- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Problem the TX automatically go to zero in vpn between 2 firewall cisco
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Problem the TX automatically go to zero in vpn between 2 firewall cisco
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2019 10:45 PM - edited 03-12-2019 03:30 AM
Hello everyone,
I have 2 site and connected vpn by used firewall cisco, And have the problem every week repeated (TX go to zero), And I attached photo below:
THANKS
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2019 12:29 AM
Hi,
Check the below things:
As you said VPN will work fine after "when i logout connection between the 2 site" It is looking that there is timing mismatch at both ends. Verify Phase 1 and Phase 2 Timers and DPD also.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2019 09:59 PM
I'm edited to my posted and the new edited was
"But the solve are temporarily resolved because after one week the problem "tx=0" replay again so in this time i go to vpn in one site and make logout and try to connect in new session again and the vpn between them will work as fine but the solve are temporarily resolved, How can i solve without any problem, Any help"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2019 10:20 PM
I checked the 2 firewall and the result show below:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2019 11:00 PM
Hi,
The Keepalives seems correct. What about the Phase1 and Phase2 timers?
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-13-2019 03:41 AM - edited 03-13-2019 03:41 AM
In below the result:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2019 02:14 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2019 12:35 AM
Any help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2019 02:06 AM
Share output:
show crypto isa sa detail
show crypto ipsec sa
show vpn-sessiondb xxxx
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2019 10:29 PM - edited 03-24-2019 10:34 PM
Dear Mr.Deepak Kumar,
I apologize for the delay,
This is the result between 2 firewall between 2 branches.
10.10.53.30
TT-HQ-VPN-1# show crypto isa sa detail
IKEv2 SAs:
Session-id:4360, Status:UP-ACTIVE, IKE count:1, CHILD count:5
Tunnel-id Local Remote Status Role
1690209953 10.10.53.30/500 10.10.53.12/500 READY RESPONDER
Encr: AES-CBC, keysize: 256, Hash: SHA96, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/18725 sec
Session-id: 4360
Status Description: Negotiation done
Local spi: 8CDB085FB8C17C33 Remote spi: C3D059EA0AB31A21
Local id: 10.10.53.30
Remote id: 10.10.53.12
Local req mess id: 1869 Remote req mess id: 1818
Local next mess id: 1869 Remote next mess id: 1818
Local req queued: 1869 Remote req queued: 1818
Local window: 1 Remote window: 1
DPD configured for 10 seconds, retry 2
NAT-T is not detected
IKEv2 Fragmentation Configured MTU: 576 bytes, Overhead: 28 bytes, Effective MTU: 548 bytes
Child sa: local selector 192.168.1.170/0 - 192.168.1.170/65535
remote selector 192.168.114.0/0 - 192.168.114.255/65535
ESP spi in/out: 0x91285b9/0x1eeee35c
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA96
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
Child sa: local selector 192.168.128.0/0 - 192.168.128.255/65535
remote selector 192.168.114.0/0 - 192.168.114.255/65535
ESP spi in/out: 0xb258f5d9/0x97cfae53
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA96
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
Child sa: local selector 192.168.1.22/0 - 192.168.1.22/65535
remote selector 192.168.114.0/0 - 192.168.114.255/65535
ESP spi in/out: 0x509ae514/0x779af8ac
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA96
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
Child sa: local selector 192.168.1.2/0 - 192.168.1.2/65535
remote selector 192.168.114.0/0 - 192.168.114.255/65535
ESP spi in/out: 0x551d612c/0xdb1aa71
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA96
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
Child sa: local selector 192.168.12.0/0 - 192.168.12.255/65535
remote selector 192.168.114.0/0 - 192.168.114.255/65535
ESP spi in/out: 0x20cd9ddb/0x9fc4e929
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA96
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
TT-HQ-VPN-1#
-----------------------------------------------------------------------------
TT-HQ-VPN-1# show crypto ipsec sa
Crypto map tag: Scop-Intra_map, seq num: 2, local addr: 10.10.53.30
access-list ScopeSky-Intranet_cryptomap extended permit ip host 192.168.1.2 192.168.114.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.1.2/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (192.168.114.0/255.255.255.0/0/0)
current_peer: 10.10.53.12
#pkts encaps: 4637, #pkts encrypt: 4637, #pkts digest: 4637
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 4637, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.10.53.30/500, remote crypto endpt.: 10.10.53.12/500
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 0DB1AA71
current inbound spi : 551D612C
inbound esp sas:
spi: 0x551D612C (1427988780)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 143048704, crypto-map: Scop-Intra_map
sa timing: remaining key lifetime (kB/sec): (4055040/9974)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
outbound esp sas:
spi: 0x0DB1AA71 (229747313)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 143048704, crypto-map: Scop-Intra_map
sa timing: remaining key lifetime (kB/sec): (3916433/9974)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: Scop-Intra_map, seq num: 2, local addr: 10.10.53.30
access-list ScopeSky-Intranet_cryptomap extended permit ip host 192.168.1.22 192.168.114.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.1.22/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (192.168.114.0/255.255.255.0/0/0)
current_peer: 10.10.53.12
#pkts encaps: 3219, #pkts encrypt: 3219, #pkts digest: 3219
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 3219, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.10.53.30/500, remote crypto endpt.: 10.10.53.12/500
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 779AF8AC
current inbound spi : 509AE514
inbound esp sas:
spi: 0x509AE514 (1352328468)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 143048704, crypto-map: Scop-Intra_map
sa timing: remaining key lifetime (kB/sec): (4055040/9973)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
outbound esp sas:
spi: 0x779AF8AC (2006644908)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 143048704, crypto-map: Scop-Intra_map
sa timing: remaining key lifetime (kB/sec): (4100867/9973)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: Scop-Intra_map, seq num: 2, local addr: 10.10.53.30
access-list ScopeSky-Intranet_cryptomap extended permit ip host 192.168.1.170 192.168.114.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.1.170/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (192.168.114.0/255.255.255.0/0/0)
current_peer: 10.10.53.12
#pkts encaps: 1566, #pkts encrypt: 1566, #pkts digest: 1566
#pkts decaps: 1589, #pkts decrypt: 1589, #pkts verify: 1589
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 1566, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.10.53.30/500, remote crypto endpt.: 10.10.53.12/500
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 1EEEE35C
current inbound spi : 091285B9
inbound esp sas:
spi: 0x091285B9 (152208825)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 143048704, crypto-map: Scop-Intra_map
sa timing: remaining key lifetime (kB/sec): (4285346/9996)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0x1EEEE35C (518972252)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 143048704, crypto-map: Scop-Intra_map
sa timing: remaining key lifetime (kB/sec): (4147107/9996)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: Scop-Intra_map, seq num: 2, local addr: 10.10.53.30
access-list ScopeSky-Intranet_cryptomap extended permit ip 192.168.12.0 255.255.255.0 192.168.114.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.12.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.114.0/255.255.255.0/0/0)
current_peer: 10.10.53.12
#pkts encaps: 34323, #pkts encrypt: 34323, #pkts digest: 34323
#pkts decaps: 37225, #pkts decrypt: 37225, #pkts verify: 37225
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 34323, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.10.53.30/500, remote crypto endpt.: 10.10.53.12/500
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 9FC4E929
current inbound spi : 20CD9DDB
inbound esp sas:
spi: 0x20CD9DDB (550346203)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 143048704, crypto-map: Scop-Intra_map
sa timing: remaining key lifetime (kB/sec): (4309864/9967)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFFFEFF
outbound esp sas:
spi: 0x9FC4E929 (2680482089)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 143048704, crypto-map: Scop-Intra_map
sa timing: remaining key lifetime (kB/sec): (4092690/9967)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: Scop-Intra_map, seq num: 2, local addr: 10.10.53.30
access-list ScopeSky-Intranet_cryptomap extended permit ip 192.168.128.0 255.255.255.0 192.168.114.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.128.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.114.0/255.255.255.0/0/0)
current_peer: 10.10.53.12
#pkts encaps: 1255, #pkts encrypt: 1255, #pkts digest: 1255
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 1255, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.10.53.30/500, remote crypto endpt.: 10.10.53.12/500
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 97CFAE53
current inbound spi : B258F5D9
inbound esp sas:
spi: 0xB258F5D9 (2992174553)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 143048704, crypto-map: Scop-Intra_map
sa timing: remaining key lifetime (kB/sec): (4285440/9971)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
outbound esp sas:
spi: 0x97CFAE53 (2546970195)
SA State: active
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 143048704, crypto-map: Scop-Intra_map
sa timing: remaining key lifetime (kB/sec): (4147136/9971)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
------------------------------------------------------------------------------------------
TT-HQ-VPN-1# show vpn-sessiondb
---------------------------------------------------------------------------
VPN Session Summary
---------------------------------------------------------------------------
Active : Cumulative : Peak Concur : Inactive
----------------------------------------------
Site-to-Site VPN : 10 : 4787 : 15
IKEv2 IPsec : 7 : 4364 : 12
IKEv1 IPsec : 3 : 423 : 4
---------------------------------------------------------------------------
Total Active and Inactive : 10 Total Cumulative : 4787
Device Total VPN Capacity : 750
Device Load : 1%
---------------------------------------------------------------------------
---------------------------------------------------------------------------
Tunnels Summary
---------------------------------------------------------------------------
Active : Cumulative : Peak Concurrent
----------------------------------------------
IKEv1 : 3 : 423 : 4
IKEv2 : 7 : 4364 : 12
IPsec : 45 : 20849 : 79
---------------------------------------------------------------------------
Totals : 55 : 25636
---------------------------------------------------------------------------
TT-HQ-VPN-1#
----------------------------------------------------------------------------------
TT-HQ-VPN-1# show vpn-sessiondb l2l
Connection : 10.10.53.12
Index : 8598 IP Addr : 10.10.53.12
Protocol : IKEv2 IPsec
Encryption : IKEv2: (1)AES256 IPsec: (5)AES256
Hashing : IKEv2: (1)SHA1 IPsec: (5)SHA1
Bytes Tx : 108875 Bytes Rx : 307480
Login Time : 07:40:02 AST Mon Mar 25 2019
Duration : 0h:01m:23s
TT-HQ-VPN-1#
TT-HQ-VPN-1# show vpn-sessiondb summary
---------------------------------------------------------------------------
VPN Session Summary
---------------------------------------------------------------------------
Active : Cumulative : Peak Concur : Inactive
----------------------------------------------
Site-to-Site VPN : 10 : 4787 : 15
IKEv2 IPsec : 7 : 4364 : 12
IKEv1 IPsec : 3 : 423 : 4
---------------------------------------------------------------------------
Total Active and Inactive : 10 Total Cumulative : 4787
Device Total VPN Capacity : 750
Device Load : 1%
---------------------------------------------------------------------------
10.10.53.12
Ha-Branch# show crypto isa sa detail
There are no IKEv1 SAs
IKEv2 SAs:
Session-id:66, Status:UP-ACTIVE, IKE count:1, CHILD count:5
Tunnel-id Local Remote Status Role
2615697595 10.10.53.12/500 10.10.53.30/500 READY INITIATOR
Encr: AES-CBC, keysize: 256, Hash: SHA96, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/18510 sec
Session-id: 66
Status Description: Negotiation done
Local spi: C3D059EA0AB31A21 Remote spi: 8CDB085FB8C17C33
Local id: 10.10.53.12
Remote id: 10.10.53.30
Local req mess id: 1797 Remote req mess id: 1847
Local next mess id: 1797 Remote next mess id: 1847
Local req queued: 1797 Remote req queued: 1847
Local window: 1 Remote window: 1
DPD configured for 10 seconds, retry 2
NAT-T is not detected
Child sa: local selector 192.168.114.0/0 - 192.168.114.255/65535
remote selector 192.168.1.170/0 - 192.168.1.170/65535
ESP spi in/out: 0x1eeee35c/0x91285b9
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA96
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
Child sa: local selector 192.168.114.0/0 - 192.168.114.255/65535
remote selector 192.168.128.0/0 - 192.168.128.255/65535
ESP spi in/out: 0x97cfae53/0xb258f5d9
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA96
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
Child sa: local selector 192.168.114.0/0 - 192.168.114.255/65535
remote selector 192.168.1.22/0 - 192.168.1.22/65535
ESP spi in/out: 0x779af8ac/0x509ae514
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA96
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
Child sa: local selector 192.168.114.0/0 - 192.168.114.255/65535
remote selector 192.168.1.2/0 - 192.168.1.2/65535
ESP spi in/out: 0xdb1aa71/0x551d612c
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA96
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
Child sa: local selector 192.168.114.0/0 - 192.168.114.255/65535
remote selector 192.168.12.0/0 - 192.168.12.255/65535
ESP spi in/out: 0x9fc4e929/0x20cd9ddb
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA96
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
Ha-Branch#
----------------------------------------------------------------------------------
Ha-Branch# show crypto ipsec sa
interface: ScopeSKY
Crypto map tag: ScopeSKY_map, seq num: 2, local addr: 10.10.53.12
access-list ScopeSKY_cryptomap extended permit ip 192.168.114.0 255.255.255.0 host 192.168.1.170
local ident (addr/mask/prot/port): (192.168.114.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.1.170/255.255.255.255/0/0)
current_peer: 10.10.53.30
#pkts encaps: 1575, #pkts encrypt: 1575, #pkts digest: 1575
#pkts decaps: 1529, #pkts decrypt: 1529, #pkts verify: 1529
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 1575, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.10.53.12/500, remote crypto endpt.: 10.10.53.30/500
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 091285B9
current inbound spi : 1EEEE35C
inbound esp sas:
spi: 0x1EEEE35C (518972252)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 1822720, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (3916710/10270)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0x091285B9 (152208825)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 1822720, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (4239267/10270)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: ScopeSKY_map, seq num: 2, local addr: 10.10.53.12
access-list ScopeSKY_cryptomap extended permit ip 192.168.114.0 255.255.255.0 192.168.12.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.114.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.12.0/255.255.255.0/0/0)
current_peer: 10.10.53.30
#pkts encaps: 37108, #pkts encrypt: 37108, #pkts digest: 37108
#pkts decaps: 33783, #pkts decrypt: 33783, #pkts verify: 33783
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 37108, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.10.53.12/500, remote crypto endpt.: 10.10.53.30/500
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 20CD9DDB
current inbound spi : 9FC4E929
inbound esp sas:
spi: 0x9FC4E929 (2680482089)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 1822720, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (4184980/10243)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0x20CD9DDB (550346203)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 1822720, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (4217664/10242)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: ScopeSKY_map, seq num: 2, local addr: 10.10.53.12
access-list ScopeSKY_cryptomap extended permit ip 192.168.114.0 255.255.255.0 host 192.168.1.2
local ident (addr/mask/prot/port): (192.168.114.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.1.2/255.255.255.255/0/0)
current_peer: 10.10.53.30
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 4510, #pkts decrypt: 4511, #pkts verify: 4511
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.10.53.12/500, remote crypto endpt.: 10.10.53.30/500
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 551D612C
current inbound spi : 0DB1AA71
inbound esp sas:
spi: 0x0DB1AA71 (229747313)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 1822720, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (4100763/10245)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0x551D612C (1427988780)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 1822720, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (3962880/10244)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: ScopeSKY_map, seq num: 2, local addr: 10.10.53.12
access-list ScopeSKY_cryptomap extended permit ip 192.168.114.0 255.255.255.0 host 192.168.1.22
local ident (addr/mask/prot/port): (192.168.114.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.1.22/255.255.255.255/0/0)
current_peer: 10.10.53.30
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 3127, #pkts decrypt: 3127, #pkts verify: 3127
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.10.53.12/500, remote crypto endpt.: 10.10.53.30/500
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 509AE514
current inbound spi : 779AF8AC
inbound esp sas:
spi: 0x779AF8AC (2006644908)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 1822720, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (4193034/10244)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0x509AE514 (1352328468)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 1822720, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (3962880/10243)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: ScopeSKY_map, seq num: 2, local addr: 10.10.53.12
access-list ScopeSKY_cryptomap extended permit ip 192.168.114.0 255.255.255.0 192.168.128.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.114.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.128.0/255.255.255.0/0/0)
current_peer: 10.10.53.30
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 1228, #pkts decrypt: 1228, #pkts verify: 1228
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.10.53.12/500, remote crypto endpt.: 10.10.53.30/500
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: B258F5D9
current inbound spi : 97CFAE53
inbound esp sas:
spi: 0x97CFAE53 (2546970195)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 1822720, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (4008897/10245)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0xFBFFFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0xB258F5D9 (2992174553)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 5, IKEv2, }
slot: 0, conn_id: 1822720, crypto-map: ScopeSKY_map
sa timing: remaining key lifetime (kB/sec): (4239360/10244)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Ha-Branch#
------------------------------------------------------------------------------------
Ha-Branch# show vpn-sessiondb
---------------------------------------------------------------------------
VPN Session Summary
---------------------------------------------------------------------------
Active : Cumulative : Peak Concur : Inactive
----------------------------------------------
Site-to-Site VPN : 2 : 67 : 3
IKEv2 IPsec : 2 : 67 : 3
---------------------------------------------------------------------------
Total Active and Inactive : 2 Total Cumulative : 67
Device Total VPN Capacity : 25
Device Load : 8%
---------------------------------------------------------------------------
---------------------------------------------------------------------------
Tunnels Summary
---------------------------------------------------------------------------
Active : Cumulative : Peak Concurrent
----------------------------------------------
IKEv2 : 2 : 67 : 3
IPsec : 8 : 238 : 10
---------------------------------------------------------------------------
Totals : 10 : 305
---------------------------------------------------------------------------
Ha-Branch# show vpn-sessiondb ?
anyconnect AnyConnect sessions
detail Show detailed output
email-proxy Email-Proxy sessions
failover Failover IPsec sessions
full Output formatted for data management programs
index Index of session
l2l IPsec LAN-to-LAN sessions
license-summary Show VPN License summary
ospfv3 OSPFv3 IPsec sessions
ra-ikev1-ipsec IKEv1 IPsec/L2TP-IPsec Remote Access sessions
ratio Show VPN Session protocol or encryption ratios
summary Show VPN Session summary
vpn-lb VPN Load Balancing Mgmt sessions
webvpn WebVPN sessions
| Output modifiers
<cr>
Ha-Branch# show vpn-sessiondb s
Ha-Branch# show vpn-sessiondb summary
---------------------------------------------------------------------------
VPN Session Summary
---------------------------------------------------------------------------
Active : Cumulative : Peak Concur : Inactive
----------------------------------------------
Site-to-Site VPN : 2 : 67 : 3
IKEv2 IPsec : 2 : 67 : 3
---------------------------------------------------------------------------
Total Active and Inactive : 2 Total Cumulative : 67
Device Total VPN Capacity : 25
Device Load : 8%
---------------------------------------------------------------------------
Ha-Branch# show vpn-sessiondb l
Ha-Branch# show vpn-sessiondb l2
Ha-Branch# show vpn-sessiondb l2l
Session Type: LAN-to-LAN
Connection : 10.10.53.30
Index : 445 IP Addr : 10.10.53.30
Protocol : IKEv2 IPsec
Encryption : IKEv2: (1)AES256 IPsec: (5)AES256
Hashing : IKEv2: (1)SHA1 IPsec: (5)SHA1
Bytes Tx : 22329705 Bytes Rx : 9290454
Login Time : 02:15:46 AST Mon Mar 25 2019
Duration : 5h:10m:55s
C
Ha-Branch#
---------------------------------------------------------------------------------------------------
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-25-2019 10:47 PM
Hi,
I didn't found any mismatch in the configuration. Please disable the keeplive on the remote site.
If you will face the issue then please share debug output.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-26-2019 12:14 AM
Thank you for your replay,
In this time i'm applied the change in TX site and set to "keep alive disable", After that i'm waiting if any issue back again and i will capture the debug output to you, (Correct me if i wrong),
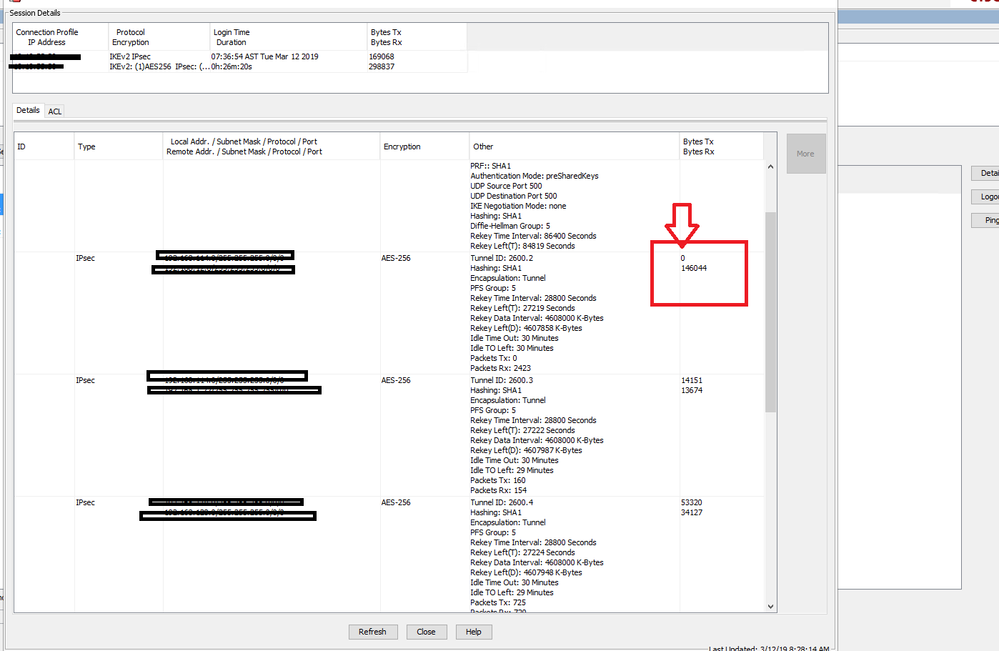
I will show you with photo below and in this ASA was TX site because no TX packet but we have RX packet, We have issue in TX site with 10.10.53.12 (TX site), And the 10.10.53.30 (RX site).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2019 02:32 AM
Any update from you to me for last my replay?
THANKS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2019 08:11 AM
Whats your ASA version? There were multiple bugs in the earlier 9.x versions where the ASA would just stop encrypting for certain SA's. The only way to recover from this is a reload. I recall the problem was stale entries on the SA Database. Can you reload the faulty ASA during a window to check this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2019 08:12 AM
Bugs:
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCup37416/?rfs=iqvred
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvb29688/?rfs=iqvred
Looks to be fixed in 9.7 and above.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide






