- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Inactive IPsec tunnel not coming up for LAN to LAN traffic
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2022 10:36 PM
Hi All,
I'm having an issue with IPSec tunnel which is initiate between CISCO ASA and PaloAlto firewalls.
Tunnel Phase 1 & 2 went up after the configurations and also encapsulated traffic. But after tunnel goes down due to inactivity, we could not bring it back to up-state by sending traffic from Remote LAN to Local LAN. Only after sending a test packet from either sides of the both firewalls only make the tunnel active again. After that Remote LAN to Local LAN connectivity is working. Kindly provide me a solution on this matter.
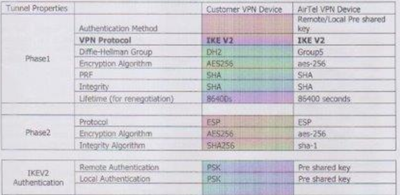
I have attached IPsec attributes for your reference. Left side Palo Alto , Right side ASA.
Solved! Go to Solution.
- Labels:
-
IPSEC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2022 06:45 AM
do you have access to both firewalls or you only adminstrator the ASA firewall?
let assume you the administator of ASA firewall. In order to get this working apply this and monitor, your configuration is not consistant with Palo Alto firewall.
Phase 1 setting are fine in regards to ASA. even though you have defined group 5 2. so this should be fine as if ASA the initiator sending the ikev2 proposals in that case the responder Palo Alto will chose/decide to use the group 2. so on ikev2 phase 1 we are good.
on phase 2 you configuration are mis-match. look you have defined on PaloAlto Integrity as SH256 but for ASA sha-1. your output showin configuration is fine you defined to use the SHA256 but on PaloAlto you mentioned to use the SHA-1. Now if you have access to PaloAlto firewall change the AirTel VPN Device Phase2 Integrity Algorithm SHA256. and If you do not have access to remote firewall (PaloAlto) in that case change your ASA config to
crypto ipsec ikev2 ipsec-proposal NTB
protocol esp encryption aes-256
protocol esp integrity sha-1I do not see PSF configured in remote firewall where as you have configured the PSF on your ASA in phase2. either you configured at psf on remote firewall or you take the command off on your asa.
no crypto map #####-CRYPTO-MAP 2913 set pfs group5
I think what happending is when the key expires the tunnel goes down (or when the tunnel goes slient) could be due to psf no configured on both end. therefore in ordere to bring up the tunnel you have to fire some traffic either end.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2022 01:05 AM
do you config pfs ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2022 04:24 AM
Yes PFS is configured. Do we need to configure same PFS groups in both peers ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2022 04:26 AM - edited 10-29-2022 04:30 AM
the mismatch DH group is issue between vendor,
you can specify one accept by cisco by reject from palo
so try use DH group that both cisco and palo accept it.
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000POf1CAG
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2022 01:44 AM
First of all is this information provided correct ? since oneside you see DH2 and other side DH5, this need to be corrected.
Also sha256 vs sha1 on Phase2
What is your config look like? do you have keepalive configured ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2022 04:22 AM
Dear @balaji.bandi FYR,
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ipsec ikev2 ipsec-proposal NTB
protocol esp encryption aes-256
protocol esp integrity sha-256
**************************************************************
tunnel-group #.#.#.# type ipsec-l2l
tunnel-group #.#.#.# ipsec-attributes
ikev2 remote-authentication pre-shared-key ####
ikev2 local-authentication pre-shared-key ####
ikev2 remote-authentication pre-shared-key #####
ikev2 local-authentication pre-shared-key #####
crypto map #####-CRYPTO-MAP 2913 match address ###_VPN
crypto map #####-CRYPTO-MAP 2913 set peer #.#.#.#
crypto map #####-CRYPTO-MAP 2913 set pfs group5
crypto map #####-CRYPTO-MAP 2913 set ikev2 ipsec-proposal NTB
crypto map #####-CRYPTO-MAP 2913 set security-association lifetime seconds 86400
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2022 06:45 AM
do you have access to both firewalls or you only adminstrator the ASA firewall?
let assume you the administator of ASA firewall. In order to get this working apply this and monitor, your configuration is not consistant with Palo Alto firewall.
Phase 1 setting are fine in regards to ASA. even though you have defined group 5 2. so this should be fine as if ASA the initiator sending the ikev2 proposals in that case the responder Palo Alto will chose/decide to use the group 2. so on ikev2 phase 1 we are good.
on phase 2 you configuration are mis-match. look you have defined on PaloAlto Integrity as SH256 but for ASA sha-1. your output showin configuration is fine you defined to use the SHA256 but on PaloAlto you mentioned to use the SHA-1. Now if you have access to PaloAlto firewall change the AirTel VPN Device Phase2 Integrity Algorithm SHA256. and If you do not have access to remote firewall (PaloAlto) in that case change your ASA config to
crypto ipsec ikev2 ipsec-proposal NTB
protocol esp encryption aes-256
protocol esp integrity sha-1I do not see PSF configured in remote firewall where as you have configured the PSF on your ASA in phase2. either you configured at psf on remote firewall or you take the command off on your asa.
no crypto map #####-CRYPTO-MAP 2913 set pfs group5
I think what happending is when the key expires the tunnel goes down (or when the tunnel goes slient) could be due to psf no configured on both end. therefore in ordere to bring up the tunnel you have to fire some traffic either end.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2022 09:25 AM
Hi @Sheraz.Salim thank you for your valuable answer. I do not have administrator access to Palo alto and i will do the changes that you have provided from ASA end and get back to you with the results.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2022 01:08 PM
something I dont get and need more clarification
the proposal can config or router can use default proposal, which in this particular case the default is same as we enter manually.
the Q is, as I know if one proposal reject the router will not give up, but it will try use other proposal, if not config then it will use default, so when the router use default proposal and when not use it ??
>>>The default proposal is a collection of commonly used algorithms which are as follows:
encryption aes-cbc-128 3des integrity sha1 md5 group 5 2
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide