- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Failover IKEV2 route based VPN between ASA and IOS router with dual ISP's
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2020 03:31 PM
Evening All,
I am looking to move away from IKEv1 route based site to site VPN's over to IKEv2. The current setup would be a HA pair of ASA's at the HQ RO2 internet and at the remote sites we would have dual ISP's going to a single IOS router, I am currently using PSK's
At the moment I am struggling on the redundancy side of things for the secondary VPN in that I can only specify 1 identity local address, is there anyway we can specify 2 like we can in a crypto map?
If anyone has set this scenario up before and could point me in the right direction or could send some configuration templates over it would be much appreciated.
Thanks
Solved! Go to Solution.
- Labels:
-
VPN
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2020 05:52 AM
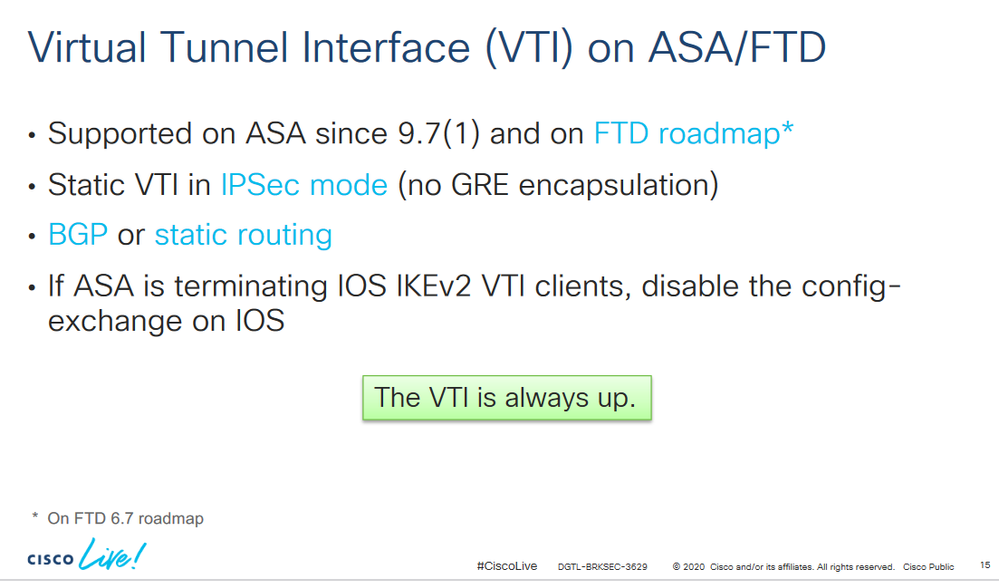
At first glance this looks ok, though I haven't implemented/labbed this scenario myself, with the ASA as the headend.
I previously read that if the headend is an ASA, that config-exchange must be disabled on the IOS routers. This can be configured under the IKEv2 profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2020 01:02 AM
Hi @Aquatera
How is you existing IKEv1 routed based VPN currently setup?
I've not tried your exact scenario and there probably much references on the internet, when using ASA as the headend device. On the router you could define 2 x ikev2 profiles, one for each ISP connection, which references the different local identities. Create 2 ipsec profiles, reference the ikev2 profiles and attach the ipsec profile to separate tunnel interfaces. You'd need 2 tunnel interfaces, tunnel-groups etc on the ASA as-well.
If you used routers' at the headend instead of the ASA's you could use dVTI's which would save a lot of configuration on the ASA - depending on how many spoke's you had.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2020 03:29 AM - edited 11-19-2020 03:33 AM
Hi Rob,
The IKEv1 setup is exactly as you described above. When I use ikev2 and create another ikev2 profile for the second ISP it seems to break the first? If I apply the backup ipsec profile to either tunnel interface the tunnel coomes up, however if I put the ipsec profile on either of the tunnel interfaces it does not work and the tunnel stops down which is strange as removing the backup ikev2 profle & backup ipsec profile the original profile's start to work again. The problem I get if I use a single ikev2 & ipsec profile is that the Tunnels drop every 90 seconds or so complaining of %CRYPTO-4-RECVD_PKT_INV_SPI: decaps: rec'd IPSEC packet has invalid spi for destaddr
Here is the config from the router side
crypto ikev2 proposal PROP-1
encryption aes-cbc-256
prf sha256
integrity sha512
group 5
!
crypto ikev2 proposal PROP-1_BACKUP
encryption aes-cbc-256
prf sha256
integrity sha512
group 5
!
crypto ikev2 policy IKEV2_POLICY
proposal PROP-1
crypto ikev2 policy IKEV2_POLICY_BACKUP
proposal PROP-1_BACKUP
!
crypto ikev2 keyring KEYRING
peer 5.5.5.5
address 5.5.5.5
pre-shared-key local *******
pre-shared-key remote *******
!
crypto ikev2 profile ASA_VTI_PROFILE
match identity remote address 5.5.5.5 255.255.255.255
identity local address 7.7.7.7
authentication remote pre-share
authentication local pre-share
keyring local KEYRING
dpd 10 2 on-demand
crypto ikev2 profile ASA_VTI_PROFILE_BACKUP
match identity remote address 5.5.5.5 255.255.255.255
identity local address 6.6.6.6
authentication remote pre-share
authentication local pre-share
keyring local KEYRING
dpd 10 2 on-demand
no crypto ikev2 http-url cert
!
crypto isakmp invalid-spi-recovery
!
crypto ipsec transform-set TSET esp-aes 256 esp-sha512-hmac
mode tunnel
crypto ipsec profile IPSEC_PROFILE
set transform-set TSET
set ikev2-profile ASA_VTI_PROFILE
!
crypto ipsec profile IPSEC_PROFILE_BACKUP
set transform-set TSET
set ikev2-profile ASA_VTI_PROFILE_BACKUP
!
interface Tunnel1
ip address 15.0.0.2 255.255.255.252
ip tcp adjust-mss 1380
tunnel source Dialer1 (6.6.6.6)
tunnel mode ipsec ipv4
tunnel destination 5.5.5.5
tunnel protection ipsec profile IPSEC_PROFILE_BACKUP
!
interface Tunnel2
ip address 15.0.0.6 255.255.255.252
ip tcp adjust-mss 1380
tunnel source Vlan62 (7.7.7.7)
tunnel mode ipsec ipv4
tunnel destination 5.5.5.5
tunnel protection ipsec profile IPSEC_PROFILE
!
ip route 192.168.6.0 255.255.255.0 Tunnel2 track 1
ip route 0.0.0.0 0.0.0.0 7.7.7.1 track 1
ip route 0.0.0.0 0.0.0.0 Dialer1 10
ip route 192.168.6.0 255.255.255.0 Tunnel1 10
Config from the ASA side
crypto ikev2 policy 5
encryption aes-256
integrity sha512
group 5
prf sha256
lifetime seconds 86400
!
crypto ikev2 enable outside
!
crypto ipsec ikev2 ipsec-proposal TSET
protocol esp encryption aes-256
protocol esp integrity sha-512
!
crypto ipsec profile IPSEC_PROFILE
set ikev2 ipsec-proposal TSET
!
group-policy 7.7.7.7 internal
group-policy 7.7.7.7 attributes
vpn-tunnel-protocol ikev2
!
group-policy 6.6.6.6 internal
group-policy 6.6.6.6 attributes
vpn-tunnel-protocol ikev2
!
tunnel-group 7.7.7.7 type ipsec-l2l
tunnel-group 7.7.7.7 general-attributes
default-group-policy 7.7.7.7
tunnel-group 7.7.7.7 ipsec-attributes
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
!
tunnel-group 6.6.6.6 type ipsec-l2l
tunnel-group 6.6.6.6 general-attributes
default-group-policy 6.6.6.6
tunnel-group 6.6.6.6 ipsec-attributes
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
!
interface Tunnel1
nameif TO-REMOTE_TU1
ip address 15.0.0.1 255.255.255.252
tunnel source interface outside
tunnel destination 6.6.6.6
tunnel mode ipsec ipv4
tunnel protection ipsec profile IPSEC_PROFILE
ASA5506# sh run int tu2
!
interface Tunnel2
nameif TO-REMOTE_TU2
ip address 15.0.0.5 255.255.255.252
tunnel source interface outside
tunnel destination 7.7.7.7
tunnel mode ipsec ipv4
tunnel protection ipsec profile IPSEC_PROFILE
!
route TO-REMOTE_TU2 10.222.111.0 255.255.255.0 15.0.0.6 1 track 1
route TO-REMOTE_TU1 10.222.111.0 255.255.255.0 15.0.0.2 10
With the above configuration tu2 does not come up and shows as up down, tu1 comes up but drops every 90 seconds or so for around 10 seconds. Tunnel 2 should be acting as the primary link.
Any help would be much appreciated guys
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2020 05:52 AM
At first glance this looks ok, though I haven't implemented/labbed this scenario myself, with the ASA as the headend.
I previously read that if the headend is an ASA, that config-exchange must be disabled on the IOS routers. This can be configured under the IKEv2 profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2020 07:44 AM
Rob my friend you are a genius
Thanks for your help with this, much appreciated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2020 07:50 AM
Glad to hear it is working!
This is where I remember that command from, CL presentation BRKSEC-3629.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-19-2020 08:19 AM
Thanks for that Rob, I will have a look through the presentation.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide