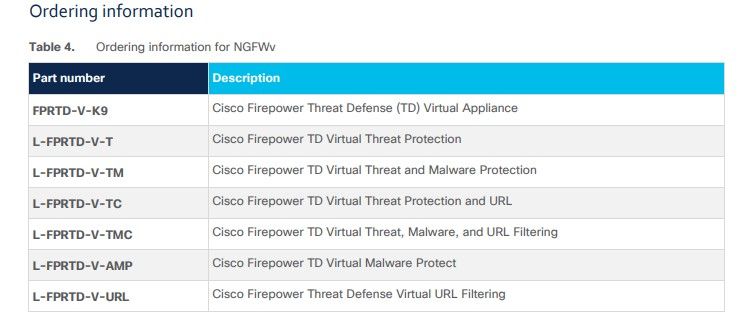
I expected the other way around that the Virtual appliance would have 0 cost (besides Smartnet) and the feature licenses would have a specific cost
Is the FPRTD-V-K9 License required in case we use a physical FMC ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2020 12:51 AM
I would like to join this event please share the registration link
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2020 01:51 AM
Hi Sachin,
The way you posted your current message, in the same way you can post query.
It is an open platform.
The event page is :
The discussion page is :
-
Pulkit
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-16-2020 02:46 PM
Hi,
cisco anyconnect vpn on asa and wants do posture ,
what are the licenses required on both asa and ISE
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2020 01:09 AM
Hi Bluesea2010,
So we want to configure anyconnect ISE posture.
Two main licensing requirements are :
- BASE and APEX license on ISE, out of which BASE must already be there as for each session base license in consumed.
- AnyConnect user license on ASA as per your requirement depending on number of users.
Below link provides information on licenses for ISE :
A few good documents to have basic understanding on configuration and flow :
-
Pulkit
- « Previous
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide